Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Section 3: iptables Firewall Configuration Step 1: From Netlab, access your Linux Server 2. You will use this vm in this section to test
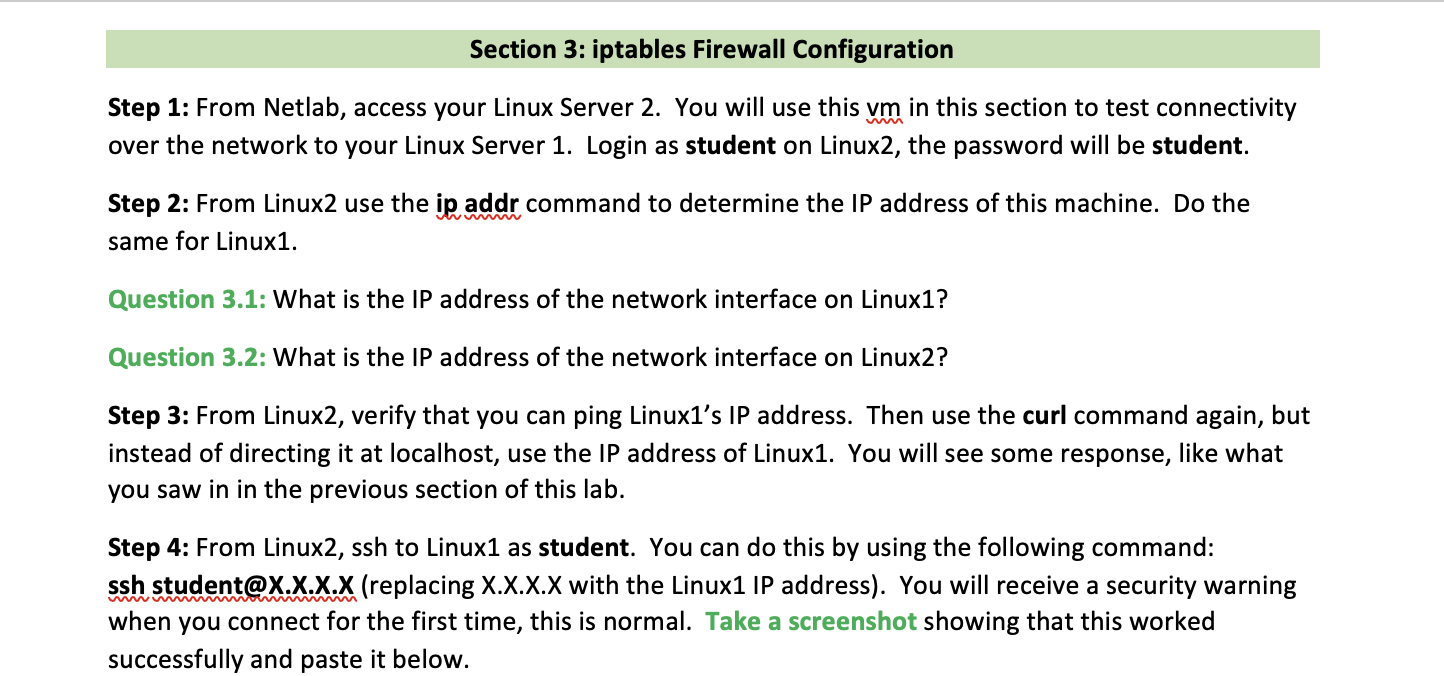
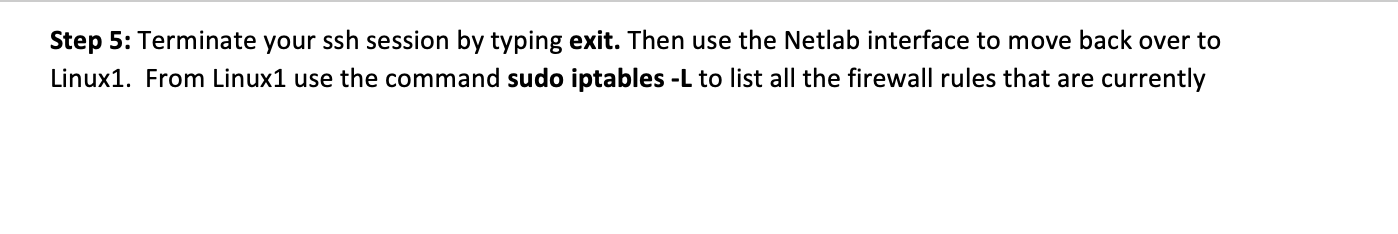
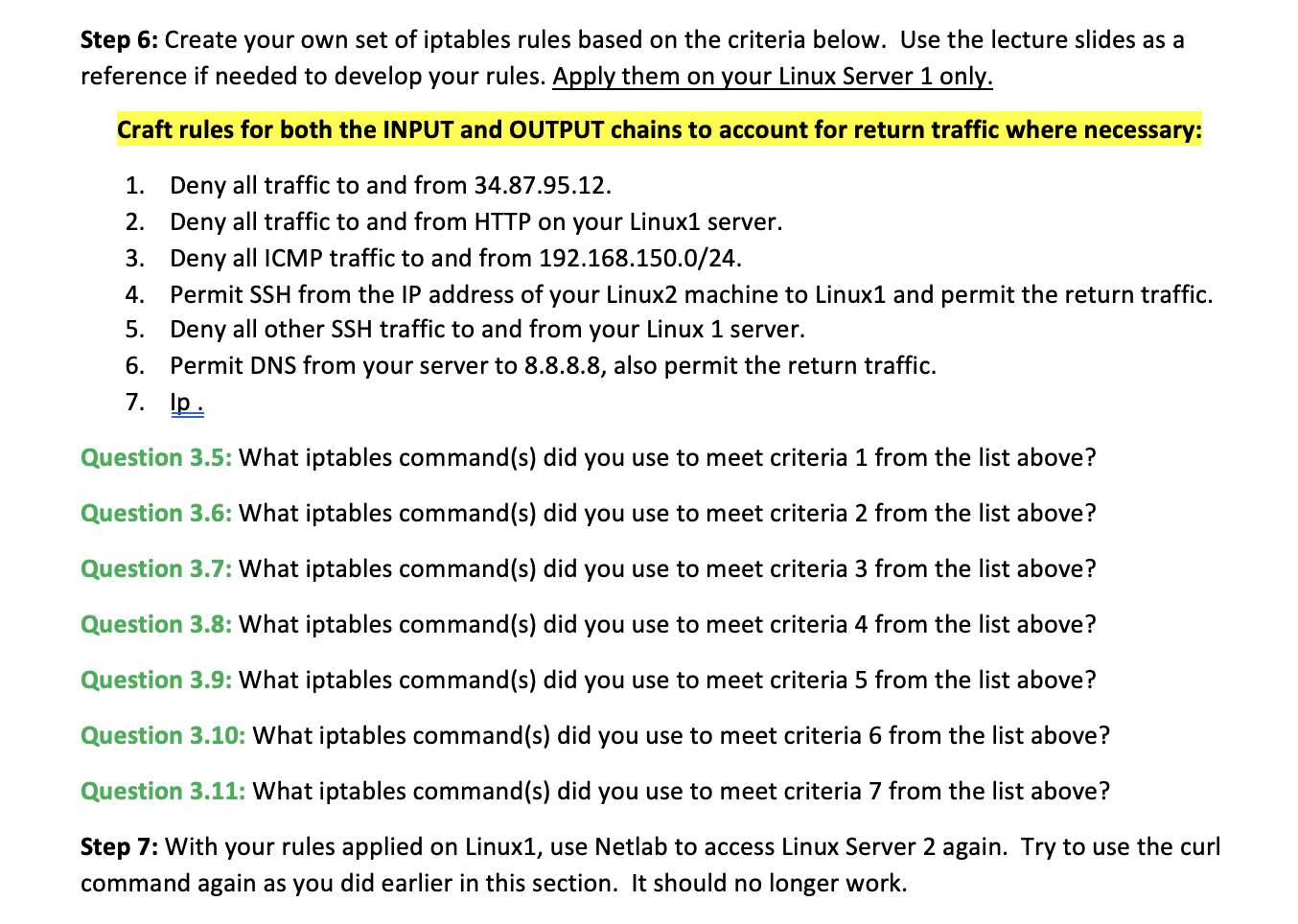
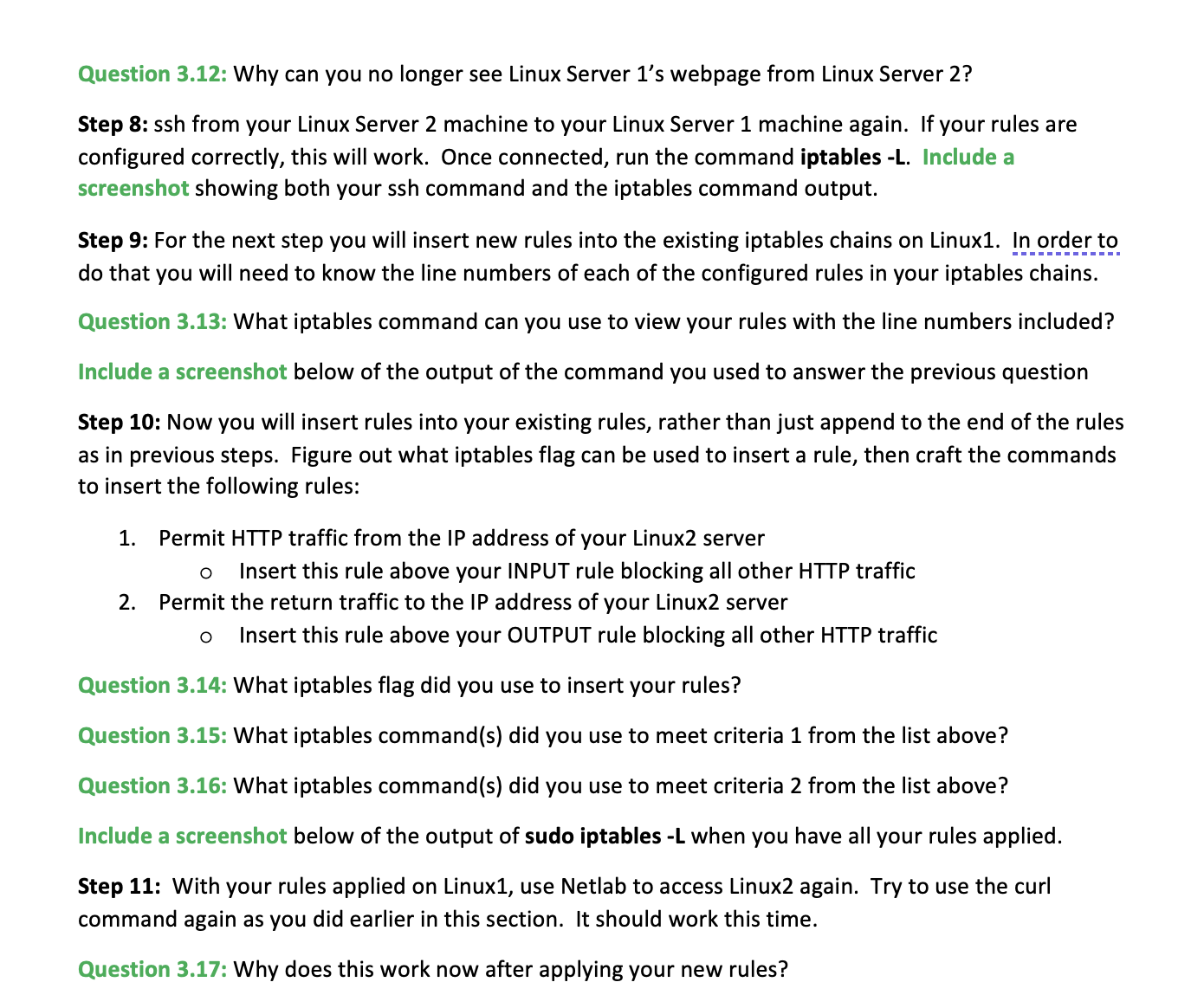
Section 3: iptables Firewall Configuration Step 1: From Netlab, access your Linux Server 2. You will use this vm in this section to test connectivity over the network to your Linux Server 1. Login as student on Linux2, the password will be student. Step 2: From Linux2 use the ip addr command to determine the IP address of this machine. Do the same for Linux1. Question 3.1: What is the IP address of the network interface on Linux1? Question 3.2: What is the IP address of the network interface on Linux2? Step 3: From Linux2, verify that you can ping Linux1's IP address. Then use the curl command again, but instead of directing it at localhost, use the IP address of Linux1. You will see some response, like what you saw in in the previous section of this lab. Step 4: From Linux2, ssh to Linux1 as student. You can do this by using the following command: ssh student@X.X.X.X (replacing X.X.X.X with the Linux1 IP