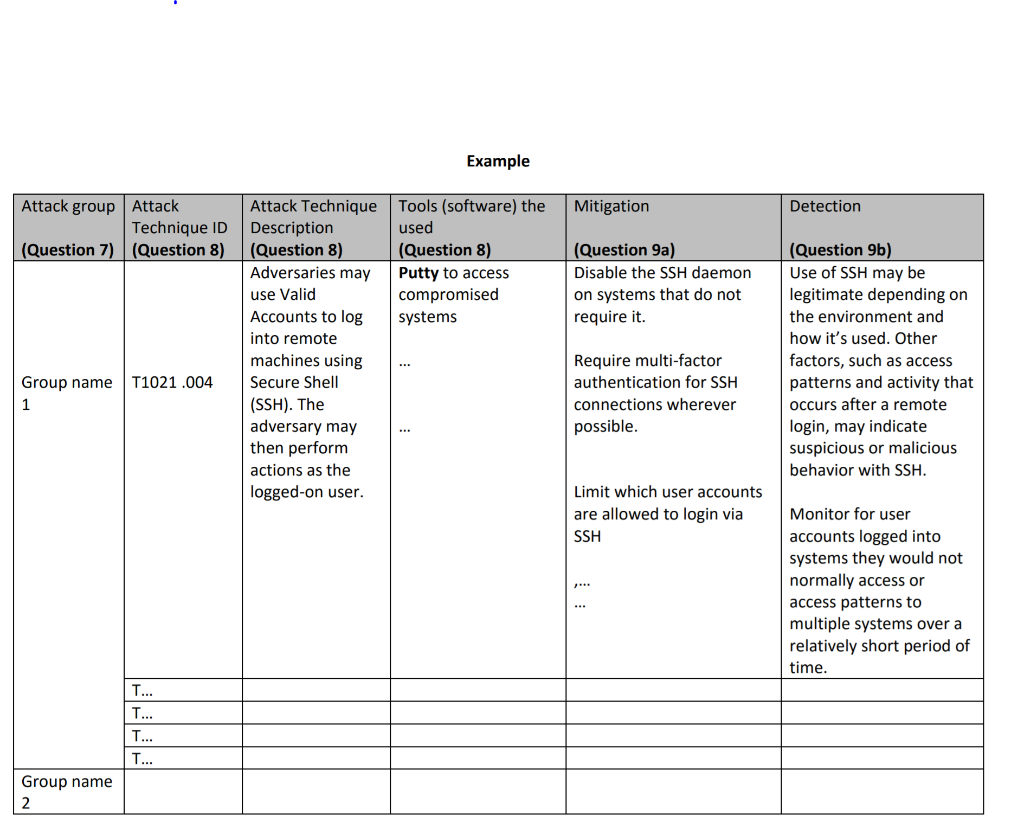
Saudi Arabia has witnessed series of cyberattacks in the past few years, due to its economic and political positions."1 In fact, the giant oil company, Saudi Aramco, has been hit by cyberattacks multiple times in the past 10 years. Use the Internet articlesews, Aramco website, and ATT&CK MITRE to answer the following questions about the topic: 1. How many times the company has been hit by cyberattacks in the past 10 years? And When? 2. What is/are the type of these cyberattacks? 3. What is the motivation of these cyberattacks? 4. What is the vulnerability they had exploited? 5. What is the impact of this cyberattack to Aramco? 6. Did this cyberattack hit any other country? (if, yes, list them) 7. Find the potential cyberattack groups that target the oil sectors in middle east (from MITRE ATT&CK)? 8. What techniques and tools they used? Select one attack group and list 5 different techniques they used, describe each one and list tools they used for each technique. 9. If you are a part of the cybersecurity team in Aramco, (from MITRE ATT&CK) a. What do you suggest to mitigate the impact of such cyberattacks? b. How can you detect such cyberattacks? Answer questions 7, 8 and 9 in a table (see an example next page) Example Mitigation Detection Attack group Attack Technique ID (Question 7) (Question 8) Tools (software) the used (Question 8) Putty to access compromised systems (Question 9a) Disable the SSH daemon on systems that do not require it. Attack Technique Description (Question 8) Adversaries may use Valid Accounts to log into remote machines using Secure Shell (SSH). The adversary may then perform actions as the logged-on user. (Question 9b) Use of SSH may be legitimate depending on the environment and how it's used. Other factors, such as access patterns and activity that occurs after a remote login, may indicate suspicious or malicious behavior with SSH. T1021.004 Require multi-factor authentication for SSH connections wherever possible. Group name 1 Limit which user accounts are allowed to login via SSH Monitor for user accounts logged into systems they would not normally access or access patterns to multiple systems over a relatively short period of time. T... T... T... T... Group name








