Answered step by step
Verified Expert Solution
Question
1 Approved Answer
I need the above items master the following options. *Options: A . Alice's public key B. Encryption or cryptography C. Work factor D. Bob's public
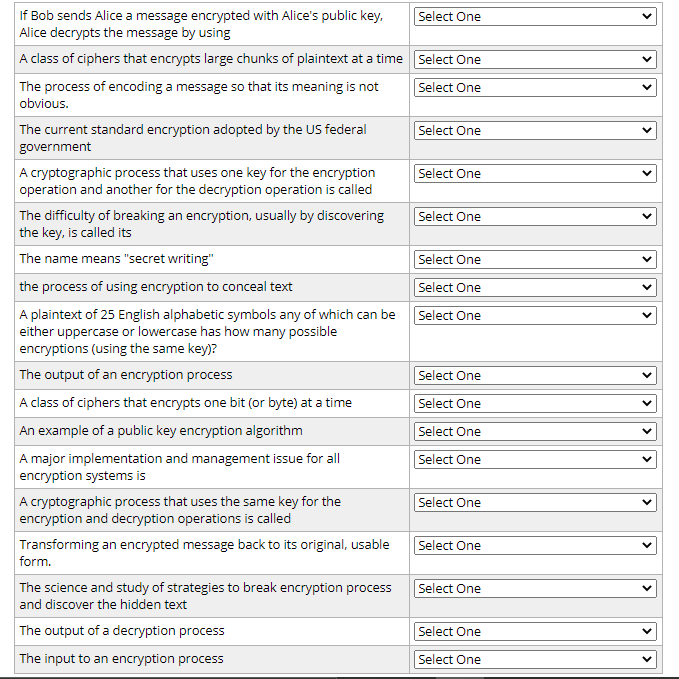
I need the above items master the following options.
*Options:
A . Alice's public key B. Encryption or cryptography C. Work factor D. Bob's public key E. Encryption F. 36^25 G. AES (Rijndael) H. Ciphertext I. Plaintext J. The management of the keys K. Asymptomatic encryption (or public key) L. Block ciphers M. Symmetric encryption (or secret key) N. Alice's private key O. Cryptography D. Decryption Q. Cryptanalysis R. 52^25 S. RSA T. DES V. Steam ciphers
> If Bob sends Alice a message encrypted with Alice's public key, Select One Alice decrypts the message by using A class of ciphers that encrypts large chunks of plaintext at a time Select One The process of encoding a message so that its meaning is not Select One obvious. The current standard encryption adopted by the US federal Select One government A cryptographic process that uses one key for the encryption Select One operation and another for the decryption operation is called The difficulty of breaking an encryption, usually by discovering Select One the key, is called its The name means "secret writing" Select One the process of using encryption to conceal text Select One A plaintext of 25 English alphabetic symbols any of which can be Select One either uppercase or lowercase has how many possible encryptions (using the same key)? The output of an encryption process Select One A class of ciphers that encrypts one bit (or byte) at a time Select One An example of a public key encryption algorithm Select One A major implementation and management issue for all Select One encryption systems is A cryptographic process that uses the same key for the Select One encryption and decryption operations is called Transforming an encrypted message back to its original, usable Select One form. The science and study of strategies to break encryption process Select One and discover the hidden text The output of a decryption process Select One The input to an encryption process Select One > >Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


