Answered step by step
Verified Expert Solution
Question
1 Approved Answer
On question 6 I answered: Unrelated On question 10 I answered: Confidentiality On question 11 I answered: Integrity On question 19 I answered: All of
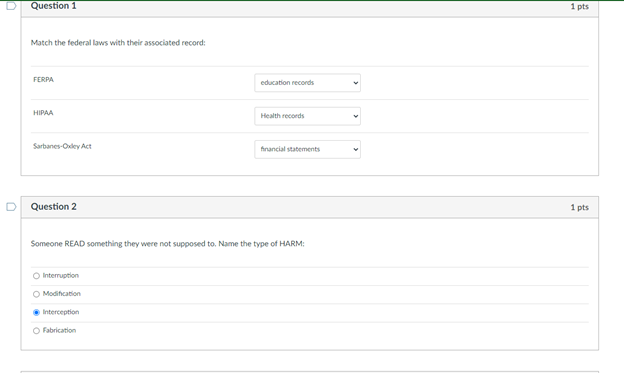
On question 6 I answered: Unrelated
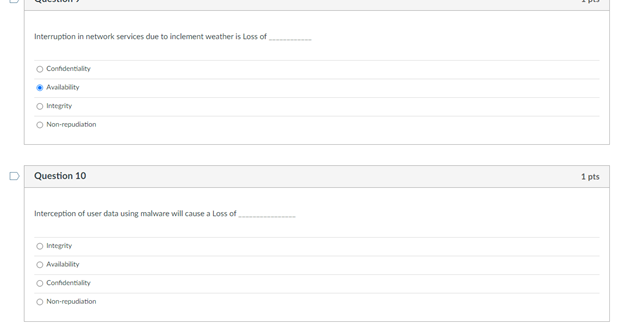
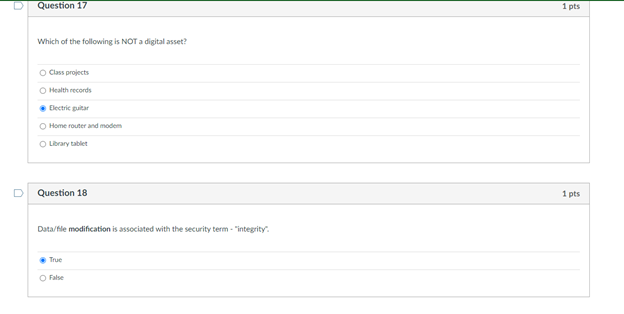
On question 10 I answered: Confidentiality
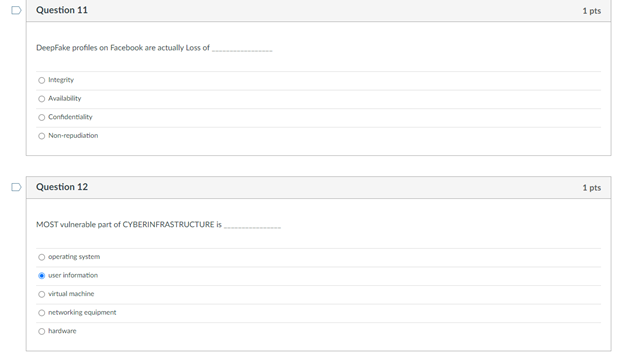
On question 11 I answered: Integrity
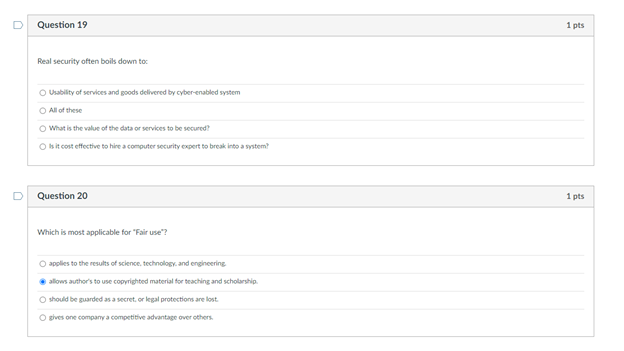
On question 19 I answered: All of these
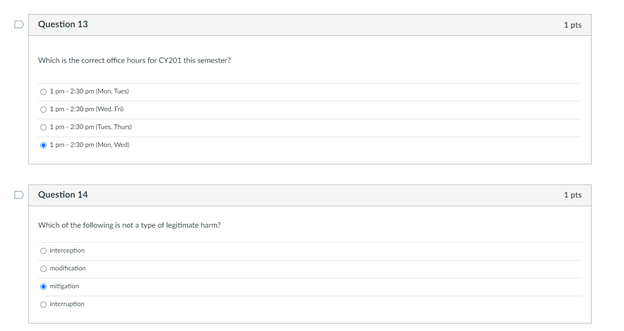
Also, I know question 13 is correct... However, I got a 18.25/20. Some help would be greatly appreciated... thanks.
