Question
** Please with an explanation if possible ** *Please answers all or leave it to another expert* Question #:1 Which of the following vulnerabilities can
** Please with an explanation if possible **
*Please answers all or leave it to another expert*
Question #:1
Which of the following vulnerabilities can lead to unexpected system behavior, including the bypassing of security controls, due to differences between the time of commitment and the time of execution?
A. Buffer overflow
B. DLL injection
C. Pointer dereference
D. Race condition
Question #:2
A security analyst is hardening a large-scale wireless network. The primary requirements are the following
* Must use authentication through EAP-TLS certificates
* Must use an AAA server
* Must use the most secure encryption protocol
Given these requirements, which of the following should the analyst implement and recommend? (Select TWO).
A. 802.1X
B. 802.3
C. LDAP
D. TKIP
E. CCMP
F. WPA2-PSK
Question #:3
Which of the following implements a stream cipher?
File-level encryption
IKEv2 exchange
SFTP data transfer
S/MIME encryption
Question #:4
A security administrator is implementing a SIEM and needs to ensure events can be compared against each other based on when the events occurred and were collected. Which of the following does the administrator need to implement to ensure this can be accomplished?
TOTP
TKJP
NTP
HOTP
Question #:5
Which of the following are considered among the BEST indicators that a received message is a hoax? (Select TWO.)
A. Minimal use of uppercase letters in the message
B. Warnings of monetary loss to the receiver
C. No valid digital signature from a known security organization
D. Claims of possible damage to computer hardware
E. Embedded URLs
Question #:6
An incident response analyst at a large corporation is reviewing proxy log data. The analyst believes a malware infection may have occurred. Upon further review, the analyst determines the computer responsible for the suspicious network traffic is used by the Chief Executive Officer (CEO). Which of the following is the best NEXT step for the analyst to take?
A. Call the CEO directly to ensure awareness of the event
B. Run a malware scan on the CEO's workstation
C. Reimage the CEO's workstation
D. Disconnect the CEO's workstation from the network.
Question #:7
Ann, a new employee, received an email from an unknown source indicating she needed to click on the provided link to update her company's profile. Once Ann clicked the link, a command prompt appeared with the following output: 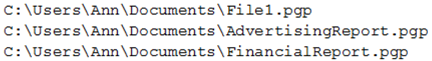 Which of the following types of malware was executed? Ransomware Adware Spyware Virus
Which of the following types of malware was executed? Ransomware Adware Spyware Virus
Question #:8 An Organization requires secure configuration baselines for all platforms and technologies that are used. If any system cannot conform to the secure baseline, the organization must process a risk acceptance and receive approval before the system is placed into production. It may have non-conforming systems in its lower environments (development and staging) without risk acceptance, but must receive risk approval before the system is placed in production. Weekly scan reports identify systems that do not conform to any secure baseline. The application team receive a report with the following results: 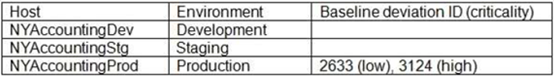 There are currently no risk acceptances for baseline deviations. This is a mission-critical application, and the organization cannot operate If the application is not running. The application fully functions in the development and staging environments. Which of the following actions should the application team take? Remediate 2633 and 3124 immediately. Process a risk acceptance for 2633 and 3124. Process a risk acceptance for 2633 and remediate 3124. Shut down NYAccountingProd and Investigate the reason for the different scan results.
There are currently no risk acceptances for baseline deviations. This is a mission-critical application, and the organization cannot operate If the application is not running. The application fully functions in the development and staging environments. Which of the following actions should the application team take? Remediate 2633 and 3124 immediately. Process a risk acceptance for 2633 and 3124. Process a risk acceptance for 2633 and remediate 3124. Shut down NYAccountingProd and Investigate the reason for the different scan results.
Question #:9 Which of the following is MOST likely happening? 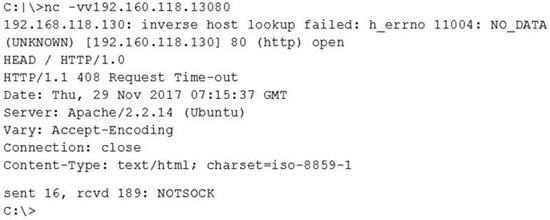
A hacker attempted to pivot using the web server interface. A potential hacker could be banner grabbing to determine what architecture is being used The DNS is misconfigured for the server's IP address. A server is experiencing DoS, and the request Is timing out.
Question #:10 A network administrator was provided the following output from a vulnerability scan. 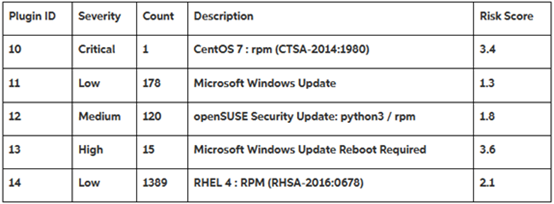 The network administrator has been instructed to prioritize remediation efforts based on overall risk to the enterprise Which of the following plugin IDs should be remediated FIRST? 10 11 12 13 14
The network administrator has been instructed to prioritize remediation efforts based on overall risk to the enterprise Which of the following plugin IDs should be remediated FIRST? 10 11 12 13 14
C:\Users\Ann\Documents File1.pgp C:\Users\Ann\Documents\AdvertisingReport.pgp C:\Users\Ann\Documents Financial Report.pgp Baseline deviation ID (criticality) Host NYAccounting Dev NYAccounting Stg NYAccounting Prod Environment Development Staging Production 2633 (low), 3124 (high) C:\>nc -vv192.160.118.13080 192.168.118.130: inverse host lookup failed: n_errno 11004: NO_DATA (UNKNOWN) [192.160.118.130] 80 (http) open HEAD / HTTP/1.0 HTTP/1.1 408 Request Time-out Date: Thu, 29 Nov 2017 07:15:37 GMT Server: Apache/2.2.14 (Ubuntu) Vary: Accept-Encoding Connection: close Content-Type: text/html; charset=iso-8859-1 sent 16, rcvd 189: NOTSOCK C:\> Plugin ID Severity Count Description Risk Score 10 Critical 1 CentOS 7: rpm (CTSA-2014:1980) 3.4 11 Low 178 1.3 Microsoft Windows Update openSUSE Security Update: python3 / rpm 12 Medium 120 1.8 13 High 15 Microsoft Windows Update Reboot Required 3.6 14 Low 1389 RHEL 4: RPM (RHSA 2016:0678) 2.1
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