address). You will receive a security warning when you connect for the first time, this is normal. Take a screenshot showing that this worked successfully and paste it below. Step 5: Terminate your ssh session by typing exit. Then use the Netlab interface to move back over to Linux1. From Linux1 use the command sudo iptables -L to list all the firewall rules that are currently Step 6: Create your own set of iptables rules based on the criteria below. Use the lecture slides as a reference if needed to develop your rules. Apply them on your Linux Server 1 only. Craft rules for both the INPUT and OUTPUT chains to account for return traffic where necessary: 1. Deny all traffic to and from 34.87.95.12. 2. Deny all traffic to and from HTTP on your Linux1 server. 3. Deny all ICMP traffic to and from 192.168.150.0/24. 4. Permit SSH from the IP address of your Linux2 machine to Linux1 and permit the return traffic. Deny all other SSH traffic to and from your Linux 1 server. 5. 6. Permit DNS from your server to 8.8.8.8, also permit the return traffic. 7. lp. Question 3.5: What iptables command(s) did you use to meet criteria 1 from the list above? Question 3.6: What iptables command (s) did you use to meet criteria 2 from the list above? Question 3.7: What iptables command(s) did you use to meet criteria 3 from the list above? Question 3.8: What iptables command(s) did you use to meet criteria 4 from the list above? Question 3.9: What iptables command(s) did you use to meet criteria 5 from the list above? Question 3.10: What iptables command(s) did you use to meet criteria 6 from the list above? Question 3.11: What iptables command(s) did you use to meet criteria 7 from the list above? Step 7: With your rules applied on Linux1, use Netlab to access Linux Server 2 again. Try to use the curl command again as you did earlier in this section. It should no longer work. Question 3.12: Why can you no longer see Linux Server 1's webpage from Linux Server 2? Step 8: ssh from your Linux Server 2 machine to your Linux Server 1 machine again. If your rules are configured correctly, this will work. Once connected, run the command iptables -L. Include a screenshot showing both your ssh command and the iptables command output. Step 9: For the next step you will insert new rules into the existing iptables chains on Linux1. In order to do that you will need to know the line numbers of each of the configured rules in your iptables chains. Question 3.13: What iptables command can you use to view your rules with the line numbers included? Include a screenshot below of the output of the command you used to answer the previous question Step 10: Now you will insert rules into your existing rules, rather than just append to the end of the rules as in previous steps. Figure out what iptables flag can be used to insert a rule, then craft the commands to insert the following rules: 1. Permit HTTP traffic from the IP address of your Linux2 server O Insert this rule above your INPUT rule blocking all other HTTP traffic 2. Permit the return traffic to the IP address of your Linux2 server O Insert this rule above your OUTPUT rule blocking all other HTTP traffic Question 3.14: What iptables flag did you use to insert your rules? Question 3.15: What iptables command(s) did you use to meet criteria 1 from the list above? Question 3.16: What iptables command(s) did you use to meet criteria 2 from the list above? Include a screenshot below of the output of sudo iptables -L when you have all your rules applied. Step 11: With your rules applied on Linux1, use Netlab to access Linux2 again. Try to use the curl command again as you did earlier in this section. It should work this time. Question 3.17: Why does this work now after applying your new rules?
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


