Answered step by step
Verified Expert Solution
Question
1 Approved Answer
The syntax of a user query is verified by Select one: a. Query optimizer Ob. None of the above c. DBA Od. Parser Question

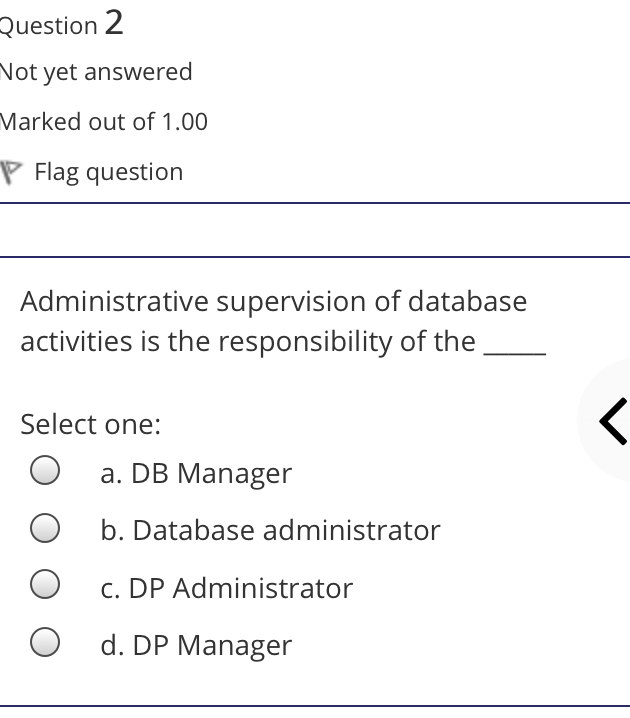
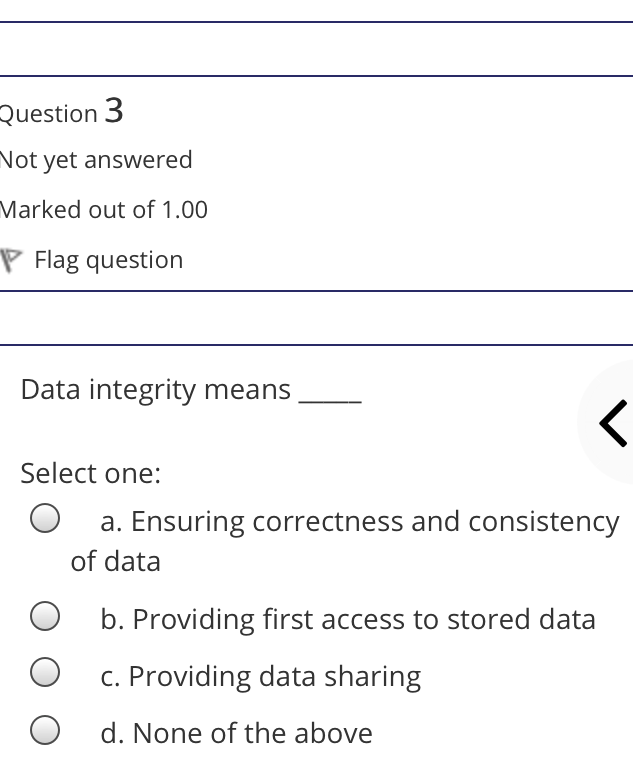
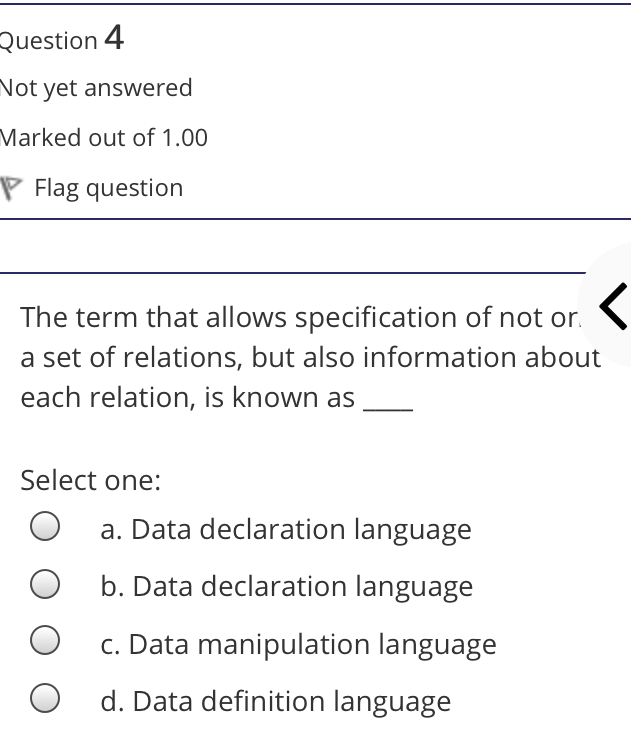
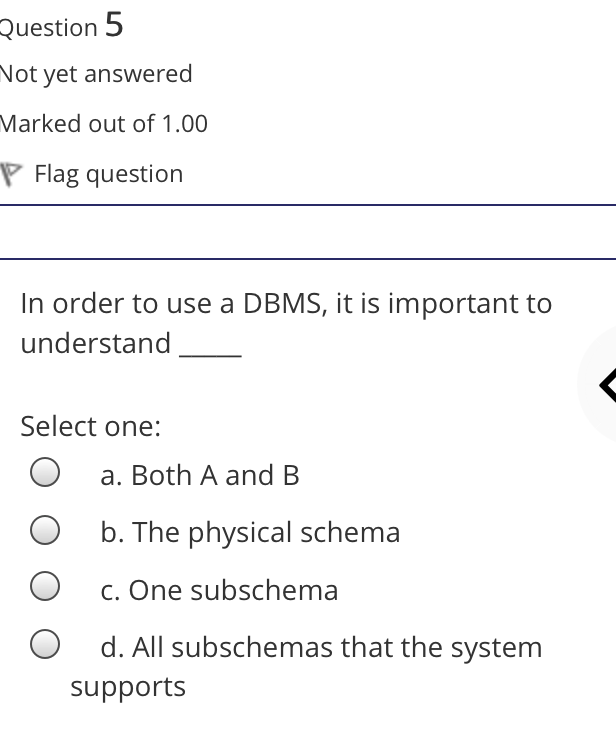
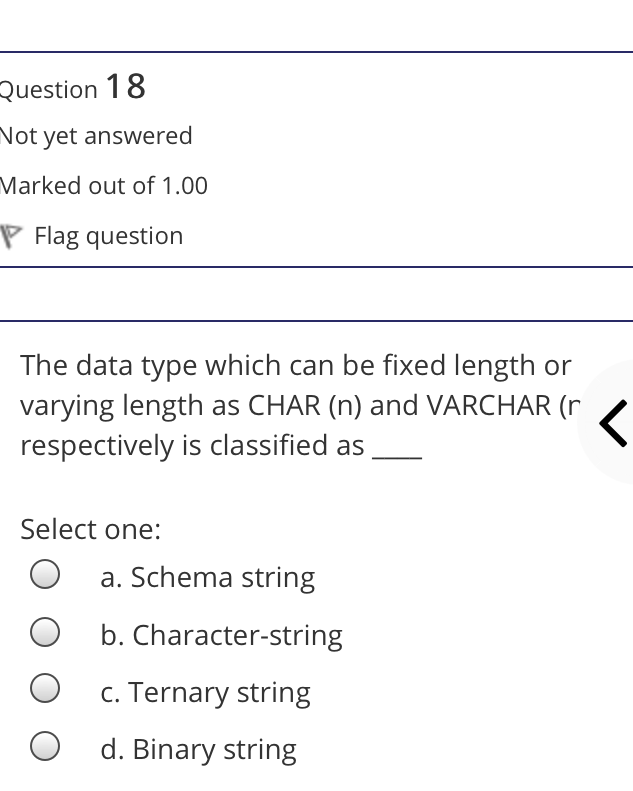
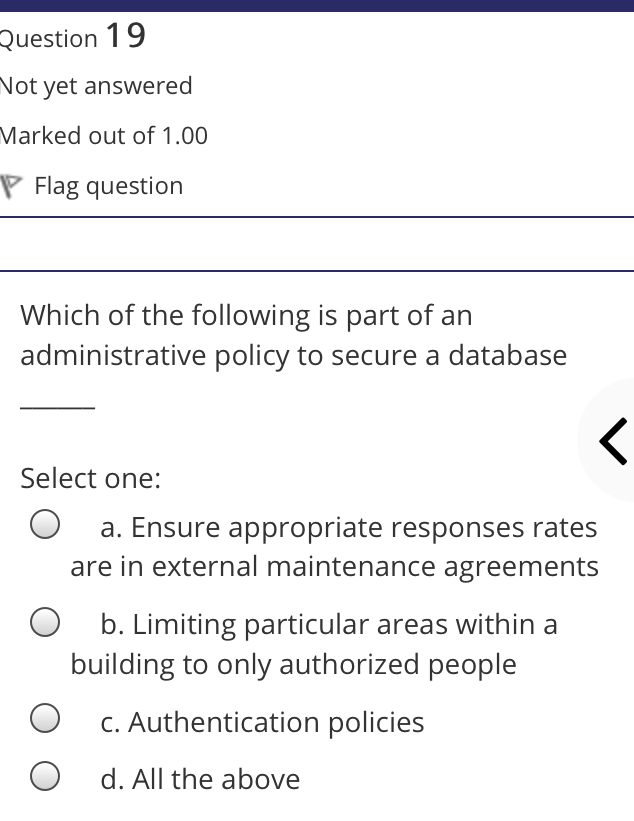
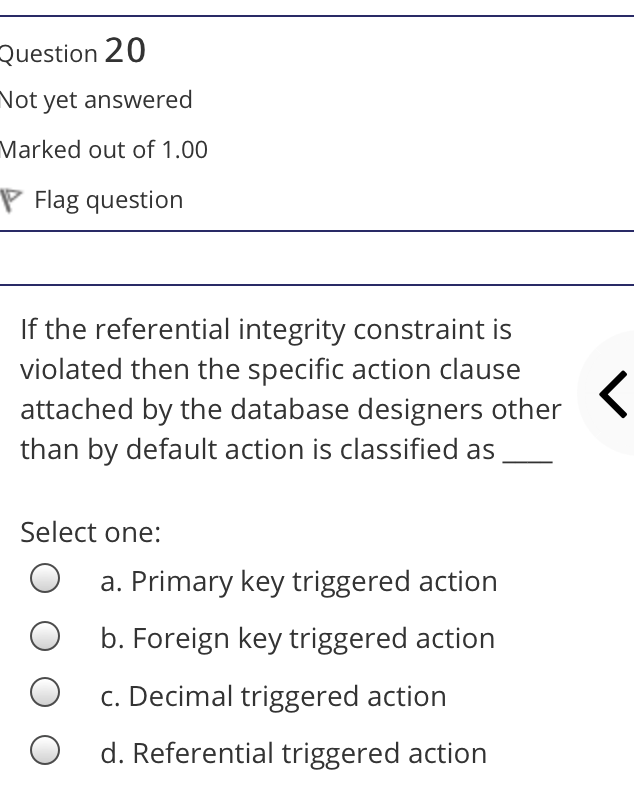
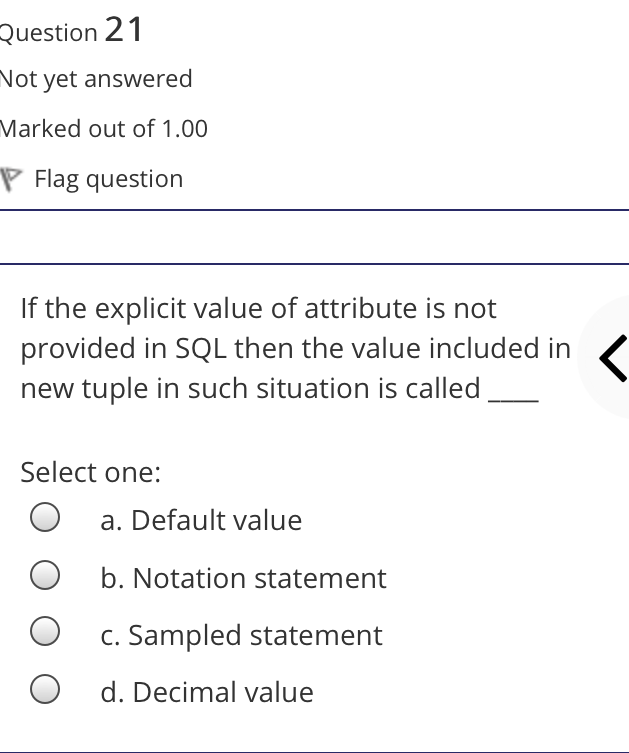
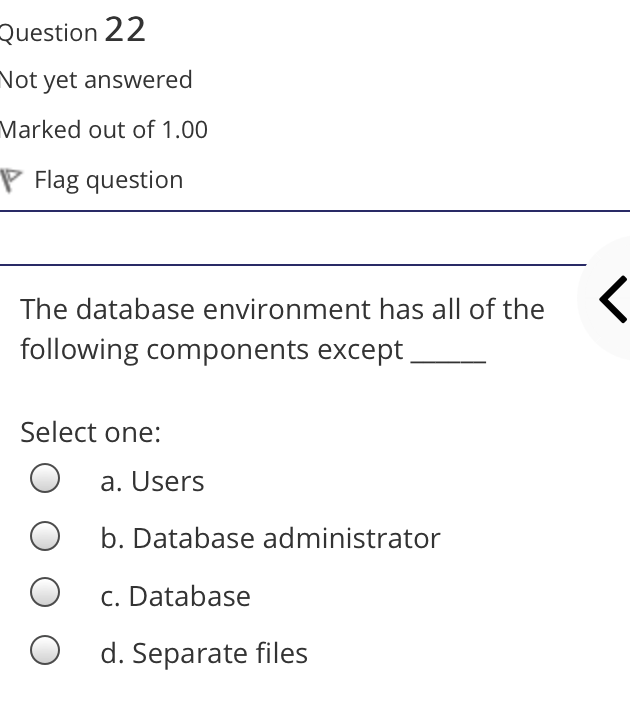
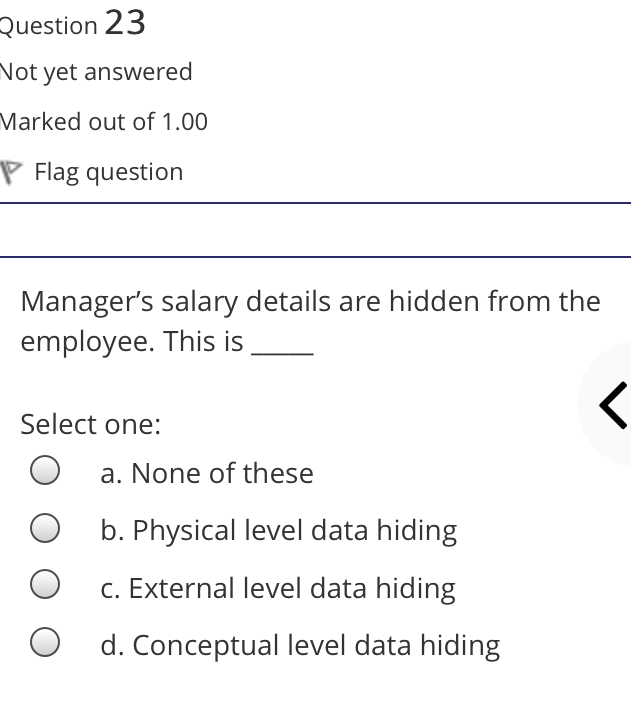
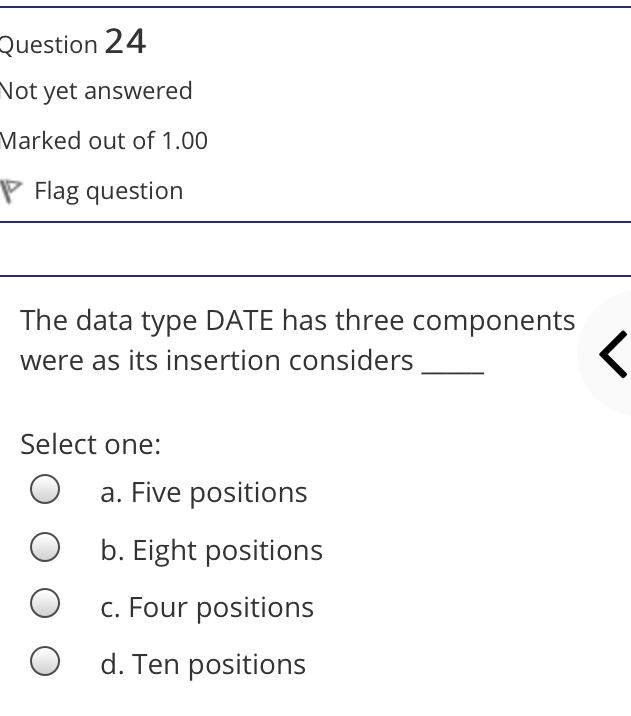
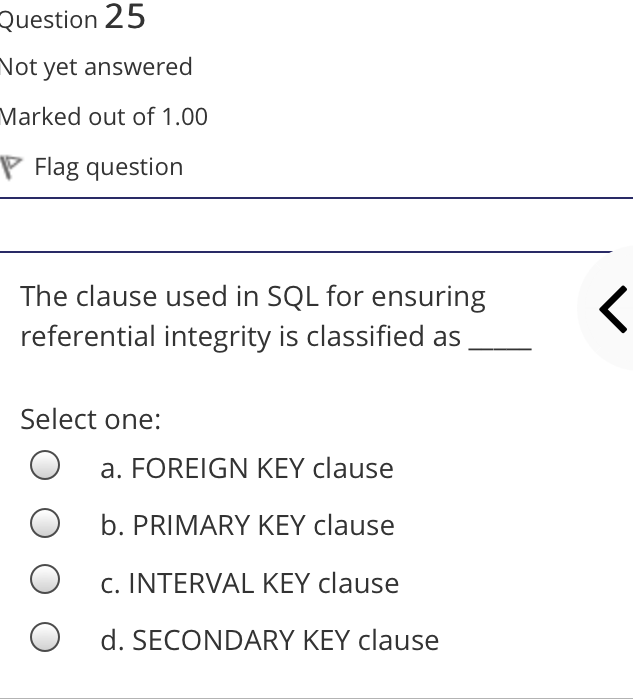
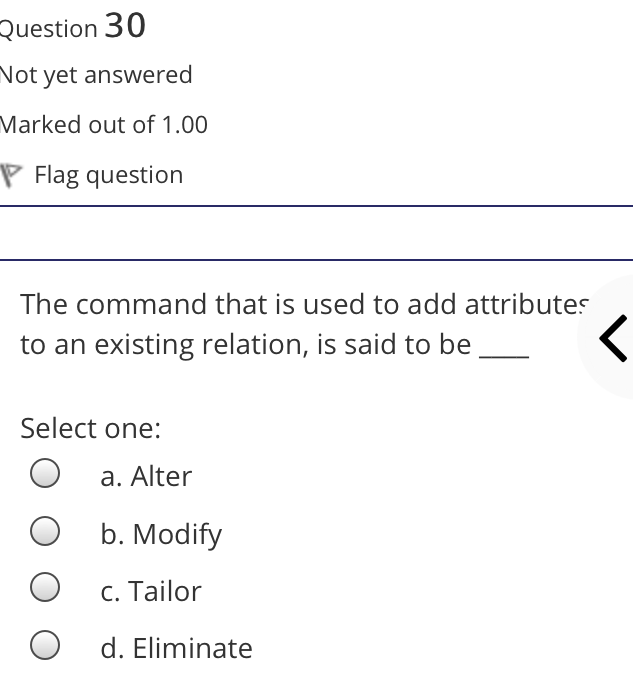
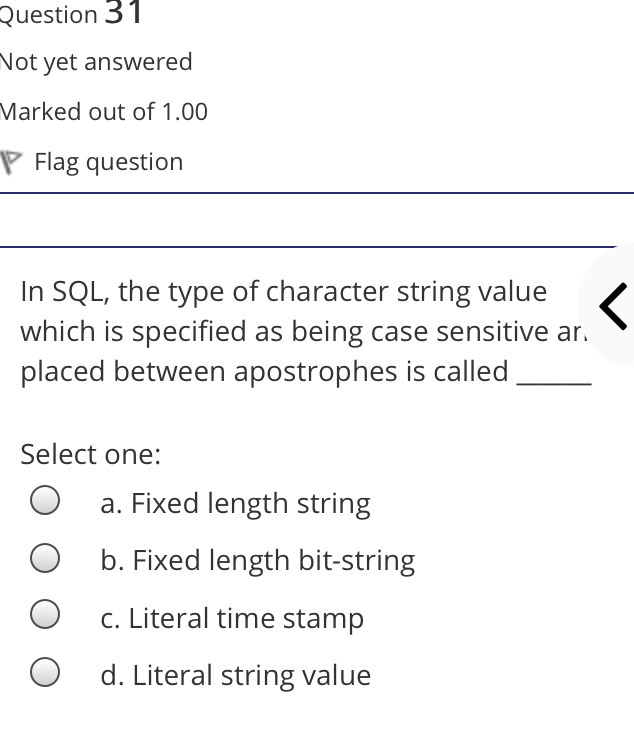
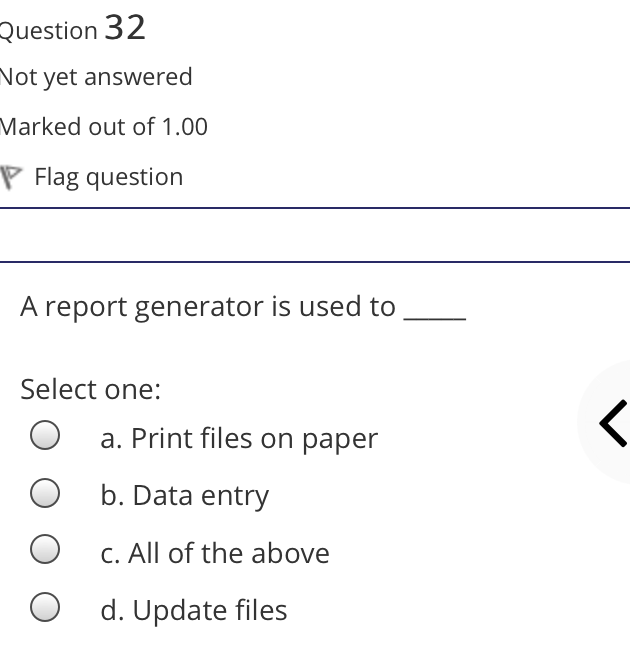
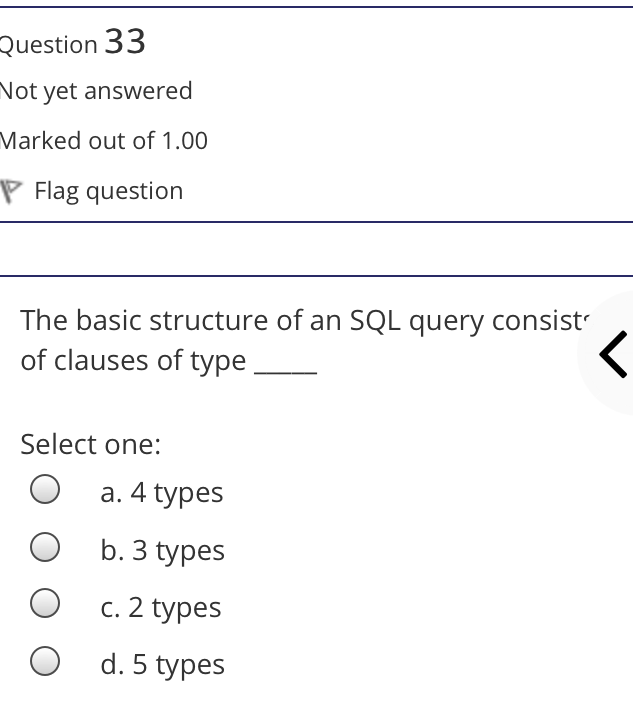
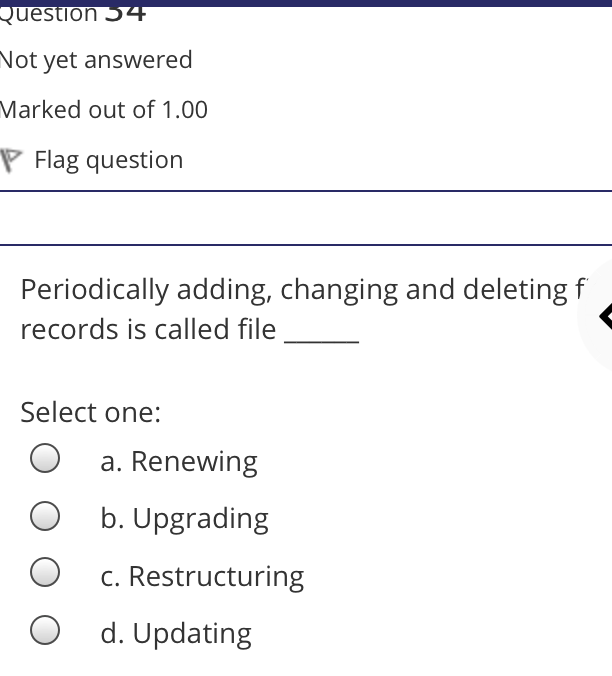
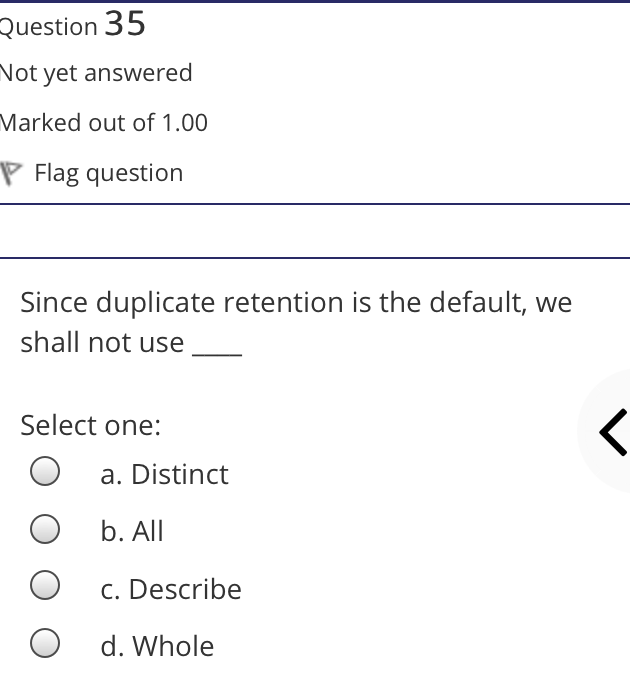
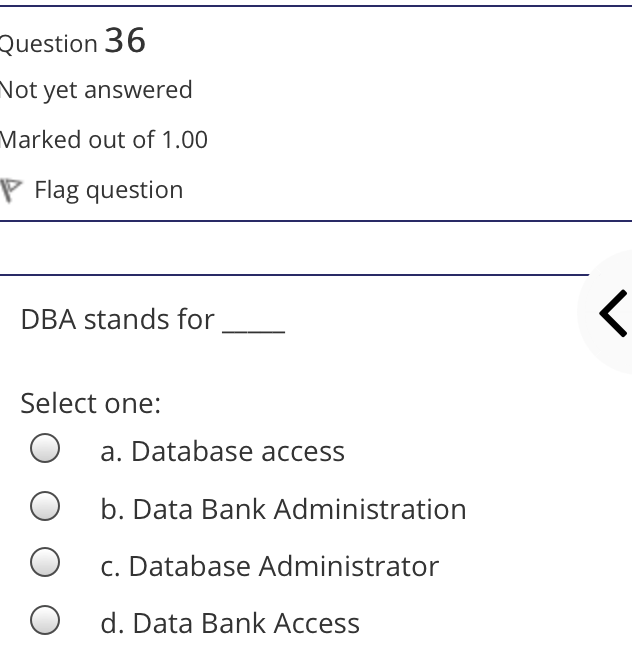
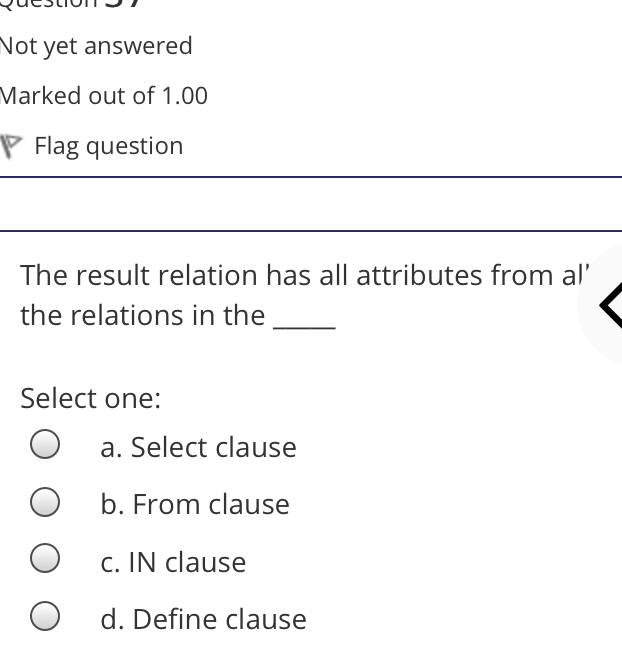
The syntax of a user query is verified by Select one: a. Query optimizer Ob. None of the above c. DBA Od. Parser Question 2 Not yet answered Marked out of 1.00 Flag question Administrative supervision of database activities is the responsibility of the Select one: O a. DB Manager b. Database administrator c. DP Administrator d. DP Manager Question 3 Not yet answered Marked out of 1.00 Flag question Data integrity means < Select one: a. Ensuring correctness and consistency of data b. Providing first access to stored data c. Providing data sharing d. None of the above Question 4 Not yet answered Marked out of 1.00 Flag question The term that allows specification of not or a set of relations, but also information about each relation, is known as Select one: a. Data declaration language b. Data declaration language c. Data manipulation language d. Data definition language Question 5 Not yet answered Marked out of 1.00 Flag question In