Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Question 3 ( a ) For a particular TCP session the current round - trip time, R T T c u r , is 5
Question
a For a particular TCP session the current roundtrip time, is and at a particular
moment of time the measured acknowledgement from a data segment is after
i Apply the Jacobson algorithm to find the updated value Assume in
calculations the smoothing factors
ii Determine the values of the current and the updated mean deviations if the
calculated updated value of the Retransmission TimeOut is
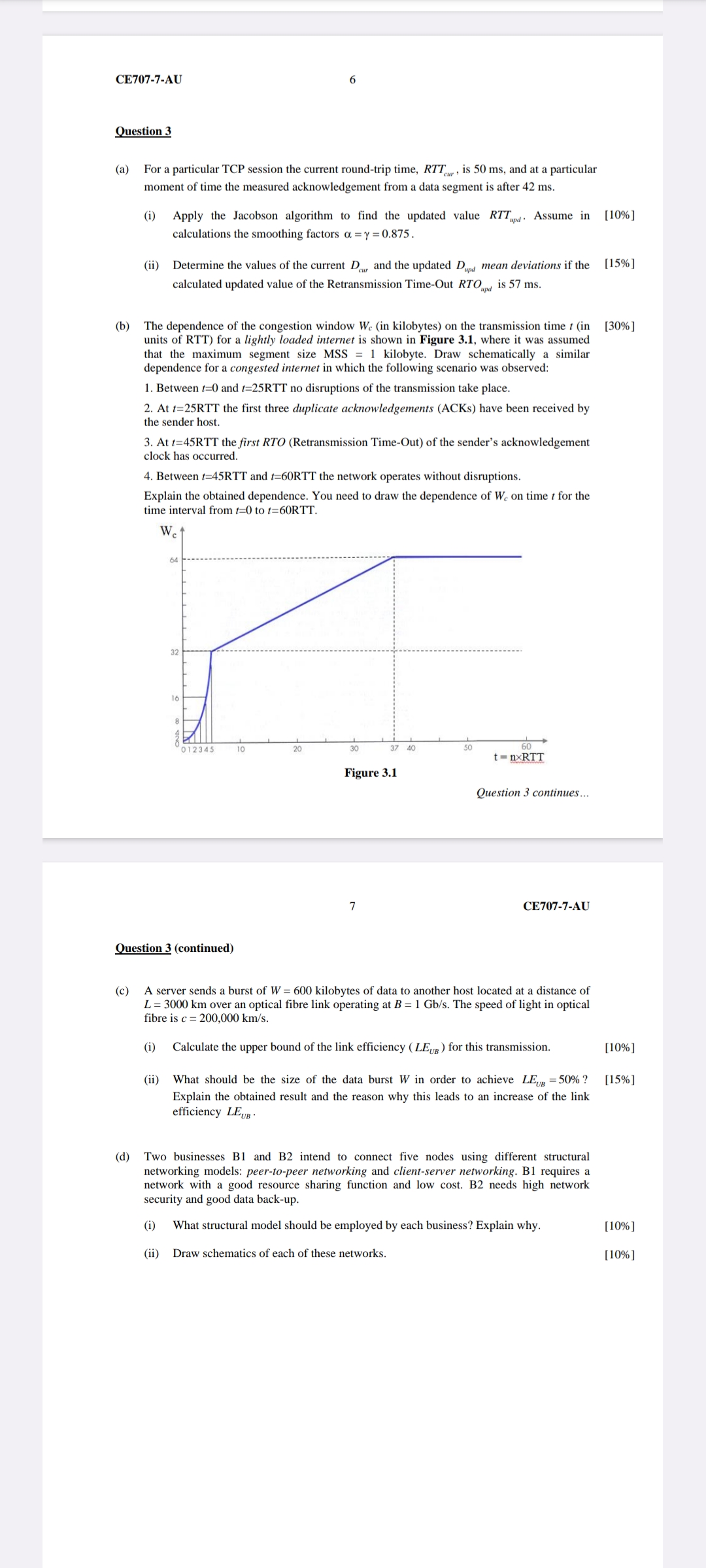
b The dependence of the congestion window in kilobytes on the transmission time in
units of RTT for a lightly loaded internet is shown in Figure where it was assumed
that the maximum segment size MSS kilobyte. Draw schematically a similar
dependence for a congested internet in which the following scenario was observed:
Between and RTT no disruptions of the transmission take place.
At RTT the first three duplicate acknowledgements ACKs have been received by
the sender host.
At RTT the first RTO Retransmission TimeOut of the senders acknowledgement
clock has occurred.
Between and the network operates without disruptions.
Explain the obtained dependence. You need to draw the dependence of on time for the
time interval from to RTT
Question continued
c A server sends a burst of kilobytes of data to another host located at a distance of
over an optical fibre link operating at The speed of light in optical
fibre is
i Calculate the upper bound of the link efficiency for this transmission.
ii What should be the size of the data burst in order to achieve
Explain the obtained result and the reason why this leads to an increase of the link
efficiency
d Two businesses B and B intend to connect five nodes using different structural
networking models: peertopeer networking and clientserver networking. B requires a
network with a good resource sharing function and low cost. B needs high network
security and good data backup
i What structural model should be employed by each business? Explain why.
ii Draw schematics of each of these networks.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


