Question: Pls help me to answer the think critically 11.1, 11.2 & Review Concepts. This book is Banking system 2nd edition 11. Robbery Prevention and Response










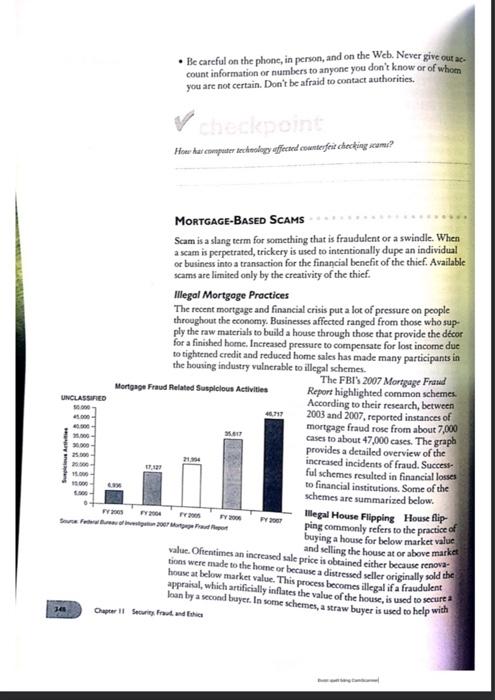









11. Robbery Prevention and Response goals - Discuss how security measures can prevent bank robbery Describe what bank employees should do during a robbery Banking Scene Cheyenne Rainwater has read about the recent increase in bank robberies in her city and in concerned. She knows that her money is protected, but she doesn't want to be present for one of these terrible events, which have resulted in harm to bystanders from time to time. What are some things she should look for that Indicate her bank is trying to prevent robberies! terms handit barrier SECURITY AS PREVENTION When asked why he robbed banks during the 1930s and 1940s, notorious bank robber Willie Sutton simply replied, "Because that's where the money ixYou might think that bank robbery in today's world is merely a plot line for television and movies, but it is a reality and actually occurs all too often. Armed robbery is an inherent risk associated with financial institutions According to the Federal Bureau of Investigation, 7,175 bank robberies- which are federal offenses-occurred in the United States during the year 2007, a 5 percent decrease over the number in the previous year. Every hank is a potential temptation to would be robbers. Despite all of the expensive and state-of-the-art measures banks have invested in to prevent robberies, make them unprofitable and enhance the capture and conviction of the perpetrator, robberies are a persistent problem. Physical Security Ensuring the security of awet, employees, and customers is a major concern for financial institution. Physically securing the bank is an important deterrent to robbery. It's easy to picture and safe deposit bemes when you think of physical security at lunke Lacking devices are certainly part of the business, but physical security includes other consideratives sometimes less obvious Building design plays a role in physical security. Everything from te sistance to attack to placement of sprinklers is a consideration in facility design. Planning the facility for technology.control of physical access to the building.location and security of records, and even the types and B Chapter Il Security Prat, and this Shoald be well dit with the lights penitioned so that they do not interfere placement of furnituse ate part of an integrated security plan. The bank with processing images of perpetrators captured on security video of film. The view of tellers by other employees should be anelstructed Surveillance and alarm technology continues to evolve. Increasingly sophisticated devices with higher and higher resolution are appearing in banks. From cmed-circuit television (CCTV) systems to honoring software for all phases of processing operation, forms of surveillance at becoming increasingly complex. Surveillance cameras should be placed so they are seen by possible robiliers and positioned to ensure a full front photograph of the robber Safety devices can be used. Bandit barriers, which are bulletproof plastic shields, can be positioned in front of each tcller's station. Popup security screens, which rise in a fraction of a second out of the counter to protect the teller, may also be used. Time-delay locks that require a PIN and allow access to the safe cely during specific hours can be installed Transportation security is a part of physical security. With the neces sity of safeguarding cash and checks in transit, transportation security involves screening of employees involved in transportation Companies providing this service are liable for the actions of employees Best Practices Recommendations It is wise for a bank to adopt a list of best practices to help deter bank robberies and to aid in the apprehension of bank bandits. Some measures prevent robberics, some protect staff and custom ers during a robbery, some help apprehend the criminal, and some accomplish a combination of these objectives. Training is a critical factor in Carrying out the best practices. Training is the core of preventing robbery. For this reason, banks invest a lot of resources in teach ing their employees how to recognize and what to do in an emergency. These procedures both lessen the risk of harm for staff and customers and minimize financial loss to the institution. Most banks are required by law to install sur veillance cameras and alarms, and properly trained staff can aid in ensuring that security devices work accurately and are used during a robbery. Security guards, customer service representatives, or others should engage customers as they enter the bank to present a plain view of the security presence and make potential robbers aware that they could be recognized later. 113 tech talk Taking Technology To the Limits To Prevent Robberies In the early 1970s in Los Angeles, as the number of bank robberies, particularly violent on, soured. Find francia tutions worked together to address this problem. Sub Senty banks deemed robbery prone constructed bullets and barriers" or control units (ACUS). The clear, bulletrestant, Poglaspartitions completely endose the teller and adjacent cash storage areas from the top of the counter to the ing or from the floor to the ceiling at the entrance. The ACUs consist of an electronically controlled, double door entrance and adjacent exit Customers access the inside of the bank, one sa time, by entering through the entry's Outer door. When the outer door cloves, a device conducts an automat matometertype search for weapons the search proves septive, the inner door automatically unlocks, allowing entry into the fade key the search yuld a positive result, indicating a possible weapon, the bullet-resistant second door remains locked, and the person must retreat from the entry Think Critically How would you feel about doing your banking in a burk that uses "bandit barriers and ACUS! What factors do you believe are responsible for bank robberie? ROBBERY PREPARATION Just as tellers are usually the first to do business with customers, they are the first line of defense during a robbery. It is critical that teller training include what to do and not to do during a holdup. Training should emphasize that physical resistance is dangerous, noe helpful. Tellers should do nothing that would risk their safety or that of others on the premises. Training should also include these instructions: Remain calm. Knowing what to do through training climinates the need to make decisions during the crisis. . Obey the robber's instructions. Employees should be assured that this is bank policy Trigger foot-pedal or bill trap alarms and security cameras as soon as possible both to protect the safety of customers and employees and to help apprehend the tobbet. A bill trup is a device that sets off a security Chuper Il Security Prestand is 314 system when a bill of switch is pulled Use decoy of marked money or specially prepared packs that contain an exploding device with a dye to mark the cash. Drop a satellite-tracking device into the bag of money, . Call 911 as soon as reasonably possible to provide a detailed description of the perpetrator and the direction he or she seemed to be heading after fleeing the bank. Keep anything, such as a demand note, when possible for fingerprint identification, and minimize contamination of evidence and the crime scene. Countertops are ideal places on which bandits leave fingerprints . Note the robber's physical characteristics, particularly any outstanding feature. Also, if possible, note any characteristics of the get-away vehicle, such as the make, model, color, and