order to use a DBMS, it is important to understand Select one: a. Both A and B Ob. The physical schema c. One subschema d. All subschemas that the system supports Question 6 Not yet answered Marked out of 1.00 Flag question What is used for database security. Select one: a. All of the above b. Finger print c. A view d. Data encryption Question 7 Not yet answered Marked out of 1.00 Flag question Which one is an incorrect statement about view Select one: a. DROP VIEW is used to dispose it b. A view is derived from other tables c. It can be updated like a table d. All are correct statement Question 8 Not yet answered Marked out of 1.00 Flag question Object based data models are used in describing the abstraction of the following level Select one: a. Only physical b. Physical and conceptual c. Conceptual and view d. None of the above Question 9 Not yet answered Marked out of 1.00 Flag question DBMS is used to Select one: a. Establish relationships among different files b. Maintain data integrity c. All of the above d. Eliminate data redundancy Question 10 Not yet answered Marked out of 1.00 Flag question Which of the following could cause data to unavailable Select one: a. Data becoming lost or inaccurate b. Planned database c. All of the above d. The database server Question 11 Not yet answered Marked out of 1.00 Flag question The person who implements the specifications of the database programs is considered as Select one: Oa. All of the above b. Application programmers c. Software developers d. Software engineers Question 12 Not yet answered Marked out of 1.00 Flag question When comparing a char type with a varchar type, one may expect extra spaces to be added to the < Select one: O a. Both A and B b. None of the above c. Char type d. Varchar type Question 13 Not yet answered Marked out of 1.00 Flag question A traditional data administrator performs which of the following roles Select one: a. Tune database performance b. Protect