Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Please do this problem in C programming language: deskey.txt content: 0f1571c947d9e859 You need to develop 2 C programs DES ECB Enc.c and DES ECB Dec.c
Please do this problem in C programming language:
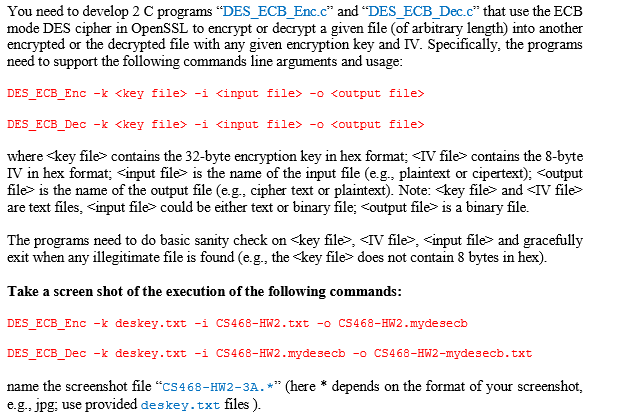
deskey.txt content:
0f1571c947d9e859You need to develop 2 C programs "DES ECB Enc.c" and "DES ECB Dec.c" that use the ECB mode DES cipher in OpenSSL to encrypt or decrypt a given file (of arbitrary length) into another encrypted or the decrypted file with any given encryption key and IV. Specifically, the programs need to support the following commands line arguments and usage: DES_ECB_Enc -k
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


