IN C create a program that.

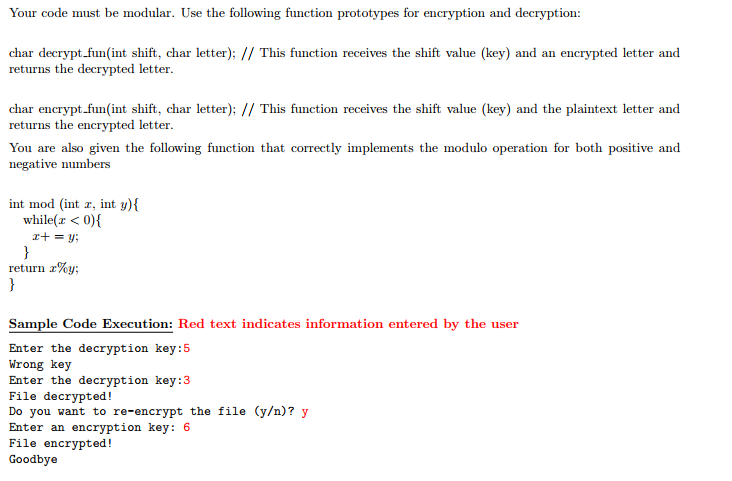
The Caesar's cipher is a cryptographic method for encrypting text such that it out access to the cryptographic key. It is named after Julius Caesar, who allegedly used it to protect messages of military significance. The encryption and decryption operations are simple shifts of the alphabet letters in a cyclic fashion. Mathematically, for a key k, the encryption and decryption are defined as: unreadable to a party with- Encryption: c= (z+k) mod 26. Decryption :r=(c-k) mod 26. To illustrate the use of the Ceasar's cipher, consider the encryption of "fry" with key k 3. Letters f, r, y correspond to the 5th, 16th, and 24th letter of the alphabet (letter a being the 0th) 6(5 + 3) r: (16 + 3) y: (24 + 3) mod 26-8i mod 26-19 u mod 26-1 b Similarly, the decryption of i,u,b follows the reverse process i:(8-3) u: (19-3) b:(1-3) mod 26-5f mod 26-16 r mod 26-24 y NOTE: The modulo operation for negative numbers is different from the % arithmetic operator in C Write a C program that decrypts a file named "encrypted.txt and places the decryption output to a file called "decrypted.txt . A file encrypted with k-3 is provided with the assignment. You can use it to test your decryption function. You will know when you have succeeded because the text becomes readable. In your program . Ask the user to enter the decryption key. . Repeat the request until the right key is entered. Display a message when file decryption is over . Ask the user to enter a key to re-encrypt the file . Re-encrypt file "decrypted.txt" and store it at "encrypted.txt" Display a message when file encryption is over Only alphabet letters (uppercase/lowercase) must be encrypted. The remaining characters (question marks, periods, etc. must remain intact Your code must be modular. Use the following function prototypes for encryption and decryption: char decrypt.fun(int shift, char letter); // This function receives the shift value (key) and an encrypted letter and returns the decrypted letter The Caesar's cipher is a cryptographic method for encrypting text such that it out access to the cryptographic key. It is named after Julius Caesar, who allegedly used it to protect messages of military significance. The encryption and decryption operations are simple shifts of the alphabet letters in a cyclic fashion. Mathematically, for a key k, the encryption and decryption are defined as: unreadable to a party with- Encryption: c= (z+k) mod 26. Decryption :r=(c-k) mod 26. To illustrate the use of the Ceasar's cipher, consider the encryption of "fry" with key k 3. Letters f, r, y correspond to the 5th, 16th, and 24th letter of the alphabet (letter a being the 0th) 6(5 + 3) r: (16 + 3) y: (24 + 3) mod 26-8i mod 26-19 u mod 26-1 b Similarly, the decryption of i,u,b follows the reverse process i:(8-3) u: (19-3) b:(1-3) mod 26-5f mod 26-16 r mod 26-24 y NOTE: The modulo operation for negative numbers is different from the % arithmetic operator in C Write a C program that decrypts a file named "encrypted.txt and places the decryption output to a file called "decrypted.txt . A file encrypted with k-3 is provided with the assignment. You can use it to test your decryption function. You will know when you have succeeded because the text becomes readable. In your program . Ask the user to enter the decryption key. . Repeat the request until the right key is entered. Display a message when file decryption is over . Ask the user to enter a key to re-encrypt the file . Re-encrypt file "decrypted.txt" and store it at "encrypted.txt" Display a message when file encryption is over Only alphabet letters (uppercase/lowercase) must be encrypted. The remaining characters (question marks, periods, etc. must remain intact Your code must be modular. Use the following function prototypes for encryption and decryption: char decrypt.fun(int shift, char letter); // This function receives the shift value (key) and an encrypted letter and returns the decrypted letter








