Answered step by step
Verified Expert Solution
Question
1 Approved Answer
please forget previous problem. this is the actual problem Lab - What was Taken? Objectives Search for and read about a few recent occurrences of
please forget previous problem. this is the actual problem
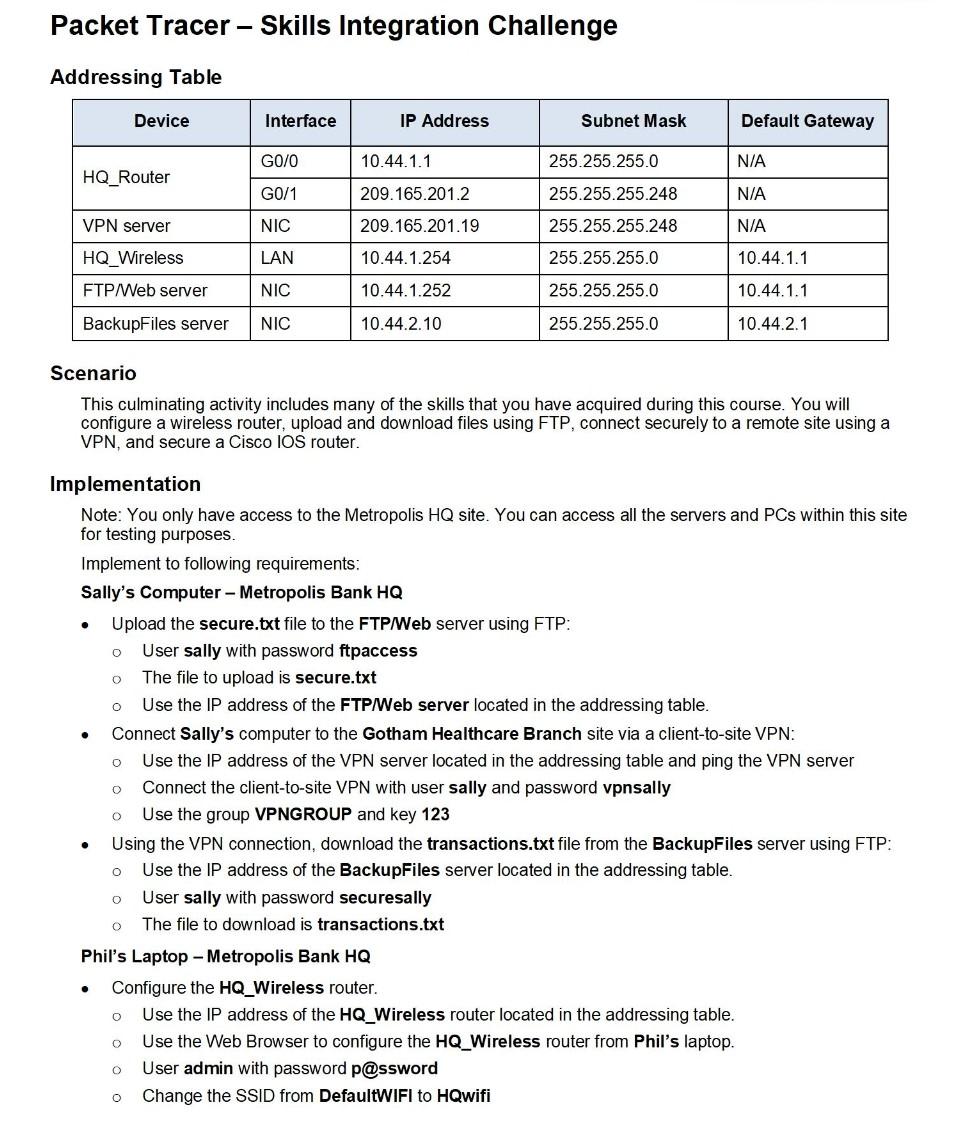

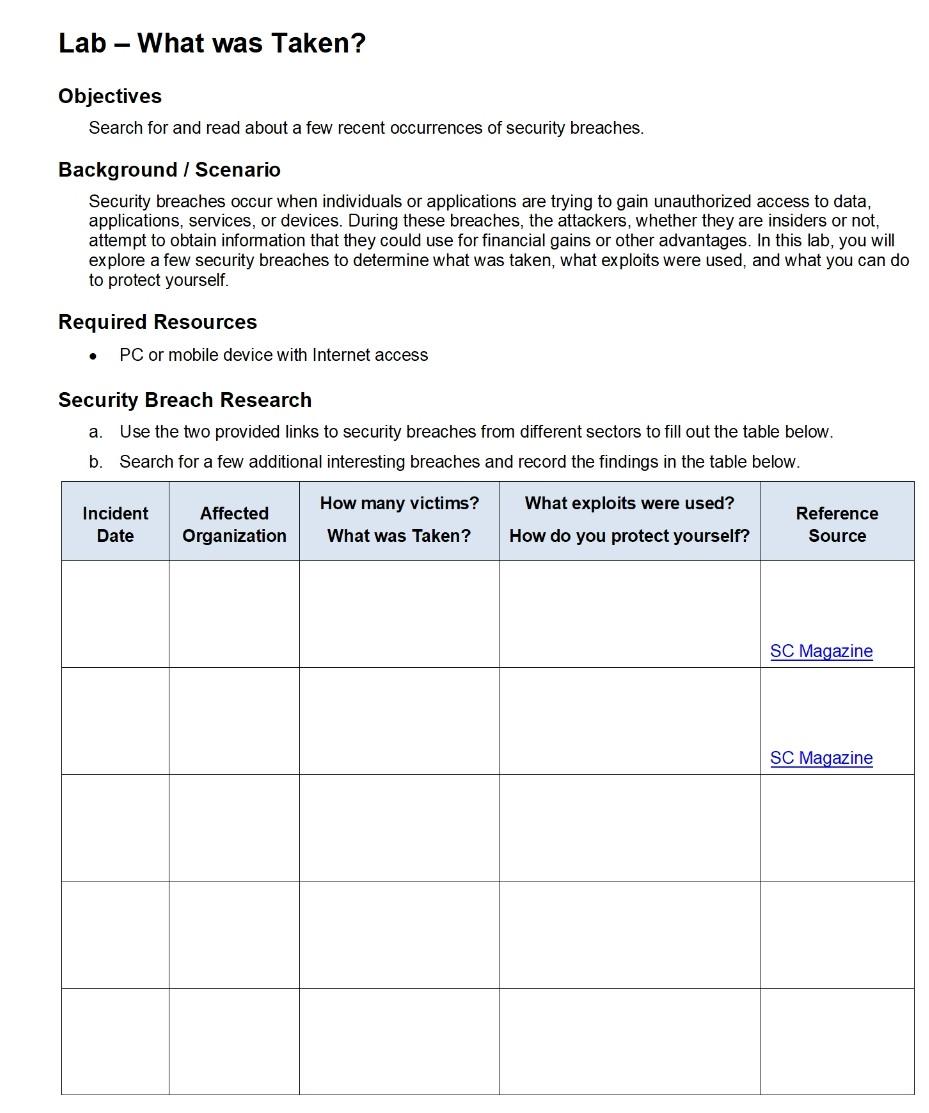
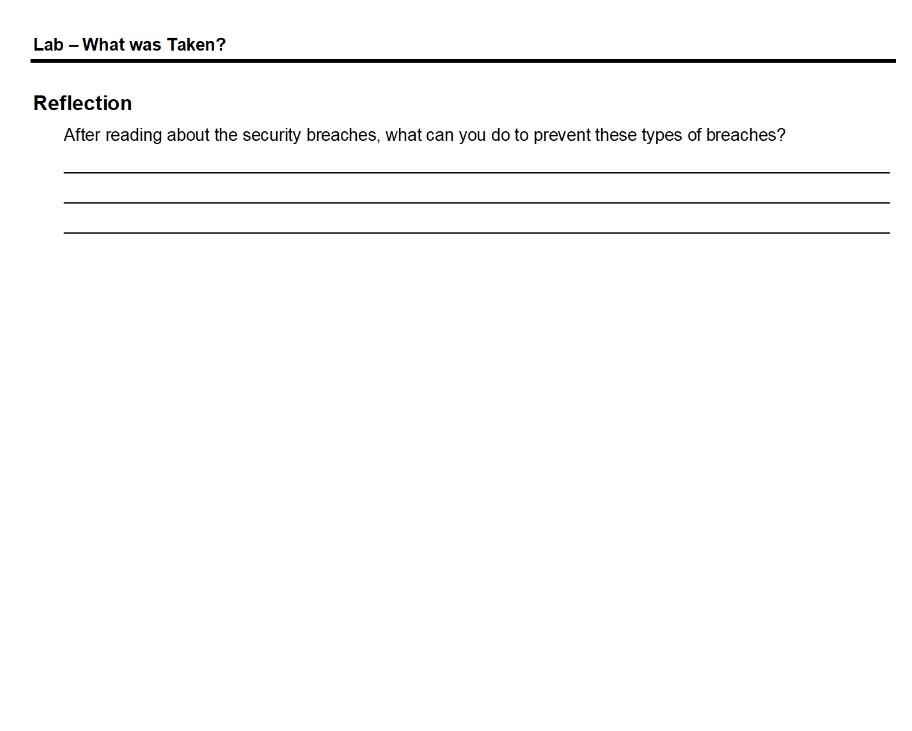
Lab - What was Taken? Objectives Search for and read about a few recent occurrences of security breaches. Background / Scenario Security breaches occur when individuals or applications are trying to gain unauthorized access to data, applications, services, or devices. During these breaches, the attackers, whether they are insiders or not, attempt to obtain information that they could use for financial gains or other advantages. In this lab, you will explore a few security breaches to determine what was taken, what exploits were used, and what you can do to protect yourself. Required Resources . PC or mobile device with Internet access Security Breach Research Use the two provided links to security breaches from different sectors to fill out the table below. b Search for a few additional interest breaches and record the findings in the table below. a. How many victims? Incident Date Affected Organization What exploits were used? How do you protect yourself? Reference Source What was Taken? SC Magazine SC Magazine Lab - What was Taken? Reflection