the security of the database c. Resolves data ownership issues d. Establish backup and recovery procedures Question 14 Not yet answered Marked out of 1.00 Flag question The constraints that are applied on individual tuples and are verified whenever any tuple i modified or new tuple is inserted are callec Select one: a. Scale based constraints b. Precision based constraints c. Language based constraints O d. Tuple based constraints O Question 15 Not yet answered Marked out of 1.00 Flag question Which of these is not TRUE in case of responsibilities of Database Administrator Select one: O a. Data entry in to the database b. All the above statements are true c. Acquiring hardware and software resources d. Authorizing access to database Question TO Not yet answered Marked out of 1.00 Flag question Which of the following are data security consideration Select one: O a. Archival storage b. All of the above c. Backups d. Disposal of data Question 17 Not yet answered Marked out of 1.00 Flag question All tuples in the relation are assigned null as the value for the new attribute, in the < Select one: a. Eliminate command b. Alter command c. Modify command d. Tailor command Question 18 Not yet answered Marked out of 1.00 Flag question The data type which can be fixed length or varying length as CHAR (n) and VARCHAR (r respectively is classified as Select one: a. Schema string O b. Character-string c. Ternary string d. Binary string Question 19 Not yet answered Marked out of 1.00 Flag question Which of the following is part of an administrative policy to secure a database Select one: a. Ensure appropriate responses rates are in external maintenance agreements r O b. Limiting particular areas within a building to only authorized people c. Authentication policies d. All the above Question 20 Not yet answered Marked out of 1.00 Flag question If the referential integrity constraint is violated then the specific action clause attached by the