license plate number. Write a description of the robber as soon as possible because memory fades quickly, especially in crisis situations. A robbery description form, such as the one below, can be used to help authorities gather information. Weight Sex Build Goate, etc ROBBERY DESCRIPTION FORM (Sample) Age Race Height Complexion light dark, etc.) Eye Color Facial Hair Beard Mustache MISCELLANEOUS Weapon Type Speech Coat or jacket (length and color) Mannerisms CLOTHING Hal Trousers (color and style) Tie Shoes Other Physical characteristics imp, deformities, etc.) It is not uncommon for tellers to become paralyzed with fright during a robbery, leading them to forget procedures for safety and suspect identifice tion. To avoid this situation, some banks provide training at teller schools several times per month and at high-risk banks at least annually. Individual branches reinforce the lessons through practice drills and at staff meetings, By doing so, the tellers are more likely to remember how to react during a robbery without endangering customers or employees. Other employees at the bank play a critically important role by being sensitive to a tellers' body language and demeanor. For example, a change in a teller's voice tone or pitch could indicate that a holdup is in process. A normally relaxed teller who tenses up or a chatty one who becomes quiet could indicate trouble. In one Scattle bank, for instance, a coworker who noticed that sounds from a normally lively teller had become stiff realized that a robbery was occurring and triggered an alarm. Types of Bank Robberies Although bank employees can never be fully prepared for a bank robbery it may be helpful for them to know the different types of robberies that commonly occur to help plan the appropriate actions to take. Morning glory robberies take place prior to opening the bank for the day. The morning glory robber could break in and wait for employees to arrive, seize the employees outside the bank as they arrive, use a ruse tactic to attempt to enter the bank, or even seize an employee en route to or from work or at the employee's home. In a takeover bank robbery, two or more robbers carry weapons and invade the bank. This is the least common type of robbery. The most common type of bank robbery committed involves note passing. In this case, the robber enters the bank and passes a note to a hank employee. The note demands money. The robber may issue a verbal demand instead of passing a note. Weapons may be displayed in all types of robberies as a means of intimidating and coercing bank employees. The FDIC as a Safety Net When robberies occur, it is important that consumers understand that the Federal Deposit Insurance Corporation (FDIC) insures deposits in banks and thrift institutions for up to $100.000 per depositor in the event of fail- ure. As part of the Emergency Economic Stabilization Act of 2008, FDIC insurance coverage per depositor was increased to $250,000 through 2009 Although it is unlikely that a robbery could result in bank failure, FDIC provides safety for individual accounts. a Why is it important that bank employees not resist a robbery attempt? assessment 11.1 Think Critically 1. How does the building facility design contribute to the physical security of a bank? 2. Closed-circuit television systems and security cameras are part of the technology that can identify suspects in bank robbery cases. What role do they play in preventing robberies? 3. Why are robbery training and preparation critical for bank employees, especially tellers? 4. In your opinion, what is the best deterrent in preventing robberies? Make Academic Connections 5. COMMUNICATION Visit a local bank to find out what types of security measures it uses and employee training preparation for robberies it offers. Present your findings in an oral report. RESEARCH Internet banking presents new security challenges for financial institutions. Use the Internet to investigate what the most important issues are and how they are being resolved. Prepare a two-page report summarizing your findings 7. HISTORY Study the bank robberies during the Great Depresion. Why did the Secret Service become involved instead of leaving the crimes to local law enforcement? 27 8/31 Rrymme 11.2 Ethics in Banking goals Explain this to financial in Idently ethical that occur in blog Banking Scene Recent scandals related to unethical and illegal activities have reached corporate world. Several banks have been involved. What can Cheyenne Raimonter do to determine whether her bank seeks to emphasize ethical bebas ter wong is employees! terms code of ethics conflict of here ETHICAL BEHAVIOR Ethics can be defined as the process of determining standards and procedures for dealing with judgmental decisions affecting other people. Ethics refers to beliefs that distinguish right from wrong. Ansical dilema in that is problematic and makes a pena question what is the right "wrong" thing to do Exhical dilemmas make individuals think about the chligation duties, or responsibilities. These dilemmas can be highly comples and difficult to release ones involve a right versus wrong answer. Most people will agree, for example, that it is unacceptable to pretend that we che's work is your own. However, plex ethical dilemmas involvea de sice between right and right." An example might occur if you never collega's error. To whom are you obligated your colleague or your employer? There is only one way for a business to convince the public that it is thical." says Gerald H. Lakin, chairman, president and CEO of Valles Naina Bancorp, and that is to build a record of dealing fairly with its customers, communities, shareholders, and employees." A code of ethics is a statement adopted by the management and board of directors of business to guide employees in taking appropriate in critical situation that could reflect on the organization. A code and employees answer questions about a bank's policy on matters such as receiving gifts from customers and taking outside jobs. Most banks og employees to read the code regularly and certify that they are in compliant with its provision. KPMG, the international accounting firm, fand in is 2000 Organizational Integrity Survey that the ethical behavior of peace tives affects employees' perception of their companies. Overall, pero of the 2,390 employees of the companies surveyed believed that their current customers would recommend their company to others. But whes employees believed management would uphold the company's stated ethical standards, that number set up to 80 percent. 