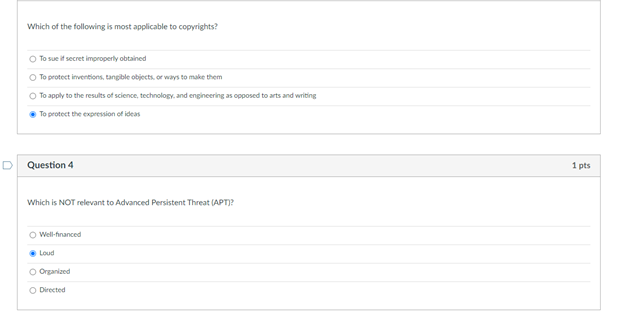
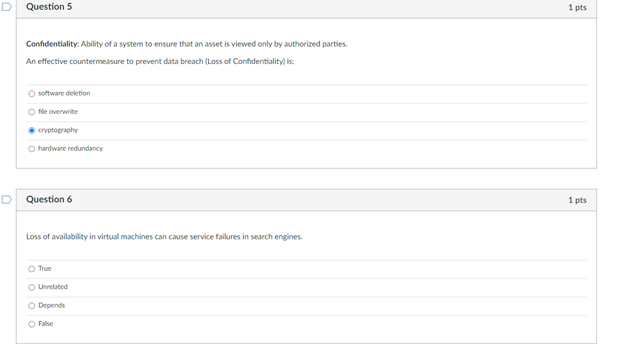
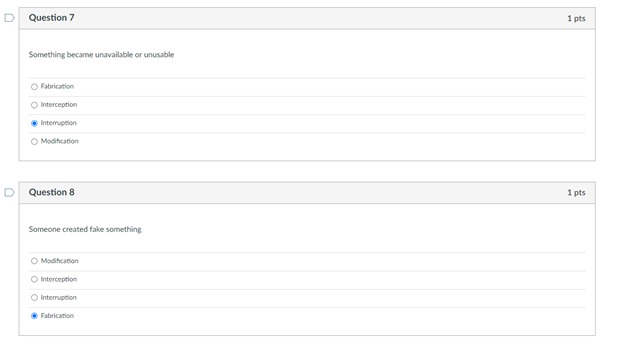
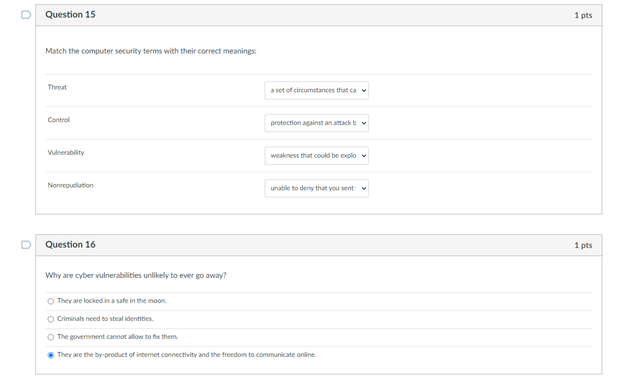
Question 1 1 pts Match the federal laws with their associated record: FERPA education records HIPAA Health records Sarbanes-Oxley Act financial statements D Question 2 1 pts Someone READ something they were not supposed to Name the type of HARM: Interruption Modification Interception Fabrication Which of the following is most applicable to copyrights? To sue it secret improperly obtained To protect inventions, tangible objects or ways to make them To apply to the results of science, technology and engineering as opposed to arts and writing To protect the expression of ideas Question 4 1 pts Which is NOT relevant to Advanced Persistent Threat (APT)? Well-financed Loud Organized Directed D Question 5 1 pts Confidentiality: Ability of a system to ensure that an asset is viewed only by authorized parties. An effective countermeasure to prevent data breach (Loss of Confidentiality) is software deletion file overwrite cryptography O hardware redundancy Question 6 1 pts Loss of availability in virtual machines can cause service failures in search engines. True Unrelated Depends False D Question 7 1 pts Something became unavailable or unusable O Fabrication Interception Interruption O Modification D Question 8 1 pts Someone created fake something O Modification Interception Interruption Fabrication Interruption in network services due to inclement weather is loss of Condentiality Availability Integrity Non-repudiation Question 10 1 pts Interception of user data using malware will cause a Loss of Integrity Availability Confidentiality Non-repudiation Question 11 1 pts DeepFake profile on Facebook are actually Loss of Integrity Availability Confidentiality Non-repudiation Question 12 1 pts MOST vulnerable part of CYBERINFRASTRUCTURE IS operating system user information virtual machine O networking equipment hardware Question 13 1 pts Which is the correct othce hours for CY201 this semester? 1 pm - 2:30 pm (Mon Tues) 1.2.30 pm Wed. Pre 1 m. 2.30pm (Tues, Thur 1 pm - 2:30 pm (Mon Wed! D Question 14 1 pts Which of the following is not a type of legitimate harm? Interception modification mitigation interruption Question 15 1 pts Match the computer security terms with their correct meanings Threat a set of circumstances that ca Control protection against attack Vulnerability weakness that could be explo Nonrepudiation unable to deny that you sent U Question 16 1 pts Why are cyber vulnerabilities unlikely to ever go away? They are locked in a safe in the moon Criminals need to steal identities The government cannot allow to fix them. They are the by-product of internet connectivity and the freedom to communicate online. Question 17 1 pts Which of the following is NOT a digital asset? Class projects Health records Electric guitar Home router and modem Library tablet Question 18 1 pts Data/fle modification is associated with the security term - "integrity. True False D Question 19 1 pts Real security often boils down to Usability of services and goods delivered by cyber-enabled system All of these What is the value of the data or services to be secured! Is it cost effective to hire a computer security expert to break into a system Question 20 1 pts Which is most applicable for "fair use"? apples to the results of science, technology, and engineering allows author's to use copyrighted material for teaching and scholarship should be guarded as a secret or legal protections are lost Oglves one company a competitive advantage over othersStep by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


