
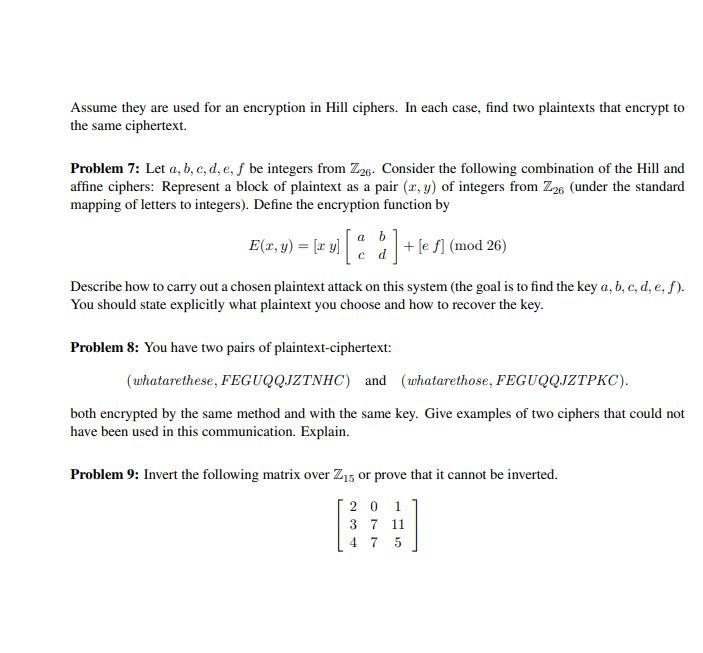
Problem 1: The following ciphertext was produced by an affine cipher modulo 26: CRVVBO. The plain- text starts with ha. Decrypt the message. Problem 2: Suppose you encrypt using an affine cipher, then encrypt the encryption using another affine cipher (both working modulo 26). Is there any advantage to doing this rather than using a single affine cipher? Why or why not? a Problem 3: Suppose that you want to encrypt a message using an affine cipher. You let a = 0,b=1, etc., but you also include ? = 26, ;= 27," = 28 and ! = 29. Therefore you have 30 symbols to encrypt and your affine cipher is given by ax +b (mod 30). (a) Enumerate all choices for a Z30 that allow you to decrypt. (b) Suppose you try to use a = 12 and b = 3. Find two plaintext letters that encrypt to the same ciphertext letter Problem 4: Suppose you have a language with only three letters a, b, c, and they occur with frequencies 0.7,0.2,0.1, respectively. The following ciphertext was encrypted by the Vigenre method (the arithmetic is them modulo 3, not moduo 26): ABCBABBBAC. Suppose you know the key length is 1, 2 or 3. Show that the key length is probably 2, and determine the most probable key. Problem 5:. (a) The ciphertext ONXM was encrypted by a Hill cipher with a 2 x 2 matrix. The plaintext is null. Find the encryption matrix. (b) Suppose the ciphertext is PNXM and the plaintext is still null. Find the encryption matrix. Note that the first column of the matrix is changed. What does it mean? Is it a good or a bad property of a cipher. Discuss. Problem 6: Consider these two matrices: 3 4 and 1 3 1 2 4 1 3 5 0 Assume they are used for an encryption in Hill ciphers. In each case, find two plaintexts that encrypt to the same ciphertext. Problem 7: Let a, b, c, d, e, f be integers from Z26. Consider the following combination of the Hill and affine ciphers: Represent a block of plaintext as a pair (I,y) of integers from Z26 (under the standard mapping of letters to integers). Define the encryption function by E(x, y) = (xy] [] ]+[e ] (mod 26) Describe how to carry out a chosen plaintext attack on this system (the goal is to find the key a, b, c, d, e, f). You should state explicitly what plaintext you choose and how to recover the key. Problem 8: You have two pairs of plaintext-ciphertext: (whatarethese, FEGUQQJZTNHC) and (whatarethose, FEGUQQJZTPKC). both encrypted by the same method and with the same key. Give examples of two ciphers that could not have been used in this communication. Explain. Problem 9: Invert the following matrix over 215 or prove that it cannot be inverted. 2 0 1 3 7 11 4 7 5