338 Chapter Il Securits. Proud, wd his war estimated that one-third of all currency in circulation waterfeit. The adoption of a national currency in 1863 did not as expected, solve the unterfeiting problem. On 5,1865, the United States AU OF ME counterfeiting created the Secret Service to suppress counterfeiting. More recently, in 2006, an estimated $62 million dollars was lost in the U.S. due to coun terfeiting. Nearly 4,000 people were arrested for crimes relating to the To address the continuing "funny money problem, in 2003 the Federal Reserve began issuing redesigned bills. To date, the $5,510,520, and $50 bills have been redesigned. The most noticeable difference in the new $20 notes is the use of subtle green, peach, and blue colors featured in the back- ground. The new $20 note design retains three important security features The watermark, the faint image similar to the large portrait, which is part of the paper itself and is visible from both sides when the bill is held up to the light . The vertical strip of plastic making up the security thread also visible from both sides when held up to the light is embedded in the paper. *USA TWENTY" and a small flag are visible on the thread. The color-shifting ink-the numeral "20" in the lower-right corner on the face of the note changes from copper to green when the note is tilted. The color shift is more dramatic and easier to see on the new notes Check Fraud interesting facts The National Consumer LARS Americh oldest proc.consumer In 1995 hached Internet Fra Wachs preventie Statistics indicate the seriousness of check fraud. In a recent eight-month period, postal inspectors seized more than $2 billion of fake checks. The hancement of computer technology has made it increasingly easy for sriminals, either individually or in organized groups, to manipulate checks deceive unknowing victims. Desktop publishing and copying to create de duplicate an actual financial document are responsible for a significant amount of check fraud today. In most cases, these crimes begin with the theft of a financial document, such as a blank check, taken from your home vehicle during a burglary, a canceled or old check you throw away or a check you just put in your mailbox. Two of the most common scheme do fected at banks are check kiting and money laundering Other check fraud includes forgery, counterfeiting or alteration, and paperhanging Check Kiting The fraud of check kiting requires opening accounts at two or more institutions and using the float time of available funds to Create fraudulent balances. A person drawsa check for an amount that ek ceeds the account balance at one bank and then deposits it at another bank Before that deposit can be processed, the individual draws a check on the Second bank to deposit at the first bank. Although neither bank account has people postale The most common trad on the wey low price rom preparare repede orde collected eneough money to cover the checks, the person may withdraw more than Check iting has become in recent years due to the Expedited Funds Availability Act of 1987, which requires banks to make funds available The Check 21 Act passed in October 2003 has probably helped content problem. Instead of requiring physical possession of a paper check by the list ing bank bcrore funds are transferred, the Check 21 Act allows the recoving bank to treat an electronic image of the check, called an Image Replacement Document (IRD), the same as the check itself. This significantly reduces the check dicaring process time and has the power to help eliminate check kciting Money Laundering The scheme of money laundering received its name because criminals use it to make moneydean." Criminals use the process to conceal illicitly acquired funds by converting them into seemingly legiti- mate income. Originally used to refer to the proceeds of organized crime, the term is now often associated with financial activities of drug dealers who seek to launder the large amounts of cash they generate from the sale of narcotics Money laundering does not cause financial institutions alo, but it makes large sum of money difficult to trace. To help combat money laundering, Congress has passed several laws The Bank Secrecy Act requires financial institutions to report suspicious transactions that may be a posible violation of law. This act creates a pa- per trail for currency so that money can not be deposited, invested, or ex changed in a way that conceals is illegal source. This discourages the use of banks to hide transfers or deposits of money derived from criminal activity. The Patriot Act of 2001 prohibits financial relationships with banks that have to physical presence in their host county. Under this act, banks must use Banking Math Connection Many insurance policies currently will protect for losses caused by the acceptance in good faithe counterfeit money. Most pay from $500 to $1.500 for a los. During a garage sale, a family unfortunately accepted 5500 in counterfeit balls for a purchase The family's insurance policy covered comes from counterfeit money up to $700 with a $200 deductible. Did the family experience alone from this transaction? If so, how much? Solution determining losis Because the low is less than the 5700 cting the formula for Amount of low-Deductible Amount covered $500 - 5200 - $300 The insurance covers $300, so the actual out-of-pocket loss in $200 ($500 loss - 5300) 144 Chapter 11 Secres Fraud and the inline to determine the identity and source of transactions. The communicate da seeks to curtail the financing of terrorism with laundered money Contact poll of at least Kryery Check forgery, or counterfeiting a check or other document Do people in your commi de intent to defraud, is difficult to spot. Criminals steal a check, cn- foar checking accounts Haeskry experienced any was present it for payment at a retail location or a bank. it with a forged or unauthorized signature, and, using fake identifica tarieties unterfeiting and Alteration Check counterfeiting can mean cither en checking on information sharings are ely creating a check with desktop publishing equipment (personal com Kanner, cutting-edge software, and top-grade laser printer) or simply became? ?a, ariat arer lating a check with advanced color photocopiers. Alteration removes hodifies handwriting and information on the check with chemicals and alients such as acetone, brake fluid, and household bleach. Peperhanging The act of purposefully writing checks on closed accounts u reordering checks for closed accounts is paperhanging. It is also known as died account fraud. Signs of Counterfeit Checks Several signs can indicate a bad check. Telling signs are lack of perforations, alow number (such as 101 through 400 on personal checks or 1001-1500 on bines checks), or no address for the customer or the bank. Stains or discal sation perhaps caused by erasures or alterations are other signs. Be alert to the Magnetic Ink Character Recognition coding number printed along the bermifit is shiny, if it does not match the check number, or if it is missing The first and probably most important line of defense against counter fet checks is teller training. Knowing how to verify a check and what to lock fue cn a suspicious one is the focus of training efforts a Consumer Tips for Preventing Check Fraud Socks are the most common negotiable instrument and should be treated carefully as cash. Here are some steps to prevent check fraud. Che checks that have built-in security features. Many of these checks have a padlock icon on them to indicate the presence of enhanced Security features such as watermarking and microprinting Don't have your social security number imprinted on checks. Your SSN sthough for a criminal to get a credit card, bank account, or fake loan Don't endorse a check until just before you cash or deposit it. It is be in fact, if you sign the check in a teller's presence Don't leave spaces on checks Draw horizontal lincato fill any bank paces, and write words close together, especially on amount in Reconcile your account regularly. Call your bank immediately if you notice any suspicious transactions on your statement Shred statements, canceled checks, ATM slips and credit card recipts ther than just throwing them in the trash Be careful on the phone, in person, and on the Web. Never give out ac- count information or numbers to anyone you don't know or of whom you are not certain. Don't be afraid to contact authorities. How the computer teckersley affected counterfeit checking scami? MORTGAGE-BASED SCAMS Scam is a slang term for something that is fraudulent or a swindle. When a scam is perpetrated, trickery is used to intentionally dupe an individual or business into a transaction for the financial benefit of the thief. Available scams are limited only by the creativity of the thief. Illegal