Answered step by step
Verified Expert Solution
Question
1 Approved Answer
I need help with making up the firewall policies for this company Instructions for this assignment: Phase 1 (30 points) Explore and research the operations
I need help with making up the firewall policies for this company
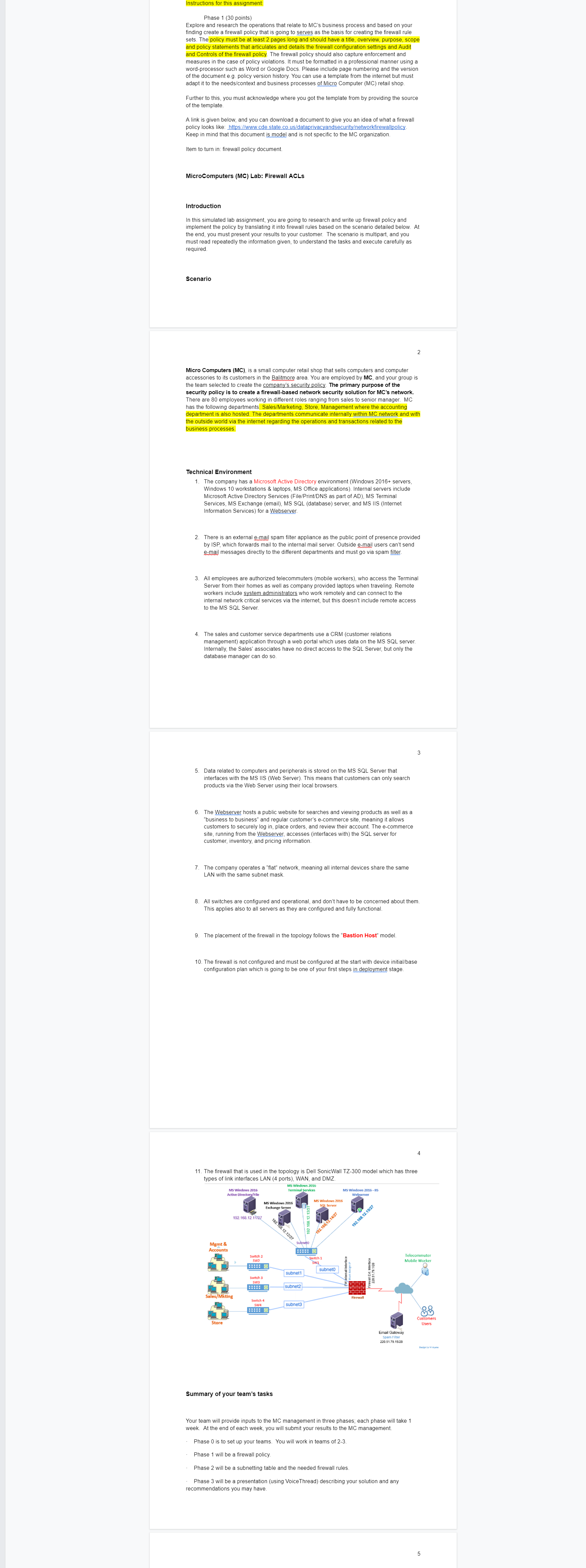
Instructions for this assignment: Phase 1 (30 points) Explore and research the operations that relate to MC's business process and based on your finding create a firewall policy that is going to serves as the basis for creating the firewall rule sets. The policy must be at least 2 pages long and should have a title, overview, purpose, scope and policy statements that articulates and details the firewall configuration settings and Audit and Controls of the firewall policy. The firewall policy should also capture enforcement and measures in the case of policy violations. It must be formatted in a professional manner using a word-processor such as Word or Google Docs. Please include page numbering and the version of the document e.g. policy version history. You can use a template from the internet but must adapt it to the needs/context and business processes of Micro Computer (MC) retail shop. Further to this, you must acknowledge where you got the template from by providing the source of the template. A link is given below, and you can download a document to give you an idea of what a firewall policy looks like: https://www.cde.state.co.us/dataprivacyandsecurity/networkfirewallpolicy. Keep in mind that this document is model and is not specific to the MC organization. Item to turn in: firewall policy document. MicroComputers (MC) Lab: Firewall ACLs Introduction In this simulated lab assignment, you are going to research and write up firewall policy and implement the policy by translating it into firewall rules based on the scenario detailed below. At the end, you must present your results to your customer. The scenario is multipart, and you must read repeatedly the information given, to understand the tasks and execute carefully as required. Scenario Micro Computers (MC), is a small computer retail shop that sells computers and computer accessories to its customers in the Balitmore area. You are employed by MC, and your group is the team selected to create the company's security policy. The primary purpose of the security policy is to create a firewall-based network security solution for MC's network. There are 80 employees working in different roles ranging from sales to senior manager. MC has the following departments: Sales/Marketing, Store, Management where the accounting department is also hosted. The departments communicate internally within MC network and with the outside world via the internet regarding the operations and transactions related to the business processes. Technical Environment 1. The company has a Microsoft Active Directory environment (Windows 2016+ servers, Windows 10 workstations & laptops, MS Office applications). Internal servers include Microsoft Active Directory Services (File/Print/DNS as part of AD), MS Terminal Services, MS Exchange (email), MS SQL (database) server, and MS IIS (Internet Information Services) for a Webserver. 