subject: Management Information System
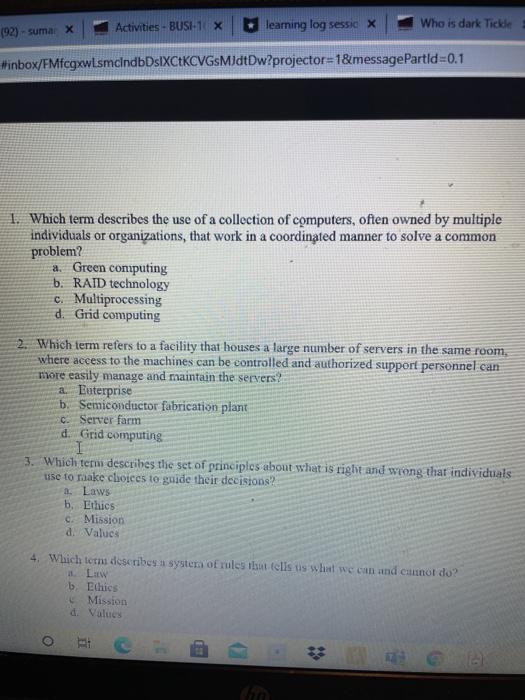
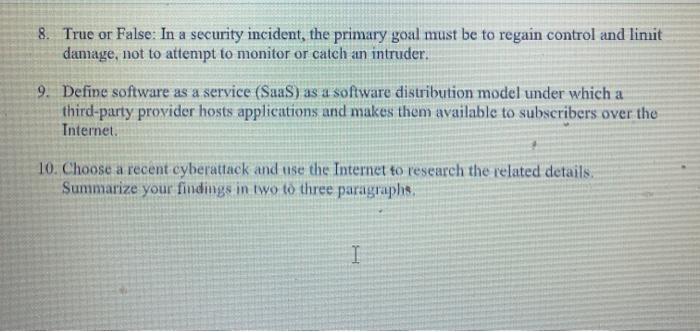
(92) - sumax Activities - BUSI-1 X learning log sessio X Who is dark Tickle #inbox/FMfcgxw.smclndbDsiXCEKCVGsM]dtDw?projector=1&messagePartid=0.1 1. Which term describes the use of a collection of computers, often owned by multiple individuals or organizations, that work in a coordinated manner to solve a common problem? a. Green computing b. RAID technology c. Multiprocessing d. Grid computing 2. Which term refers to a facility that houses a large number of servers in the same room, where access to the machines can be controlled and authorized support personnel can more easily manage and maintain the servers? 2. Euterprise b. Semiconductor fabrication plant c. Server farm d. Grid computing 3. Which term describes the set of principles about what is right and wong that individuals use to make choices to guide their decisions? 1. Laws b. Ethics C. Mission d. Values 4. Which lotni describes a system of rules that tells us what we can and cannot do? LW bEthics Mission d. Values O Fox (92) - suma X Activities - BUSI-1 X learning log sessic X Who is dark Tickle x blinbox/FMfcgxwlsmeindbDsiXCEKCVGsMJdtDw?projector=1& message Partid=0.1 TIITiki e Mission d Values Open with Google Docs 5. Which term describes a large group of computers that are controlled from one or more remote locations by hackers without the knowledge or consent of their legitimate owners? e Intrusion detection system (IDS) f. Virtual private network (VPN) g. Botnet h. Proxy server 6. Which three terms are referenced in the CTA security triad? a. Confidentiality, integrity, and auditability b. Confidentiality, integrity, and availability 6. Certainty integrity and authenticity d. Certainty integrity and auditability 7. Which term refers to an attack that takes place before the security community becomes aware of and fixes a security vulnerability": 3. Botnet 6. Ransomware 8. True or False: In a security incident, the primary goal must be to regain control and linuit damage, not to attempt to monitor or catch an intruder. 9. Define software as a service (SaaS) as a software distribution model under which a third-party provider hosts applications and makes them available to subscribers over the Internet. 10. Choose a recent cyberattack and use the Internet to research the related details. Summarize your findings in two to three paragraphs