Answered step by step
Verified Expert Solution
Question
1 Approved Answer
please put the code clearly Assignments Goals: 1. Getting the practical knowledge of arrays and several types of linked lists. 2. Learning the real-life application
please put the code clearly


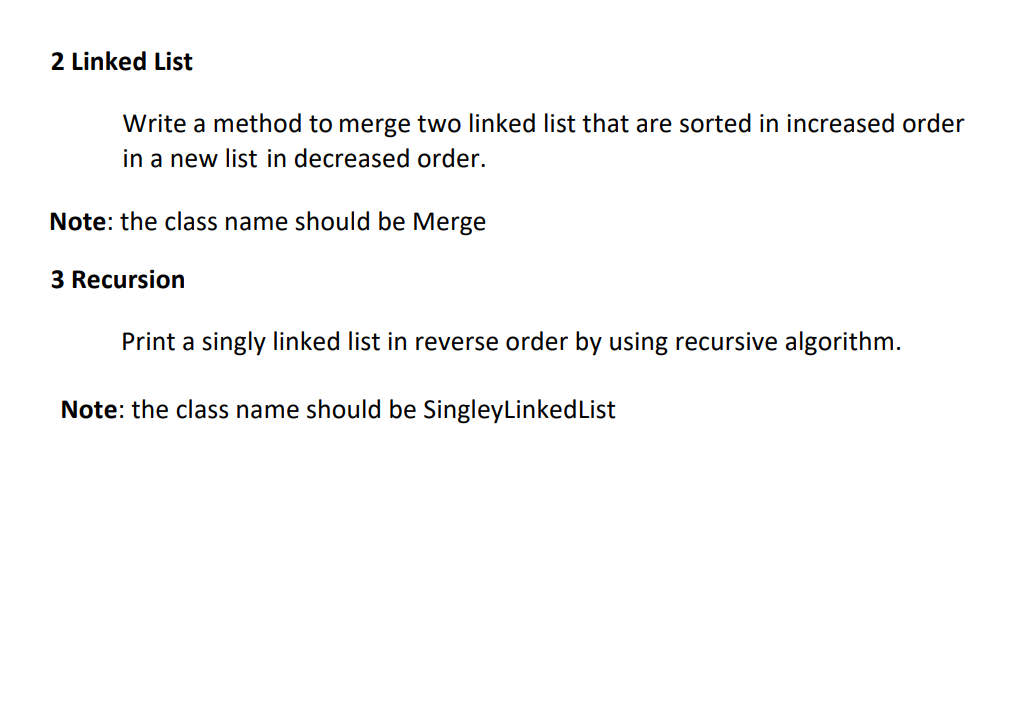
Assignments Goals: 1. Getting the practical knowledge of arrays and several types of linked lists. 2. Learning the real-life application of linked lists, arrays and recursion. Assignments Rules: 1. The submission will be on Blackboard folder (one submission per group). 2. You should use comments for your methods and state your names, students ID 3. Your code should have no compilation errors. 1 Cryptography with Strings and Character Arrays 1 Cryptography: Cryptography is a collection of technique to change the original message to secure a communication between two parties. "This field involves the process of encryption, in which a message, called plaintext, is converted into a scrambled message, called cipher text. It also involves decryption, turning a cipher text back into its original plaintext". One simple type of encryption is to substitute each letter in the plaintext with another letter e.g. substitute each letter with the letter following it by one, two or any number of letters. If each letter will be substituted with the one after it, A will be substituted by B, B will be substituted by C.... and so on. Finally, Z will be substituted with A. Example(1 letter): plain text: hi welcome back cipher Text: ij xfmdpnf cbdl Example(4 letters): plain text: hi welcome back cipher Text: Im aipgsqi fego 1.2 Write a pseudo code (algorithm steps) for an encoder method that takes the plaintext and a number. The number represents how many letters the cipher letter is far from original letter. The algorithm should generate a cipher text for the plaintext by substituting each letter with letter following it by the specified number. Note: write the pseudo code as comment before the next method in the code file. 1.3 Write a method based on your previous answer called encoder that takes a message as plain text and a number. The method should encrypt the message by substituting each letter in the message with the letter following it by the specified number. The method should return the cipher text. 1.4 Write a pseudo code (algorithm steps) for a decoder method that takes the cipher text and a number. The number represents how many letters the cipher letter is far from the original letter. The algorithm should generate the original plaintext for a given cipher text by substituting each letter with the letter preceding it by the specified number. Note: write the pseudo code as comment before the next method in the code file. 1.5 Write a method called decoder that takes a message as cipher text and a number representing the cipher key that is used to encrypt the message. The method should return the cipher text to its original plaintext by substituting each letter by the letter before it according to the specified number. The method should return the plaintext. Note: the class name should be Cipher 2 Linked List Write a method to merge two linked list that are sorted in increased order in a new list in decreased order. Note: the class name should be Merge 3 Recursion Print a singly linked list in reverse order by using recursive algorithm. Note: the class name should be SingleyLinkedList
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