Mortgage Practices The recent mortgage and financial crisis put a lot of pressure on people throughout the economy. Businesses affected ranged from those who sup- ply the raw materials to build a house through those that provide the decor for a finished home. Increased pressure to compensate for lost income due to tightened credit and reduced home sales has made many participants in the housing industry vulnerable to illegal schemes. The FBI'S 2007 Mortgage Frand Mortgage Fraud Related Suplelous Activities Report highlighted common schemes UNCLASSIFIED According to their research, between 46,797 2003 and 2007, reported instances of 3.000 40.000 mortgage fraud rose from about 7,000 25,000 23.07 cases to about 47,000 cases. The graph 90.000 provides a detailed overview of the 21304 increased incidents of fraud. Success ful schemes resulted in financial losses HO 19.00 to financial institutions. Some of the schemes are summarized below. Illegal House Flipping House flip ping commonly refers to the practice of buying a house for below market value value. Oftentimes an increased sale price is obtained either because renova: and selling the house at or above market tions were made to the home or because a distressed seller originally sold the house at below market value. This process becomes illegal if a fraudulent appraisal, which artificially inflates the value of the house, is used to secure Inan by a second bayer. In some schemes, a straw buyer is used to help with Ort Security Prout his Svet FY F 2006 P200 Je flat world... Scom Targets New Zealanders 230, a sick online banking scam fooled New someone else as soon 28 Islanders into losing large sum of money A web possible on the same day she with a professional look and claiming to be buske The scammer then quickly tersporters with all leading New Zealand barks Cancel the $14.000 deposit er utomland for New Zealand readers. The scam Theme The unlucky worted by convincing people to accept deposits into New Zealander has lost his or her teir bank accounts and then to send the funds mi own $13.500 sent to its perpetrators wa transaction fee to a third party Of course, the nel deposit is then canceled. For comple, a scam Think Critically What do you think.com mochte" might deposit $14.000 into the account be done to protect people from scams such as the da New Zealander, who then sends $12.500 on to one in New Zealand besheme. A straw buyer is someone who agrees to use their personal infor- mation to buy the home at a falsely inflated price. The straw buyer agrees to time that they intend to live in the home even though their actual intent is to Lothe home. Sometimes a straw buyer knows that they are participating in a fraudulent scheme and sometimes they themselves are victims. Profits from illegal house flipping can be obtained by intentionally de Sulting on a loan. For example, Buyer A purchases a home for $30,000 and den has it fraudulently appraised for $100,000. Buyer A solicits the help of Bayer B, a straw buyer, to purchase the house for $100.000 by obtain sa bank loan for $80,000. Buyer B does not plan to move in to the house and plans to default on the loan. An illegal profit of $50,000 is available be shared between Buyer A and Bayer R. (An $80,000 loan minus the tal $30,000 investment in the house.) The bank is then left with a los $50,000. This loss arises because the bank has an $50,000 mortgage on a hoose that has a true value of $30,000. According to the FBI, if the loan was Other Mortgage-Based Schemes A variety of other schemes exploit the concepts of illegally inflating the value of a house, obtaining finan to pay for the inflated value and defaulting on loans for personal gain Names of some of these schemes include Bad Bloor Schemes, Salle Astance Scans Short Sude Schemes, and Fonda Racar Sram Checkpoint " What is the necessary dep in the procedura alla fin where achieves a profit? a 21/31 Identity Theft 11.4 Banking Scene goals Explain the concept of identity theft. Describe various identity theft methods - Discuss identity theft prevention terms Cheyenne was puzzled and embarrassed. While pumping pas che attendant had taid, over the loudspeaker where everyone could hear that her credit card had been declined. As she paid her bill in full and on time each month she did not know why her credit card was declined. When she got home. Creyenne called her bank. She was informed that her credit card had been closed due to suspicious activity that included charges in two separate states within hours of each other. Cheyenne then regretted not checking her voice mais promptly, as the bank had left her a message to call. Apparently some one had obtained access to Cheyenne's account information and legally used her identity. What should she do! Could she have prevented this! - spam - phishing war driving wiffer program fraud alert credit freeze AN OVERVIEW OF IDENTITY THEFT Identity theft occurs when someone intentionally obtains your personal in formation to use that information for personal gain. By illegally identifying themselves as you, they engage in financial transactions that enable them to Feceive goods and services that are charged to your accounts Categories of Identity Theft in November, 2007, the Federal Trade Commission (FTC released the 2006 Identity Theft Survey Report. This report categorized identity theft by the severity of the harm caused by the identity thic. The Eng Credit Card Only categorization occurs when the thief only misuse one or more existing credit cards. It is the least serious category. The Entig Ni-Crni Card Account categorization occurs when the thief access an existing ac Count, like a checking or savings account that is not a credit card account The most serious category is New Arrow and Orier Fru In this in stance, the thief opens new accounts using the victim identity. This type of Identity theft can be difficult for the victim to catch One way to catch this is to do an annual review of your credit report. Then How Identity Theft Information is obtained Purchase or other transaction, 75 Know thiet personally, 18 From wallet Company that had Information, From the mail -Hacking into computer, Phishing. 15 Some other way Don't know how into was taken, 56% Source: Federal Trade Commission--2008 identity Thet Survey Report Costs of Identity Theft When identity theft occurs, victims experience financial costs, emotional coses, and loss of productive time. They have to use their time to resolve the many issues that arise from the identity theft. According to the FTCs report, $500 was the median value of goods and services obtained by identity thieves. However, 5 percent of victims indicated that the thieves obtained at least $13,000 of products, Fortunately, over half of the victims incurred no out-of-pocket expenset Some victims, however, had expenses of $5,000 or more. Attorney fees, lom of salary, and paying for any charges attributed to the thief are among the potential costs. There is a variety of laws designed to protect consumers from out-of-pocket losses that result from identity theft. Although the median amount of time victims spent resolving the iden tity theft was four hours, some victims spent at least 130 hours resolving the identity theft. The feelings of identity theft victims range from vulnerability to violation of personal privacy to anger to sadness. The emotional stress caused by identity theft adds to the overall fatigue victims experience when dealing with what can be a long process to thoroughly resolve all issues stemming from the theft checkpoint What are the three general categories of identity theft? 