Question: Section A (True False) - 30 marks 8. Redundancy is one of the recovery methods in data security breaches Justification: Please tick (V) in the
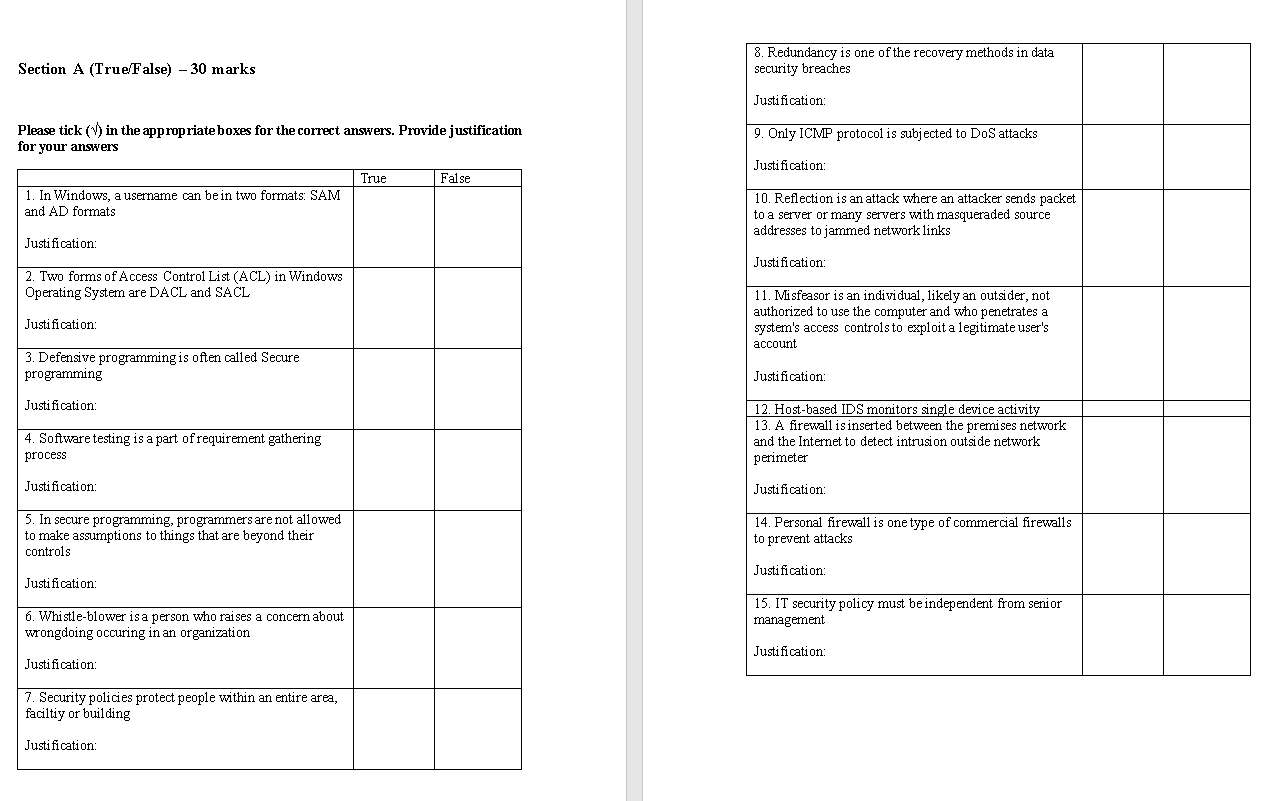
Section A (True False) - 30 marks 8. Redundancy is one of the recovery methods in data security breaches Justification: Please tick (V) in the appropriate boxes for the correct answers. Provide justification for your answers 9. Only ICMP protocol is subjected to DoS attacks Justification: True False 1. In Windows, a username can be in two formats: SAM and AD formats 10. Reflection is an attack where an attacker sends packet to a server or many servers with masqueraded source addresses to jammed network links Justification: Justification: 2. Two forms of Access Control List (ACL) in Windows Operating System are DACL and SACL Justification: 11. Misfeasor is an individual, likely an outsider, not authorized to use the computer and who penetrates a systern's access controls to exploit a legitimate user's account 3. Defensive programming is often called Secure programming Justification: Justification: 4. Software testing is a part of requirement gathering process 12. Host-based IDS monitors single device activity 13. A firewall is inserted between the premises network and the Internet to detect intrusion outside network perimeter Justification Justification: 5. In secure programming, programmers are not allowed to make assumptions to things that are beyond their controls 14. Personal firewall is one type of commercial firewalls to prevent attacks Justification Justification: 6. Whistle-blower is a person who raises a concern about wrongdoing occuring in an organization 15. IT security policy must be independent from senior management Justification: Justification: 7. Security policies protect people within an entire area, faciltiy or building Justification
Step by Step Solution
There are 3 Steps involved in it

Get step-by-step solutions from verified subject matter experts


