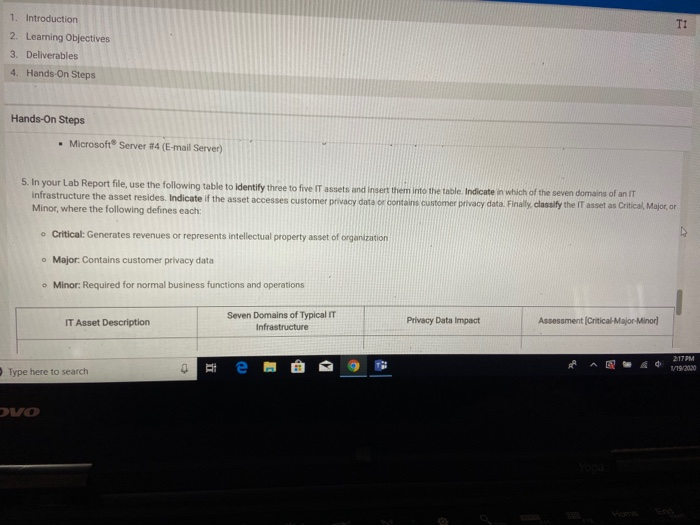
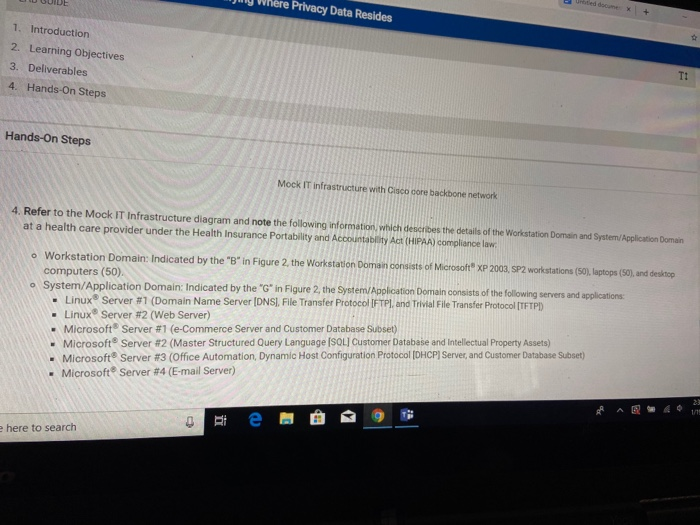
LAB GUIDE 1. Introduction 2. Learning Objectives 3. Deliverables 4. Hands-On Steps Learning Objectives Upon completing this lab, you will be able to: 1. Create an IT asset/inventory checklist organized within the seven domains of a typical IT infrastructure 2. Perform an asset identification and asset classification exercise for a typical IT infrastructure. 3. Explain how a data classification standard is linked to customer privacy data protection and proper security controls. 4. Identify where privacy data can reside or traverse throughout the seven domains of a typical IT Infrastructure 5. Identify where privacy data protection and proper security controls are needed to assist organizations with maintaining compliance O Type here to search 1. Introduction 2. Learning Objectives 3. Deliverables 4. Hands-On Steps Hands-On Steps Microsoft Server #4 (E-mail Server) 5. In your Lab Report file, use the following table to identify three to five IT assets and insert them into the table. Indicate in which of the seven domains of an IT infrastructure the asset resides. Indicate if the asset accesses customer privacy data or contains customer privacy data. Finally classify the IT asset as Critical Major, or Minor, where the following defines each: o Critical: Generates revenues or represents intellectual property asset of organization o Major: Contains customer privacy data Minor: Required for normal business functions and operations IT Asset Description Seven Domains of Typical IT Infrastructure Privacy Data Impact Assessment (Critical-Major Minor] 217 PM o Type here to search e A o &O 12.20 ovo U GUIDE wg Where Privacy Data Resides 1. Introduction 2. Learning Objectives 3. Deliverables 4. Hands-On Steps Hands-On Steps Mock IT infrastructure with Cisco core backbone network 4. Refer to the Mock IT Infrastructure diagram and note the following information, which describes the details of the Workstation Domain and System/Application Domain at a health care provider under the Health Insurance Portability and Accountability Act (HIPAA) compliance law. o Workstation Domain: Indicated by the "B" in Figure 2 the Workstation Domain consists of Microsoft XP 2003, SP2 workstations (501, laptops (50), and desktop computers (50) System/Application Domain: Indicated by the "G" in Figure 2, the System/Application Domain consists of the following servers and applications: - Linux Server #1 (Domain Name Server (DNS). File Transfer Protocol IFTP), and Trivial File Transfer Protocol [TFTPD) - Linux Server #2 (Web Server) - Microsoft Server #1 (e-Commerce Server and Customer Database Subset) - Microsoft Server #2 (Master Structured Query Language [SOL] Customer Database and intellectual Property Assets) - Microsoft Server #3 (Office Automation, Dynamic Host Configuration Protocol (DHCP Server, and Customer Database Subset) - Microsoft Server #4 (E-mail Server) te 9 e here to search LAB GUIDE 1. Introduction 2. Learning Objectives 3. Deliverables 4. Hands-On Steps Learning Objectives Upon completing this lab, you will be able to: 1. Create an IT asset/inventory checklist organized within the seven domains of a typical IT infrastructure 2. Perform an asset identification and asset classification exercise for a typical IT infrastructure. 3. Explain how a data classification standard is linked to customer privacy data protection and proper security controls. 4. Identify where privacy data can reside or traverse throughout the seven domains of a typical IT Infrastructure 5. Identify where privacy data protection and proper security controls are needed to assist organizations with maintaining compliance O Type here to search 1. Introduction 2. Learning Objectives 3. Deliverables 4. Hands-On Steps Hands-On Steps Microsoft Server #4 (E-mail Server) 5. In your Lab Report file, use the following table to identify three to five IT assets and insert them into the table. Indicate in which of the seven domains of an IT infrastructure the asset resides. Indicate if the asset accesses customer privacy data or contains customer privacy data. Finally classify the IT asset as Critical Major, or Minor, where the following defines each: o Critical: Generates revenues or represents intellectual property asset of organization o Major: Contains customer privacy data Minor: Required for normal business functions and operations IT Asset Description Seven Domains of Typical IT Infrastructure Privacy Data Impact Assessment (Critical-Major Minor] 217 PM o Type here to search e A o &O 12.20 ovo U GUIDE wg Where Privacy Data Resides 1. Introduction 2. Learning Objectives 3. Deliverables 4. Hands-On Steps Hands-On Steps Mock IT infrastructure with Cisco core backbone network 4. Refer to the Mock IT Infrastructure diagram and note the following information, which describes the details of the Workstation Domain and System/Application Domain at a health care provider under the Health Insurance Portability and Accountability Act (HIPAA) compliance law. o Workstation Domain: Indicated by the "B" in Figure 2 the Workstation Domain consists of Microsoft XP 2003, SP2 workstations (501, laptops (50), and desktop computers (50) System/Application Domain: Indicated by the "G" in Figure 2, the System/Application Domain consists of the following servers and applications: - Linux Server #1 (Domain Name Server (DNS). File Transfer Protocol IFTP), and Trivial File Transfer Protocol [TFTPD) - Linux Server #2 (Web Server) - Microsoft Server #1 (e-Commerce Server and Customer Database Subset) - Microsoft Server #2 (Master Structured Query Language [SOL] Customer Database and intellectual Property Assets) - Microsoft Server #3 (Office Automation, Dynamic Host Configuration Protocol (DHCP Server, and Customer Database Subset) - Microsoft Server #4 (E-mail Server) te 9 e here to search