352 Chapter II secures Fraud withics METHODS FOR STEALING IDENTITIES interesting facts aches and as customer payment systems change, new methods of obtain There is a variety of methods available for scaling identities. As technology The Identity Theft Enforce- ment and Pestitution Act of penal information become available. Some theft methods are manual 2007 is an act that developed daher methods are electronic in response to increased Manual Ways to Commit Identity Theft occurrences of identity theft entity thieves can be fairly creative. They have found ways to steal per- and increased losses due to weal information through telephone scams, by using information from em- identity theft. The Act would playment tecneds, through stealing mail in resadential mailboxes, by going increase the ways in which Arough the trash, and through in-person onervation. Once these methods are used to construct a false identity, the thief either steal the individual's identity theft could be funds or obtains credit in the name of the victim. prosecuted. The status of the Act is still pending Telephone Scams Many scams are committed using the telephone The scam may begin with a postcard advertising easy credit approval or low credit card interest rates. When consumers call these phone numbers, someone asks for their checking account number, supposedly as part of a "verification process." Other scams involve con artists that call and claim to be from the person's bank, saying they need to verify certain information about the checking account for various reasons. Another com- mon scam is to call people to tell them that they have won a prize. After a few minutes of pleasant chat, the thief requires the per son to read the numbers off the bottom of a check to "confirm that he or she "qualifies" for the prize. With checking account information, the con artist can issue a bank draft on the person's checking account. Mail Thelt Some identity thieves steal mail from residential mailboxes. As about 700 million pieces of mail are delivered daily, thieves have ample opportunity to steal mail. Personal information, including credit card num- bers and bank account numbers, can be obtained this way. Offers addressed to the resident for new credit or new loans can also be stolen. Once the thief obtains these documents, the information can be used to illegally establish accounts, apply for a loan, or access funds in existing accounts. The U.S. Postal Inspection service works hard to prevent mail theft. According to their website, in 2007 they arrested more than 9,000 suspects for crimes relating to the mail. More than half of those arrests related to mailtheft or identity crimes, VEROORLENERO TROOM 23 NETBookmark Trash Retrieval Dumpster dining occurs when a thief goes through the trash of a business or in dividual with the specific intent of finding either personal identifying information or account infor The Federal Trade Commission (FTO) is dedicated mation to construct a false identity to helping individuals and business wo becom Observation In this day and age, it's hard to ing victims of entithet. Access www.cepe know who is watching you. Discrete image-takin com/schopnance banking and click on the link for Chapter 11 Go to the Federal de Commission devices, ranging from cell phone cameras to website. Review the content in the Hor Linction pocket-sized video recorders with micro button What are some new identity the schemes! How can cameras, can record you discretely. Thieves can record an image of a credit card left exposed on you and your employer work to avoid them a restaurant table or can photograph a customer www.cengage.com/school finance banking entering a PIN in a retail store Electronic Weys to commit Identity Theft The Internet has streamlined financial transac tions. It has also streamlined identity theft. The Internet allows individuals or companies to communicate with tens of thousands of people without spending much time effort of money. The Securities and Exchange Commission says that spam, or junk e-mail, allow "the unscrupulous to target more potential investors than cold calling or mass mailing"Spammers can use a bulk e-mail program to send personal ised messages to thousands of Internet users at a time. In addition, anyone can also reach a large audience by posting a message on an online bulletin board. Fraudtes se spam to find investors for bogus investment scheme Electronic methods for Healing identities abound Phishing Common attacks on banks through the Internet include phishing (fishing which is the act of sendinga er an e-mail falsely daiming to be legitimate enterprise in an attempt to solicit private information. The directs the users to visit a website to which they are to update personal information, such as passwords and credit card, Social Security, and banke count numbers. The scammer commits identity theft using this informed Hacking Computer hackers that gain access to records or systemspor another threat to consumers and banks. Banks should use tools such virus software and sobo, programs that constantly monitor all trane tions looking for abnormalities. Furrealis, programs that monitor and incoming and outgoing transmission, have become increasingly impor as banks allow access to records for online banking via the Internet Ban must safeguard the technology that makes doing business possible Fraudelent HELOC Accounts A HELOC loan enables borrowers borrow against a home equity line of credit. Withdrawals against the co can be made by check or credit card. An identity thief can open an clic HELOC account using a false identity and then methodically withdra funds from the account. 354 Chapter 11 Securites, free and the Fake Websites There are multiple ways to extract personal information from fraudulent websites. One method is to develop a website that looks like an authentic business and prompt people to pay for a product or service from that web site. When the victim enters identifying credit information, the thieves can use that information for their own purposes Another method exploits design weaknesses in the Domain Name System (D.N.S.). In the early 1980s, the D.NS. was developed to provide Internet addresses. The sys tem was not initially intended to safeguard transactions, like credit transactions, that required specific identity verification. Internet-savvy thieves can exploit the D.N.S. to redirect website visitors to nonlegititmate locations where their personal account information can be collected. Personnel Data Theft In the age of laptops and flash drives, it is fairly casy for confidential employee information to be lost or stolen. In recent years, electronic versions of per- vanel data has been stolen from a diverse array of organiza- tions including the United States Veteran Affairs, Equifax, the District of Columbia, and Google. In many instances, an employer will offer employees a one-year free subscription to an identity-theft monitoring service after a data theft occurs. Looking for Opportunities Some thieves seek to abuse wi-fi systems used by stores to transmit customer credit information. War driving refers to the criminal practice of driving around to find retailers with weaknesses in their Internet security systems. Once a weakness has been found, sniffer programs, which are electronic programs that capture account numbers and PINs, can be installed. One particularly effective example of this was widely reported during the summer of 2008. In this case, an international ring of thieves exploited weaknesses in the Internet security of major retailers including TJ. Maxx, Barnes & Noble, and Office Max. More than 41 million debit and credit card numbers were stolen. Sometimes the stolen numbers were sold online and Sometimes they were used to manufacture fraudulent ATM cards Cash could be withdrawn