database designers other than by default action is classified as Select one: Oa. Primary key triggered action b. Foreign key triggered action c. Decimal triggered action d. Referential triggered action Question 21 Not yet answered Marked out of 1.00 Flag question If the explicit value of attribute is not provided in SQL then the value included in new tuple in such situation is called Select one: a. Default value b. Notation statement c. Sampled statement d. Decimal value Question 22 Not yet answered Marked out of 1.00 Flag question The database environment has all of the following components except. Select one: a. Users b. Database administrator c. Database d. Separate files Question 23 Not yet answered Marked out of 1.00 Flag question Manager's salary details are hidden from the employee. This is Select one: O a. None of these b. Physical level data hiding c. External level data hiding d. Conceptual level data hiding Question 24 Not yet answered Marked out of 1.00 Flag question The data type DATE has three components were as its insertion considers Select one: Oa. Five positions b. Eight positions c. Four positions d. Ten positions r Question 25 Not yet answered Marked out of 1.00 Flag question The clause used in SQL for ensuring referential integrity is classified as Select one: a. FOREIGN KEY clause b. PRIMARY KEY clause C. INTERVAL KEY clause O d. SECONDARY KEY clause Question 26 Not yet answered Marked out of 1.00 Flag question Top level manager users Select one: a. Both A and B b. External information only c. Internal information only d. None of these r Question 27 Not yet answered Marked out of 1.00 Flag question Poor data administration can lead to which of the following. < Select one: O a. Missing data elements b. A single definition of the same data entity c. All of the above d. Familiarity with existing data Question 29 Not yet answered Marked out of 1.00 Flag question Which of the following will not help us for the secure