After reading about the security breaches, what can you do to prevent these types of breaches? Packet Tracer - Skills Integration Challenge - Addressing Table Device Interface IP Address Subnet Mask Default Gateway G0/0 10.44.1.1 N/A HQ_Router G0/1 N/A 255.255.255.0 255.255.255.248 255.255.255.248 255.255.255.0 VPN server 209.165.2012 209.165.201.19 10.44.1.254 NIC N/A HQ_Wireless LAN 10.44.1.1 FTP/ Web server NIC 10.44.1.252 255.255.255.0 10.44.1.1 BackupFiles server NIC 10.44.2.10 255.255.255.0 10.44.2.1 Scenario This culminating activity includes many of the skills that you have acquired during this course. You will configure a wireless router, upload and download files using FTP, connect securely to a remote site using a VPN, and secure a Cisco IOS router. . O O 0 . O Implementation Note: You only have access to the Metropolis HQ site. You can access all the servers and PCs within this site for testing purposes. Implement to following requirements: Sally's Computer - Metropolis Bank HQ Upload the secure.txt file to the FTP/Web server using FTP: User sally with password ftpaccess The file to upload is secure.txt Use the IP address of the FTP/Web server located in the addressing table. Connect Sally's computer to the Gotham Healthcare Branch site via a client-to-site VPN: Use the IP address of the VPN server located in the addressing table and ping the VPN server Connect the client-to-site VPN with user sally and password vpnsally