from victims' accounts with the fraudulent ATM Cards. checicpoint Last six ways to steal identity information electronically. IDENTITY THEFT PREVENTION There are a number of ways to proactively protect your personal informa. tion to try to avoid being an identity theft victim. Common Sense Precautions Keep your radar up at all times regarding any suspicious activities or in- quities. If someone unfamiliar is walking around your neighborhood and looking into mailboxes, keep an eye on them. If you think they are stealing mail contact law enforcement authorities. Never provide account access cordes, Social Security numbers, or other personal identifying information over the phone or online unless you are absolutely certain of the validity of the parties with whom you are interacting. Shred all documents containing personal identifying information--including offers for new credit that arrive in the mail Electronic Precautions A fraud alert is an electronic warning placed on your accounts to monitor for suspicious financial activity. According to the FTC, you are legally enti- tled to two free types of fraud alerts. An initial frend alert is good for 90 days and could be put in place if you suspect you may soon be a victim of identity theft. (If perhaps, your wallet was recently stolen.) An extended fraud alert lasts for seven years. An extended alert is a good idea if you have been a victim of identity theft. A copy of the Identity Theft Report must be submitted before an extended fraud alert can be placed on your account A credit freeze prohibits access to your credit report. These electronic protections provide a good first step, but they do not necessarily prevent all types of identity theft. Commercially Sold Identity Protection Packages Many private companies offer a variety of services to help combat identity theft. Some companies offer services, like fraud alerts, that are actually available for free. Some companies may help you resolve complications sulting from being an identity theft victim. Carefully evaluate the services and costs of such programs. Determine the true value they offer before pur- chasing them. re- V checkpoint Distinguish between the two types of fraud alerts. Review Concepts 11. Discuss the way security can be described as robbery prevention 2. Nare several actions that should be part of a "best practices" list for a bank. 13. Why is training the key to preventing robbery? 14. Discuss some actions that tellers should take during a robbery to help identify a suspect afterward. 15. Explain how fraud related to banking may be committed 16. How does a credit freeze help prevent identity theft? 17. Discuss the signs to look for that could identify counterfeit checks. 18. List and explain check fraud. some steps to take to avoid becoming the victim of Chapter 1 Anvestment 350 assessment 11.2 Think Critically 1. Discuss how ethical dilemmas could involve making decisions between "right" and "right." 2. Why is confidentiality a critical element in banking? 3. Discuss the ethical implications of the ability of a bank to determine the interest rate for a loan. 4. Why did Congress and the President see the need for the Sarbanes-Oxley Act? Make Academic Connections 5. TECHNOLOGY Use the Internet to find out about ethical issues regard- ing online banking that are of concern to bank regulators. Present your findings to the class orally 6. RESEARCH Locate the websites of three commercial banks that have a code of ethics. List any elements not covered in this chapter. 7. PROBLEM SOLVING Asa supervisor, you must decide what to do about a loyal, honest employee who tries really hard but can't perform upto par, forcing coworkers to pick up the slack. You know that the employee is a single parent whose child has serious medical problems What do you do? 12 h 3 11. Robbery Prevention and Response goals - Discuss how security measures can prevent bank robbery Describe what bank employees should do during a robbery Banking Scene Cheyenne Rainwater has read about the recent increase in bank robberies in her city and in concerned. She knows that her money is protected, but she doesn't want to be present for one of these terrible events, which have resulted in harm to bystanders from time to time. What are some things she should look for that Indicate her bank is trying to prevent robberies! terms handit barrier SECURITY AS PREVENTION When asked why he robbed banks during the 1930s and 1940s, notorious bank robber Willie Sutton simply replied, "Because that's where the money ixYou might think that bank robbery in today's world is merely a plot line for television and movies, but it is a reality and actually occurs all too often. Armed robbery is an inherent risk associated with financial institutions According to the Federal Bureau of Investigation, 7,175 bank robberies- which are federal offenses-occurred in the United States during the year 2007, a 5 percent decrease over the number in the previous year. Every hank is a potential temptation to would be robbers. Despite all of the expensive and state-of-the-art measures banks have invested in to prevent robberies, make them unprofitable and enhance the capture and conviction of the perpetrator, robberies are a persistent problem. Physical Security Ensuring the security of awet, employees, and customers is a major concern for financial institution. Physically securing the bank is an important deterrent to robbery. It's easy to picture and safe deposit bemes when you think of physical security at lunke Lacking devices are certainly part of the business, but physical security includes other consideratives sometimes less obvious Building design plays a role in physical security. Everything from te sistance to attack to placement of sprinklers is a consideration in facility design. Planning the facility for technology.control of physical access to the building.location and security of records, and even the types and B Chapter Il Security Prat, and this Shoald be well dit with the lights penitioned so that they do not interfere placement of furnituse ate part of an integrated security plan. The bank with processing images of perpetrators captured on security video of film. The view of tellers by other employees should be anelstructed Surveillance and alarm technology continues to evolve. Increasingly sophisticated devices with higher and higher resolution are appearing in banks. From cmed-circuit television (CCTV) systems to honoring software for all phases of processing operation, forms of surveillance at becoming increasingly complex. Surveillance cameras should be placed so they are seen by possible robiliers and positioned to ensure a full front photograph of the robber Safety devices can be used. Bandit barriers, which are bulletproof plastic shields, can be positioned in front of each tcller's station. Popup security screens, which rise in a fraction of a second out of the counter to protect the teller, may also be used. Time-delay locks that require a PIN and allow access to the safe cely during specific hours can be installed Transportation security is a part of physical security. With the neces sity of safeguarding cash and checks in transit, transportation security involves screening of employees involved in transportation Companies providing this service are liable for the actions of employees Best Practices Recommendations It is wise for a bank to adopt a list of best practices to help deter bank robberies and to aid in the apprehension of bank bandits. Some measures prevent robberics, some protect staff and custom ers during a robbery, some help apprehend the criminal, and some accomplish a combination of these objectives. Training is a critical factor in Carrying out the best practices. Training is the core of preventing robbery. For this reason, banks invest a lot of resources in teach ing their employees how to recognize and what to do in an emergency. These procedures both lessen the risk of harm for staff and customers and minimize financial loss to the institution. Most banks are required by law to install sur veillance cameras and alarms, and properly trained staff can aid in ensuring that security devices work accurately and are used during a robbery. Security guards, customer service representatives, or others should engage customers as they enter the bank to present a plain view of the security presence and make potential robbers aware that they could be recognized later. 