Answered step by step
Verified Expert Solution
Question
1 Approved Answer
The Caesar cipher is a (very insecure) method for encrypting text dating back to the Romans. It is the same alphabetic shift cipher as is
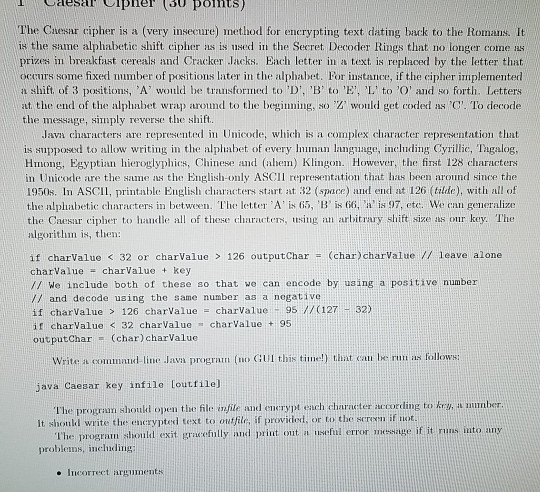
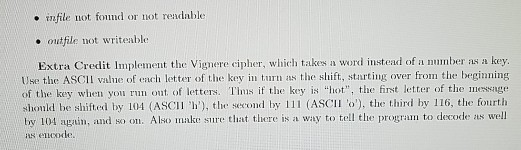
The Caesar cipher is a (very insecure) method for encrypting text dating back to the Romans. It is the same alphabetic shift cipher as is used in the Secret Decoder Rings that no longer come as prizes in breakfast cereals and Cracker Jacks. Each letter in a text is replaced by the letter that occurs some fixed number of positions later in the alphabet. For instance, if the cipher implemented a shift of 3 positions, A' would be transformed to 'D', 'B' to 'E, L' to 'O' and so forth. Letters at the end of the alphabet wrap around to the beginning, so 'Z would get coded as C'. To decode the message, snply reverse the shift ava characters are represented in Unicode, which is a complex character representation that is supposed to allow writing in the alphabet of every man langnage, including Cyrillic, Tagalog Hmong, Egyptian hieroglyphics, Chinese and (ahe) Klingon. However, the finst 128 characters in Unicode are the same as the English-only ASCII representation that has been around since the 1950s. In ASCII, printable English characters start at 32 (space) and end at 126 (tilde), with all of the alphabetic characters in between. The letter A' is 65, 'B is 66, a' is 97, ete. We an generalize the Caesar cipher to handle all of these characters, sg an arbitrary shift size as our key. The algorithm is, then: if charValue 126 charvalue charvalue - 95 // (127 32) if charValue 32 charValue charValue95 outputChar (char) charValue Write a command-line Java program (no GUI this tinel) thint can be run as follows java Caesar key infile loutfile] lhe prograam shoukd open the file infile and enerypt each character according to key, a mumber It should write the encrypted text to outfile, if providod, or to the screen if not l'he program should exit gracefilly and print ont a uswful error message if it nis into any problems, incuding . Ineorrect argumen
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


