Answered step by step
Verified Expert Solution
Question
1 Approved Answer
.Latest network medium should be used Latest network security devices should be used By considering the above scenario answer the following questions: i). What


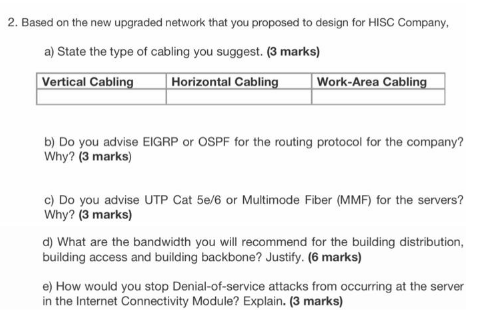
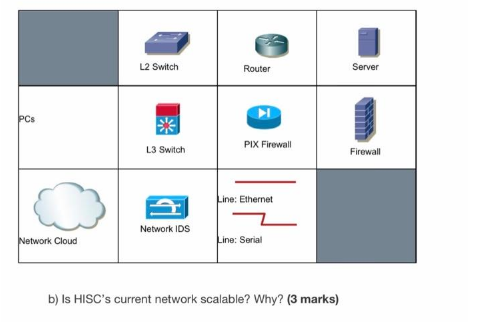

.Latest network medium should be used Latest network security devices should be used By considering the above scenario answer the following questions: i). What type of network topology you suggest for the above network scenario? Why you suggest that network topology, justify your answer in your own words? ii). What type of network you suggest for the above network scenario to share the important data/files among all users? Why you suggest that network, justify your answer? iii). Write the name of the cables which are used to connect the following network devices in the new network. (2 marks) iv). IP Plan for the above network scenario-write the correct IP address in the following table. Use Class-C IP address: 192.168.1.0 Answer the following questions by considering the above scenario i). What network medium can be used to connect network devices within IBRICT network? How the data is being sent through this medium? ii). What network medium can be used to connect a network in Oman to connect with the network in Saudhi Arabia? How the data is being sent through this medium? iii). Differentiate the above mentioned network mediums. Question 4: 4. As a network designer, you are asked to create a new network with 2 departments, each department with 1 computer. Connect both departments by using a router. 2. Based on the new upgraded network that you proposed to design for HISC Company, a) State the type of cabling you suggest. (3 marks) Vertical Cabling Horizontal Cabling Work-Area Cabling b) Do you advise EIGRP or OSPF for the routing protocol for the company? Why? (3 marks) c) Do you advise UTP Cat 5e/6 or Multimode Fiber (MMF) for the servers? Why? (3 marks) d) What are the bandwidth you will recommend for the building distribution, building access and building backbone? Justify. (6 marks) e) How would you stop Denial-of-service attacks from occurring at the server in the Internet Connectivity Module? Explain. (3 marks) PCs L2 Switch Router Server PIX Firewall L3 Switch Firewall Line: Ethernet Network IDS Network Cloud Line: Serial b) Is HISC's current network scalable? Why? (3 marks) The headquarters are located in state A and B, in addition to two branches in states C and D. The C branch consists of design and development departments, with 85 active desktop PCs. There is no IS department in C branch, and the branch C has to be connected to B headquarter office directly The D branch consists of Advertisement, Accountings and IS departments, with 350 active desktop PCs. The D branch has to be connected to the headquarter A office directly. Yousef as a system admin is designing an Active Directory Domain Services (ADDS) infrastructure for DesignTech company. The company has registered the DesignTech.net domain name, and Yousef has created a subdomain called local.DesignTech.net for use by Active Directory (AD).
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