113 tech talk Taking Technology To the Limits To Prevent Robberies In the early 1970s in Los Angeles, as the number of bank robberies, particularly violent on, soured. Find francia tutions worked together to address this problem. Sub Senty banks deemed robbery prone constructed bullets and barriers" or control units (ACUS). The clear, bulletrestant, Poglaspartitions completely endose the teller and adjacent cash storage areas from the top of the counter to the ing or from the floor to the ceiling at the entrance. The ACUs consist of an electronically controlled, double door entrance and adjacent exit Customers access the inside of the bank, one sa time, by entering through the entry's Outer door. When the outer door cloves, a device conducts an automat matometertype search for weapons the search proves septive, the inner door automatically unlocks, allowing entry into the fade key the search yuld a positive result, indicating a possible weapon, the bullet-resistant second door remains locked, and the person must retreat from the entry Think Critically How would you feel about doing your banking in a burk that uses "bandit barriers and ACUS! What factors do you believe are responsible for bank robberie? ROBBERY PREPARATION Just as tellers are usually the first to do business with customers, they are the first line of defense during a robbery. It is critical that teller training include what to do and not to do during a holdup. Training should emphasize that physical resistance is dangerous, noe helpful. Tellers should do nothing that would risk their safety or that of others on the premises. Training should also include these instructions: Remain calm. Knowing what to do through training climinates the need to make decisions during the crisis. . Obey the robber's instructions. Employees should be assured that this is bank policy Trigger foot-pedal or bill trap alarms and security cameras as soon as possible both to protect the safety of customers and employees and to help apprehend the tobbet. A bill trup is a device that sets off a security Chuper Il Security Prestand is 314 system when a bill of switch is pulled Use decoy of marked money or specially prepared packs that contain an exploding device with a dye to mark the cash. Drop a satellite-tracking device into the bag of money, . Call 911 as soon as reasonably possible to provide a detailed description of the perpetrator and the direction he or she seemed to be heading after fleeing the bank. Keep anything, such as a demand note, when possible for fingerprint identification, and minimize contamination of evidence and the crime scene. Countertops are ideal places on which bandits leave fingerprints . Note the robber's physical characteristics, particularly any outstanding feature. Also, if possible, note any characteristics of the get-away vehicle, such as the make, model, color, and license plate number. Write a description of the robber as soon as possible because memory fades quickly, especially in crisis situations. A robbery description form, such as the one below, can be used to help authorities gather information. Weight Sex Build Goate, etc ROBBERY DESCRIPTION FORM (Sample) Age Race Height Complexion light dark, etc.) Eye Color Facial Hair Beard Mustache MISCELLANEOUS Weapon Type Speech Coat or jacket (length and color) Mannerisms CLOTHING Hal Trousers (color and style) Tie Shoes Other Physical characteristics imp, deformities, etc.) It is not uncommon for tellers to become paralyzed with fright during a robbery, leading them to forget procedures for safety and suspect identifice tion. To avoid this situation, some banks provide training at teller schools several times per month and at high-risk banks at least annually. Individual branches reinforce the lessons through practice drills and at staff meetings, By doing so, the tellers are more likely to remember how to react during a robbery without endangering customers or employees. Other employees at the bank play a critically important role by being sensitive to a tellers' body language and demeanor. For example, a change in a teller's voice tone or pitch could indicate that a holdup is in process. A normally relaxed teller who tenses up or a chatty one who becomes quiet could indicate trouble. In one Scattle bank, for instance, a coworker who noticed that sounds from a normally lively teller had become stiff realized that a robbery was occurring and triggered an alarm. Types of Bank Robberies Although bank employees can never be fully prepared for a bank robbery it may be helpful for them to know the different types of robberies that commonly occur to help plan the appropriate actions to take. Morning glory robberies take place prior to opening the bank for the day. The morning glory robber could break in and wait for employees to arrive, seize the employees outside the bank as they arrive, use a ruse tactic to attempt to enter the bank, or even seize an employee en route to or from work or at the employee's home. In a takeover bank robbery, two or more robbers carry weapons and invade the bank. This is the least common type of robbery. The most common type of bank robbery committed involves note passing. In this case, the robber enters the bank and passes a note to a hank employee. The note demands money. The robber may issue a verbal demand instead of passing a note. Weapons may be displayed in all types of robberies as a means of intimidating and coercing bank employees. The FDIC as a Safety Net When robberies occur, it is important that consumers understand that the Federal Deposit Insurance Corporation (FDIC) insures deposits in banks and thrift institutions for up to $100.000 per depositor in the event of fail- ure. As part of the Emergency Economic Stabilization Act of 2008, FDIC insurance coverage per depositor was increased to $250,000 through 2009 Although it is unlikely that a robbery could result in bank failure, FDIC provides safety for individual accounts. a Why is it important that bank employees not resist a robbery attempt? assessment 11.1 Think Critically 1. How does the building facility design contribute to the physical security of a bank? 2. Closed-circuit television systems and security cameras are part of the technology that can identify suspects in bank robbery cases. What role do they play in preventing robberies? 3. Why are robbery training and preparation critical for bank employees, especially tellers? 4. In your opinion, what is the best deterrent in preventing robberies? Make Academic Connections 5. COMMUNICATION Visit a local bank to find out what types of security measures it uses and employee training preparation for robberies it offers. Present your findings in an oral report. RESEARCH Internet banking presents new security challenges for financial institutions. Use the Internet to investigate what the most important issues are and how they are being resolved. Prepare a two-page report summarizing your findings 7. HISTORY Study the bank robberies during the Great Depresion. Why did the Secret Service become involved instead of leaving the crimes to local law enforcement? 