Please complete this activity and do the 3 deliverables from the 2nd picture. Professor wants screen shots from wireshark included as well. THANKS IN ADVANCE!!!
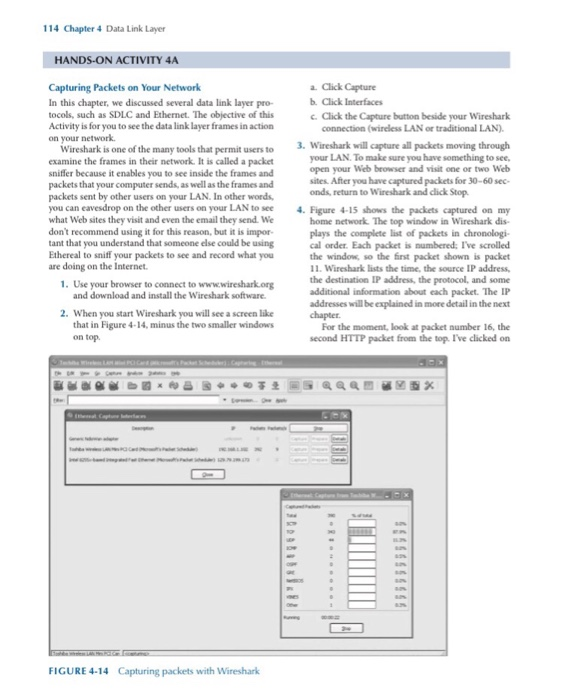
114 Chapter 4 Data Link Layer HANDS-ON ACTIVITY 4A Capturing Packets on Your Network a Click Capture b. Click Interfaces In this chapter, we discussed several data link layer pro- tocols, such as SDLC and Ethernet. The objective of this Activity is for you to see the data link layer frames in action Click the Capture buttion beside your Wireshark connection (wireless LAN or traditional LAN) 3. Wireshark will capture all packets moving through Wireshark is one of the many tools that permit users to examine the frames in their network. It is called a packet sniffer because it enables you to see inside the frames and your LAN. To make sure you have something to see, open your Web browser and visit one or two Web sites. After you have captured packets for 30-60sec- packets that your computer sends, as well as the frames and packets sent by other users on your LAN. In other words you can eavesdrop on the other users on your LAN to see what Web sites they visit and even the email they send. We don't recommend using it for this reason, but it is impor- tant that you understand that someone else could be using Ethereal to sniff your packets to see and record what you onds, return to Wireshark and click Stop. . Figure 4-15 shows the packets captured on my home network The top window in Wireshark dis- plays the complete list of packets in chronologi- cal order. Each packet is numbered: I've scrolled the window, so the first packet shown is packet 11. Wireshark lists the time, the source IP address, the destination IP address, the protocol, and some additional information about each packet. The IP addresses will be explained in more detail in the next are doing on the Internet 1. Use your browser to connect to www.wireshark org and download and install the Wireshark software. 2. When you start Wireshark you will see a screen like that in Figure 4-14, minus the two smaller windows For the moment, look at packet number 16, the second HTTP packet from the top. I've clicked on on top. FIGURE 4-14 Capturing packets with Wireshark Hands-On Activity 4A 115 this packet, so the middle window shows the inside of the packet. The first line in this second window says the frame (or packet if you prefer) is 1091 byties long. It contains an Ethernet II packet, an Internet Protocol (IP) packet, a Transmission Control Pro- tocol (TCP) packet, and a Hypertext Transfer Pro- tocol (HTTP) packet. Remember in Chapter 1 that Figure 1.4 described how each packet was placed inside another packet as the message moved through the layers and was transmitted version. The data before the highlighted section are the TCP packet. From Chapter 2, you know that the client sends an HTTP request packet to request a Web page, and the Web server sends back an HTTP response packet. Packet number 25 in the top window in Figure 4-15 is the HTTP response sent back to my computer by the Yahoo! server. You can see that the destination IP address in my HTTP request is the source IP address of this HTTP packet Click on the plus sign (+) in front of the HTTP packet to expand it. Wireshark shows the con- tents of the HTTP packet. By reading the data inside the HTTP packet, you can see that this packet was an HTTP request to myyahoo.com that contained a cookie. If you look closely, you'll see that the sending computer was a Tablet PC-thats some of the optional information my Web browser (Internet Explorer) induded in the 1. List the 5. Figure 4-15 also shows what happens when you click the plus sign (+) in front of the Ethernet II packet to expand it. You can see that this Ethernet packet has a destination address and source address (e.g shows the thelayer 2,3,4, and S PDUs that are used in your network to send a request to get a Web page. HTTP header The bottom window in Figure 4-15 shows the exact bytes that were captured. The section high- lighted in gray shows the HTTP packet. The num- bers on the left show the data in hexadecimal for 3. What value is in the Ethernet type held in thismes- mat, whereas the data on the right show the text 2. List the source and destination Ethernet addresses on the message sage? Why FIGURE 4-15 Analyzing packets with Wireshark









