Question
java 1. This step is toCreate a new Customer Java class which implements the Encryptable interface on page 426. To make it a little easier,
java
1. This step is toCreate a new Customer Java class which implements the Encryptable interface on page 426. To make it a little easier, you can start with a copy of the Secret class (pages 426-428). These files should be among the Student Data Files you downloaded at the beginning of the semester. The Customer class should include: The following instance data: 1. Customer ID 6 digits represented as a String 2. last name - String 3. first name - String 4. email address - String 5. user name - String 6. bank balance float 7. password - String 8. encypted - boolean Remove any code/variables from Secret that is not needed by Customer. A constructor which requires 7 parameters (the first 7 shown above). The following could be a sample instantiation of an object from the Customer class: Customer bankCustomer = new Customer (123456, Smith, John, jsmith0001@kctcs.edu, jsmith0001, 1511.20, Sillygoat213); Since all of the passwords currently in the file are not encrypted, the constructor should set the encrypted data item in the class to FALSE. A definition for the encrypt( )method (required by the Encryptable interface): o This method uses a simple technique to encrypt a password: Reverse the order of the characters in the password (for example, if the password is Sillygoat213, it would become 312taogylliS. You are NOT permitted to use the StringBuffer class. This assignment is partially designed to review string manipulation. o Use the Caesar cipher, shown in the Secret class in Chapter 9, to further encrypt the reversed-order version of the password use a set shift value of 4. o This method should update the password to the encrypted password you generated and change the encrypted data item to TRUE. A definition for the decrypt( )method (required by the Encryptable interface): o This method uses a simple technique to decrypt an encrypted password. Use the Caesar cipher, shown in the Secret class in Chapter 9, to shift the encrypted passed by -4. Then reverse the order of the characters in the password. You are NOT permitted to use the StringBuffer class. o This method should update the password to the decrypted password you generate and change the encrypted data item to FALSE. From a security point of view, think about which data items in the class need accessors. Create those accessors. Include a comment in the Customer class file which explains why you chose the ones you did and why excluded the others. Create the accessors that you chose. You do not have to create any mutators for the data items for this assignment. However, include a comment in the Customer class file as to which you feel need a mutator and why. Include a toString( ) method to build and return a string that contains all instance data items in a nice format. In Blackboard, a file named Customer.csv was included with this assignment. It contains a list of 200 Customer records. All of the passwords in this file are currently not encrypted. 2. The bank wants you to create and test a program that would encrypt customer passwords. To do this, create a driver program named CustomerList which reads through the Customer.csv file and displays First name Last name Original password Encrypted password Note: You are not updating the Customer file, you are simply displaying the old and new password. The accessors will help with this. The driver will simply read a record, display name and original password, encrypt the password, and display the new encrypted password. The bank is debating whether or not to enforce a password rules: passwords should be 10 characters or longer You want to know how many records in the file currently have invalid passwords if the new rules were initiated. Create a class called InvalidPWException to help with this. This will be similar to the OutofRangeException class on page 454 of the textbook. This is pretty simple. Dont overcomplicate this. 3. Create a copy of the driver, naming it CustomerExceptions. Create a new InvalidPWException objects in the driver program for: password is too short The new driver program should throw an exception if the password is too short. You might want to refer to the CreatingExceptions program on page 453. Display only records with passwords which are too short: First name Last name User ID Password (this will not be encrypted) Error message
Customer file
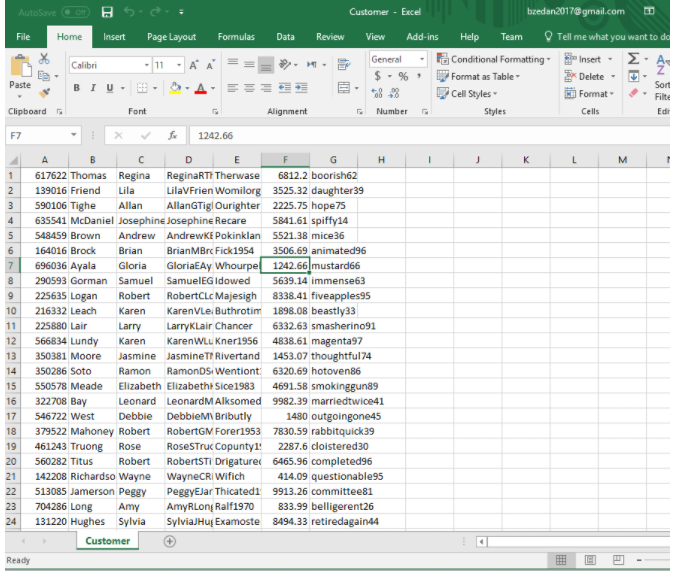
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