2. There is an external e-mail spam filter appliance as the public point of presence provided by ISP, which forwards mail to the internal mail server. Outside e-mail users can't send e-mail messages directly to the different departments and must go via spam filter. 3. All employees are authorized telecommuters (mobile workers), who access the Terminal Server from their homes as well as company provided laptops when traveling. Remote workers include system administrators who work remotely and can connect to the internal network critical services via the internet, but this doesn't include remote access to the MS SQL Server. 4. The sales and customer service departments use a CRM (customer relations management) application through a web portal which uses data on the MS SQL server. Internally, the Sales' associates have no direct access to the SQL Server, but only the database manager can do so. 5. Data related to computers and peripherals is stored on the MS SQL Server that interfaces with the MS IIS (Web Server). This means that customers can only search products via the Web Server using their local browsers. 6. The Webserver hosts a public website for searches and viewing products as well as a "business to business" and regular customer's e-commerce site, meaning it allows customers to securely log in, place orders, and review their account. The e-commerce site, running from the Webserver, accesses (interfaces with) the SQL server for customer, inventory, and pricing information. 7. The company operates a "flat" network, meaning all internal devices share the same LAN with the same subnet mask. 9. The placement of the firewall in the topology follows the "Bastion Host" model. 8. All switches are configured and operational, and don't have to be concerned about them. This applies also to all servers as they are configured and fully functional. 10. The firewall is not configured and must be configured at the start with device initial/base configuration plan which is going to be one of your first steps in deployment stage. MS Windows 2016 Active Directory/File Mgmt & Accounts 11. The firewall that is used in the topology is Dell SonicWall TZ-300 model which has three types of link interfaces LAN (4 ports), WAN, and DMZ. Store 192.168.12.11/27 Sales/Mkting Switch 2 SW2 ***** Switch 3 SW3 MS Windows 2016 Exchange Server Switch 4 SW4 **** MS Windows 2016 Terminal Services Summary of your team's tasks 192.168.12.12/27 Subneto subnet1 subnet2 192.168.12.13/2 subnet3 MS Windows 2016 SQL Server MS Windows 2016-IIS Webserver 192.168.12.14/27 Switch 1 SW1 subneto 2 FW internall Interface Firewall 192.168.12.15/27 Firewall Ext. Interface 220.51.79.1/28 3 Email Gateway Spam Filter 220.51.79.15/20 Your team will provide inputs to the MC management in three phases; each phase will take 1 week. At the end of each week, you will submit your results to the MC management. Phase 0 is to set up your teams. You will work in teams of 2-3. Phase 1 will be a firewall policy. Phase 2 will be a subnetting table and the needed firewall rules. Phase 3 will be a presentation (using VoiceThread) describing your solution and any recommendations you may have. 4 Telecommuter Mobile Worker Customers Users Design by Ma 5
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


