The information below is all that was given, it is obtained from a Host Computer
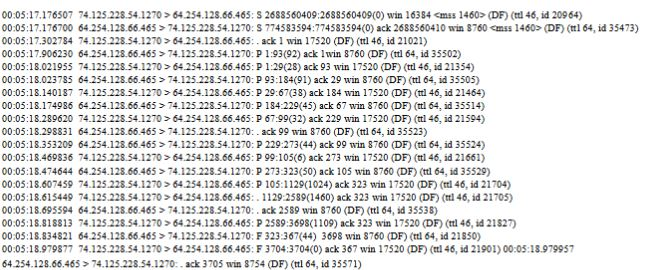
A).What is the application being communicated between these two host? How do you know?
B). Was the entire transaction completed? How do you know?
C).Did this transaction use TCP, UDP or something else? How do you know?
00:0:17,176507 74.125.228.54.1270 64.254.128.66.465: S 2688560409:2688560409(0) win 16384
74.125.228.54.1270: S 774383594:774583594(0) ack 2688560410 win 8760 cmss 1460 (DF) (l 64, id 35473) 00:05:17.302784 74.125.228.54.1270> 64254.128.66.465: ack 1 win 17520 (DF) (ttl 46, id 21021) 00:05: 17.906230 64.254.128.66.465 > 74.125.228.54. 1270: p 1:93(92) ack lwin 8760 (DF) (ttl 64, id 35502) 00:05:18.021955 74.125.228.54.1270> 64 254.123.66.465: P 1:29(28) ack 93 win 17520 (DF) (ttl 46, id 21354) 00:05:18.023785 64254.128.66.465 > 74.125.228.54.1270: P 93:184(91) ack 29 win 8760 (DF (ttl 64, id 35505) 00:05:18.140187 74.125.228.54.1270> 64.254.128.66.465: P 29:6738) ack 184 win 17520 (DF) (tl 46, id 21464) 00:05:18.174986 64.254.128.66465 74.125.22854.1270: P 184:229(45) ack 67 win 8760 (DF) (tl 64, id 35514) 00:05:18.289620 74.125 228.54.1270> 64 254.128.66465: P 67:99(32) ack 229 win 17520 (DF) (tl 46, id 21594) 00:05:18.298831 64.254.128.66465 > 74.125.228.54.1270: ack 99 win 8760 (DF) (ttl 64, id 35523) 00:05:18.353209 64.254.128.66465> 74.125 228.54.1270: P 229:273 44) ack 99 win 8760 (DF) (ttl 64, id 35524) 00:05:18.469836 74.125.228.54.1270 64.254.128.66.465: P 99:105(6) ack 273 win 17520 (DF) (ttl 46, id 21661) 00:05:18.474644 64.254.128.66465 > 74.12522.54.1270: P 273 323 50) ack 105 win 8760 (DF) (l 64, id 35529) 00:05:18.607459 74.125.228.54.1270> 64.254.128.66.465 P 105:1129(1024) ack 323 win 17520 (DF) (ttl46, id 21704) 00:05:18.615449 74.125.228.54.1270>64.254.128.66465:. 1129 2589(1460) ack 323 win 17520 (DF) (i 46, id 21705) 00:05:18.695594 64.254.128.66.46574.125228.54.1270: . ack 2589 win S760 (DF (t 64, id 35538) 00.05:18.818813 74.125.228 54.1270 64.254128.66.465: P 2589:3698(1109) ack 323 win 17520 (DF) (46, id 21827) 00:05:18.834821 64.254.128.66465> 74125.228.54.1270: F 323367(44) 3698 win 8760 (DF) (t 64, id 21850) 00:05:18.979877 74.125.228.54.1270> 64.254.128.66465: F 3704:3704(0) ack 367 win 17520 (DF) (l46, id 21901) 00:05:18.979957 64.254.128.66.465> 74.125.228.54.1270.ack 3705 win 8754 (DF) (ttl 64, id 33571) 00:0:17,176507 74.125.228.54.1270 64.254.128.66.465: S 2688560409:2688560409(0) win 16384 74.125.228.54.1270: S 774383594:774583594(0) ack 2688560410 win 8760 cmss 1460 (DF) (l 64, id 35473) 00:05:17.302784 74.125.228.54.1270> 64254.128.66.465: ack 1 win 17520 (DF) (ttl 46, id 21021) 00:05: 17.906230 64.254.128.66.465 > 74.125.228.54. 1270: p 1:93(92) ack lwin 8760 (DF) (ttl 64, id 35502) 00:05:18.021955 74.125.228.54.1270> 64 254.123.66.465: P 1:29(28) ack 93 win 17520 (DF) (ttl 46, id 21354) 00:05:18.023785 64254.128.66.465 > 74.125.228.54.1270: P 93:184(91) ack 29 win 8760 (DF (ttl 64, id 35505) 00:05:18.140187 74.125.228.54.1270> 64.254.128.66.465: P 29:6738) ack 184 win 17520 (DF) (tl 46, id 21464) 00:05:18.174986 64.254.128.66465 74.125.22854.1270: P 184:229(45) ack 67 win 8760 (DF) (tl 64, id 35514) 00:05:18.289620 74.125 228.54.1270> 64 254.128.66465: P 67:99(32) ack 229 win 17520 (DF) (tl 46, id 21594) 00:05:18.298831 64.254.128.66465 > 74.125.228.54.1270: ack 99 win 8760 (DF) (ttl 64, id 35523) 00:05:18.353209 64.254.128.66465> 74.125 228.54.1270: P 229:273 44) ack 99 win 8760 (DF) (ttl 64, id 35524) 00:05:18.469836 74.125.228.54.1270 64.254.128.66.465: P 99:105(6) ack 273 win 17520 (DF) (ttl 46, id 21661) 00:05:18.474644 64.254.128.66465 > 74.12522.54.1270: P 273 323 50) ack 105 win 8760 (DF) (l 64, id 35529) 00:05:18.607459 74.125.228.54.1270> 64.254.128.66.465 P 105:1129(1024) ack 323 win 17520 (DF) (ttl46, id 21704) 00:05:18.615449 74.125.228.54.1270>64.254.128.66465:. 1129 2589(1460) ack 323 win 17520 (DF) (i 46, id 21705) 00:05:18.695594 64.254.128.66.46574.125228.54.1270: . ack 2589 win S760 (DF (t 64, id 35538) 00.05:18.818813 74.125.228 54.1270 64.254128.66.465: P 2589:3698(1109) ack 323 win 17520 (DF) (46, id 21827) 00:05:18.834821 64.254.128.66465> 74125.228.54.1270: F 323367(44) 3698 win 8760 (DF) (t 64, id 21850) 00:05:18.979877 74.125.228.54.1270> 64.254.128.66465: F 3704:3704(0) ack 367 win 17520 (DF) (l46, id 21901) 00:05:18.979957 64.254.128.66.465> 74.125.228.54.1270.ack 3705 win 8754 (DF) (ttl 64, id 33571)







