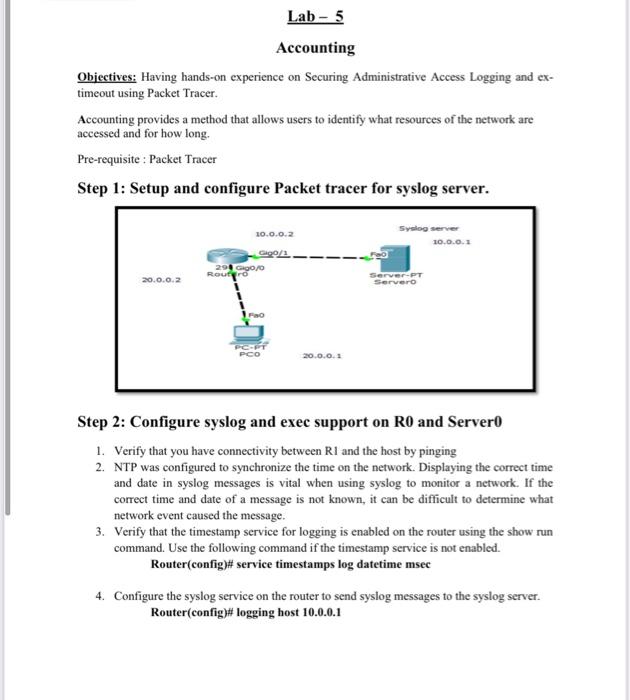
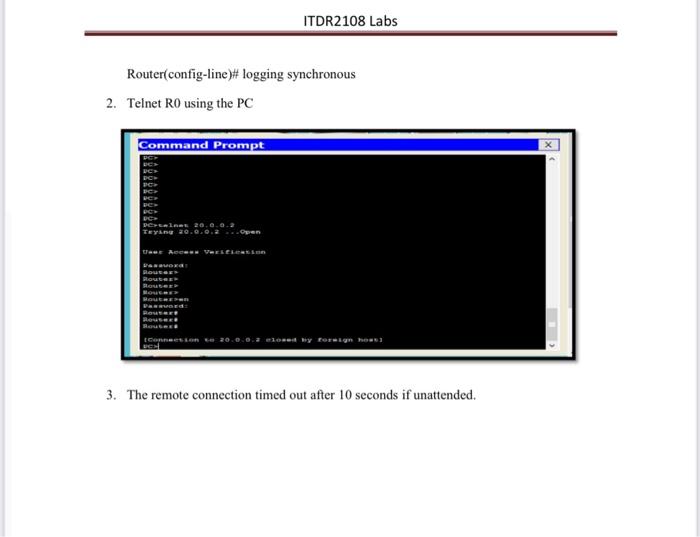
Lab - 5 Accounting Objectives: Having hands-on experience on Securing Administrative Access Logging and ex- timeout using Packet Tracer. Accounting provides a method that allows users to identify what resources of the network are accessed and for how long, Pre-requisite : Packet Tracer Step 1: Setup and configure Packet tracer for syslog server. 10.0.0.2 Sysiog server 10.0.0.1 Gigs 29 GOOD Rouryo 20.0.0.2 Servero FO Step 2: Configure syslog and exec support on RO and Server 1. Verify that you have connectivity between RI and the host by pinging 2. NTP was configured to synchronize the time on the network. Displaying the correct time and date in syslog messages is vital when using syslog to monitor a network. If the correct time and date of a message is not known, it can be difficult to determine what network event caused the message. 3. Verify that the timestamp service for logging is enabled on the router using the show run command. Use the following command if the timestamp service is not enabled. Router(config)# service timestamps log datetime msec 4. Configure the syslog service on the router to send syslog messages to the syslog server. Router(config)# logging host 10.0.0.1 ITDR2108 Labs Step 3: Configure the logging severity level on RO. Logging traps can be set to support the logging function. A trap is a threshold that when reached triggers a log message. The logging message debugging is used Router(config)#logging trap debugging Step 4: Display the current status of logging for Ro. Use the show logging command to see the type and level of logging enabled. Routershow logging Step 5: Display the current status of logging for RO using Logging Server. a. Open services in the server computer and check the syslog status Step 6: exec-timeout for block repetitive telnet login into RO 1. To avoid repetitive logins during this lab, the exec timeout can be set to 0(minutes) O(seconds), which prevents it from expiring. Configure the following in the RO Router(config)ttenable secret 12345 Router(config)# line vty 0 4 Router(config-line)# password cisco Router(config-line /exec-timeout 0 10 Router(config-line)# login ITDR2108 Labs Router(config-line)# logging synchronous 2. Telnet RO using the PC Command Prompt X Cales 20.0.0.2 Teng 20.0.0.2 ... Open DE A VELES 3. The remote connection timed out after 10 seconds if unattended