disposal of data Select one: a. Keep careful records b. Destroy access c. Destroy the data d. Destroy the device Question 28 Not yet answered Marked out of 1.00 Flag question In database management systems, the rec which contains all the data regarding tuples of database is called Select one: a. Environment record b. Connection record c. Description record d. Statement record Question 30 Not yet answered Marked out of 1.00 Flag question The command that is used to add attributes to an existing relation, is said to be < Select one: a. Alter b. Modify c. Tailor d. Eliminate Question 31 Not yet answered Marked out of 1.00 Flag question In SQL, the type of character string value which is specified as being case sensitive ar. placed between apostrophes is called Select one: O a. Fixed length string b. Fixed length bit-string c. Literal time stamp d. Literal string value Question 32 Not yet answered Marked out of 1.00 Flag question A report generator is used to Select one: a. Print files on paper b. Data entry c. All of the above d. Update files Question 33 Not yet answered Marked out of 1.00 Flag question The basic structure of an SQL query consist of clauses of type Select one: a. 4 types b. 3 types c. 2 types d. 5 types Question 54 Not yet answered Marked out of 1.00 Flag question Periodically adding, changing and deleting f records is called file. Select one: a. Renewing b. Upgrading c. Restructuring Od. Updating Question 35 Not yet answered Marked out of 1.00 Flag question Since duplicate retention is the default, we shall not use Select one: a. Distinct b. All c. Describe d. Whole Question 36 Not yet answered Marked out of 1.00 Flag question DBA stands for Select one: a. Database access b. Data Bank Administration c. Database Administrator d. Data Bank Access Not yet answered Marked out of 1.00 Flag question The result relation has all attributes from al' the relations in the Select one: a. Select clause b. From clause c. IN