Use the group VPNGROUP and key 123 Using the VPN connection, download the transactions.txt file from the BackupFiles server using FTP: Use the IP address of the BackupFiles server located in the addressing table. User sally with password securesally The file to download is transactions.txt Phil's Laptop - Metropolis Bank HQ Configure the HQ_Wireless router. Use the IP address of the HQ_Wireless router located in the addressing table. Use the Web Browser to configure the HQ_Wireless router from Phil's laptop. User admin with password password Change the SSID from DefaultWIFI to HQwifi 0 . 0 0 O . 0 0 O Packet Tracer - Skills Integration Challenge . 0 Set the SSID to be viewable (broadcasted) to wireless clients. Configure wireless security of WPA2 Personal with the passphrase of cisco321. Secure the HQ_Router. Use the IP address of HQ_Router router located in the addressing table. Use the Command prompt to ssh to HQ_Router with the user phil and password securessh Use the enable command and password cisco. Activate the Cisco IOS resilient configuration feature. Configure a banner motd message that includes the phrase Authorized Access Only Gina's Laptop - Metropolis Bank HQ Connect Gina's laptop to the wireless network. Connect to the SSID of HQwifi Use the Pre-shared Key of cisco321 Verify that the laptop uses DHCP O o 0 0 O Suggested Scoring Rubric Packet Tracer scores 90 points
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


