Answered step by step
Verified Expert Solution
Question
1 Approved Answer
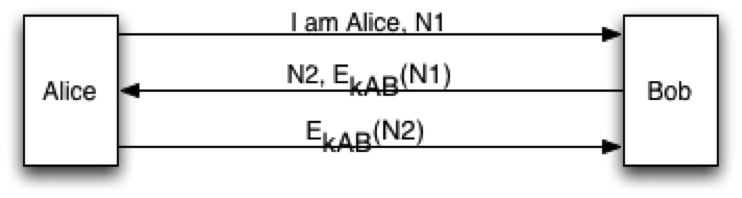
Reflection attack: Suppose Oscar wants to impersonate Alice to Bob using the protocol in Figure 2. He starts the protocol by claiming to be Alice
Reflection attack: Suppose Oscar wants to impersonate Alice to Bob using the protocol in Figure 2. He starts the protocol by claiming to be Alice and sending a nonce N1. When he gets the response and the challenge N2, he cannot proceed further. However, note that he has managed to get Bob to encrypt the nonce N1 for him using the key kAB. Next suppose he starts a second session with Bob, but uses N2 as the initial challenge
a. Show the steps by which he can successfully complete the first session.
b. How can this attack be foiled?
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