clause d. Define clause Question 38 Not yet answered Marked out of 1.00 Flag question In Standard Query Language, the data types included are Select one: a. Time stamp b. Bit-string c. All of the above d. Character string Question 39 Not yet answered Marked out of 1.00 Flag question The general purpose programming languag such as COBOL and ADA is classified as Select one: O a. Client language b. Referential language c. Server language d. Host language Question 40 Not yet answered Marked out of 1.00 Flag question The level of data abstraction which describ how the data is actually stored is Select one: O a. None of these b. Conceptual level c. Physical level d. File level Question 41 Not yet answered Marked out of 1.00 Flag question What is true about data security Select one: a. Data security requires system managers to reduce unauthorized access to the system by building physical arrangements and software checks b. Data security is the protection of programs and data in computers and communication systems against unauthorized access c. It refers to the right of individuals or organizations to deny or restrict the collection and use of information d. All of the above Question 42 Not yet answered Marked out of 1.00 Flag question Data security threats include Select one: a. Hardware protection b. Fraudulent manipulation of data c. All of the above d. Privacy invasion Question 43 Not yet answered Marked out of 1.00 Flag question Which one of the following design is both software and hardware independent Select one: Oa. None of the above b. Conceptual c. Logical Od. Physical Question 44 Not yet answered Marked out of 1.00 Flag question Prevention of access to the database by unauthorized users is referred to as Select one: a. Integrity b. Reliability c. Security Od. Productivity Question 45 Not yet answered Marked out of 1.00 Flag question Collection of information stored in a databa at a particular moment is Select one: O a. View