27 8/31 Rrymme 11.2 Ethics in Banking goals Explain this to financial in Idently ethical that occur in blog Banking Scene Recent scandals related to unethical and illegal activities have reached corporate world. Several banks have been involved. What can Cheyenne Raimonter do to determine whether her bank seeks to emphasize ethical bebas ter wong is employees! terms code of ethics conflict of here ETHICAL BEHAVIOR Ethics can be defined as the process of determining standards and procedures for dealing with judgmental decisions affecting other people. Ethics refers to beliefs that distinguish right from wrong. Ansical dilema in that is problematic and makes a pena question what is the right "wrong" thing to do Exhical dilemmas make individuals think about the chligation duties, or responsibilities. These dilemmas can be highly comples and difficult to release ones involve a right versus wrong answer. Most people will agree, for example, that it is unacceptable to pretend that we che's work is your own. However, plex ethical dilemmas involvea de sice between right and right." An example might occur if you never collega's error. To whom are you obligated your colleague or your employer? There is only one way for a business to convince the public that it is thical." says Gerald H. Lakin, chairman, president and CEO of Valles Naina Bancorp, and that is to build a record of dealing fairly with its customers, communities, shareholders, and employees." A code of ethics is a statement adopted by the management and board of directors of business to guide employees in taking appropriate in critical situation that could reflect on the organization. A code and employees answer questions about a bank's policy on matters such as receiving gifts from customers and taking outside jobs. Most banks og employees to read the code regularly and certify that they are in compliant with its provision. KPMG, the international accounting firm, fand in is 2000 Organizational Integrity Survey that the ethical behavior of peace tives affects employees' perception of their companies. Overall, pero of the 2,390 employees of the companies surveyed believed that their current customers would recommend their company to others. But whes employees believed management would uphold the company's stated ethical standards, that number set up to 80 percent. 338 Chapter Il Securits. Proud, wd his war estimated that one-third of all currency in circulation waterfeit. The adoption of a national currency in 1863 did not as expected, solve the unterfeiting problem. On 5,1865, the United States AU OF ME counterfeiting created the Secret Service to suppress counterfeiting. More recently, in 2006, an estimated $62 million dollars was lost in the U.S. due to coun terfeiting. Nearly 4,000 people were arrested for crimes relating to the To address the continuing "funny money problem, in 2003 the Federal Reserve began issuing redesigned bills. To date, the $5,510,520, and $50 bills have been redesigned. The most noticeable difference in the new $20 notes is the use of subtle green, peach, and blue colors featured in the back- ground. The new $20 note design retains three important security features The watermark, the faint image similar to the large portrait, which is part of the paper itself and is visible from both sides when the bill is held up to the light . The vertical strip of plastic making up the security thread also visible from both sides when held up to the light is embedded in the paper. *USA TWENTY" and a small flag are visible on the thread. The color-shifting ink-the numeral "20" in the lower-right corner on the face of the note changes from copper to green when the note is tilted. The color shift is more dramatic and easier to see on the new notes Check Fraud interesting facts The National Consumer LARS Americh oldest proc.consumer In 1995 hached Internet Fra Wachs preventie Statistics indicate the seriousness of check fraud. In a recent eight-month period, postal inspectors seized more than $2 billion of fake checks. The hancement of computer technology has made it increasingly easy for sriminals, either individually or in organized groups, to manipulate checks deceive unknowing victims. Desktop publishing and copying to create de duplicate an actual financial document are responsible for a significant amount of check fraud today. In most cases, these crimes begin with the theft of a financial document, such as a blank check, taken from your home vehicle during a burglary, a canceled or old check you throw away or a check you just put in your mailbox. Two of the most common scheme do fected at banks are check kiting and money laundering Other check fraud includes forgery, counterfeiting or alteration, and paperhanging Check Kiting The fraud of check kiting requires opening accounts at two or more institutions and using the float time of available funds to Create fraudulent balances. A person drawsa check for an amount that ek ceeds the account balance at one bank and then deposits it at another bank Before that deposit can be processed, the individual draws a check on the Second bank to deposit at the first bank. Although neither bank account has people postale The most common trad on the wey low price rom preparare repede orde collected eneough money to cover the checks, the person may withdraw more than Check iting has become in recent years due to the Expedited Funds Availability Act of 1987, which requires banks to make funds available The Check 21 Act passed in October 2003 has probably helped content problem. Instead of requiring physical possession of a paper check by the list ing bank bcrore funds are transferred, the Check 21 Act allows the recoving bank to treat an electronic image of the check, called an Image Replacement Document (IRD), the same as the check itself. This significantly reduces the check dicaring process time and has the power to help eliminate check kciting Money Laundering The scheme of money laundering received its name because criminals use it to make moneydean." Criminals use the process to conceal illicitly acquired funds by converting them into seemingly legiti- mate income. Originally used to refer to the proceeds of organized crime, the term is now often associated with financial activities of drug dealers who seek to launder the large amounts of cash they generate from the sale of narcotics Money laundering does not cause financial institutions alo, but it makes large sum of money difficult to trace. To help combat money laundering, Congress has passed several laws The Bank Secrecy Act requires financial institutions to report suspicious transactions that may be a posible violation of law. This act creates a pa- per trail for currency so that money can not be deposited, invested, or ex changed in a way that conceals is illegal source. This discourages the use of banks to hide transfers or deposits of money derived from criminal activity. The Patriot Act of 2001 prohibits financial relationships with banks that have to physical presence in their host county. Under this act, banks must use Banking Math Connection Many insurance policies currently will protect for losses caused by the acceptance in good faithe counterfeit money. Most pay from $500 to $1.500 for a los. During a garage sale, a family unfortunately accepted 5500 in counterfeit balls for a purchase The family's insurance policy covered comes from counterfeit money up to $700 with a $200 deductible. Did the family experience alone from this transaction? If so, how much? Solution det
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