b. Instance c. None of the above d. Schema Question 46 Not yet answered Marked out of 1.00 Flag question is responsible for using the database remains in a consistent state despite system failure Select one: a. Storage manager b. Sophisticated c. Transaction manager d. End user Question 48 Not yet answered Marked out of 1.00 Flag question A set of objects that share a common structure and a common behavior is called Select one: a. Class b. Entity c. Object d. None of these Question 47 Not yet answered Marked out of 1.00 Flag question Which one is lowest level data model Select one: Oa. External data model b. Physical data model c. Logical data model Od. None of the above Question 49 Not yet answered Marked out of 1.00 Flag question The query for finding the department nam of all instructors, is Select one: a. Define dept_name from instructor; b. Define dept_name about instructor; c. Select dept_name about instructor; d. Select dept_name from instructor; Question 50 Not yet answered Marked out of 1.00 Flag question Between the users and the database itself, a DBMS will act as Select one: a. Referee b. Barrier c. Interface d. Obstacle Question 51 Not yet answered Marked out of 1.00 Flag question Data items grouped together for storage purposes are called a Select one: a. Record b. Title c. List d. String Question 52 Not yet answered Marked out of 1.00 Flag question In the SQL environment, the collection of schemas is classified as Select one: a. Initiator b. Integration c. Catalog d. Value set Question 53 Not yet answered Marked out of 1.00 Flag question For understanding of operations, the clauses must be written in the order Select one: O a. From, select, where b. Select, where, from c. Select, from, where d. From, where, select Question 54 Not yet answered Marked out of 1.00 Flag question If both data and database administration exist in an organization, the database administrator is responsible for which of th following Select one: a. Data modeling b. Metadata c. All of the above d. Database design Question 55 Not yet answered Marked out of 1.00 Flag question Which of the following are the properties o entities Select one: O a. Groups b. Attributes c. Switchboards d. Table Question 56 Not yet answered Marked out of 1.00 Flag question The referential triggered action clause in Standard Query Language is attached to constraint called Select one: a. Interval notation constraint b. Foreign key constraint c. Stamped key constraint d. Primary key constraint Question 57 Not yet answered Marked out of 1.00 Flag question Which of these is not a database object Select one: O a. Sequence b. Trigger c. Index d. Cursor Question 58 Not yet answered Marked out of 1.00 Flag question Authentication refers to Select one: O O < a. Methods of restricting user access to system b. Controlling access to portions of database c. All of the above d. Controlling the operation on the data Question 59 Not yet answered Marked out of 1.00 Flag question A data warehouse administrator is concerned with which of the following Select one: O a. The time to make a decision and th typical roles of a database administrator < b. The typical roles of a data administrator and redesigning existing applications c. The typical roles of a database administrator and redesigning existing applications Od. The time to make a decision but not the typical roles of a database administrator Question 60 Not yet answered Marked out of 1.00 Flag question A schema describes Select one: a. Record and files b. Data elements c. Record relationship d. All of the above
Step by Step Solution
★★★★★
3.43 Rating (169 Votes )
There are 3 Steps involved in it
Step: 1
1 The syntax of a user query is verified by ANS Dparser 2 The administrative supervision of database activities is the responsibility of ANS BDatabase administrator 3 Data integrity means ANS AEnsurin...
Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


