The screenshots show some parts of the VirusTotal report about an Android app. Identify possible malicious/suspicious indicators among the provided information. Make a conclusion whether this application is malware.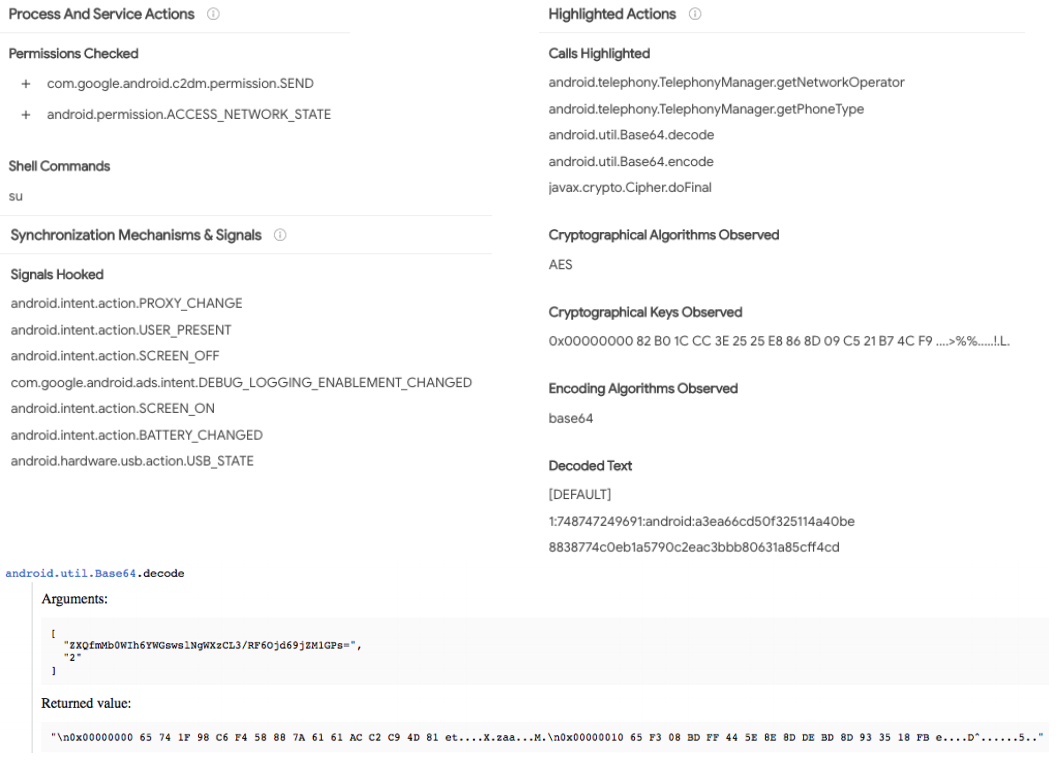
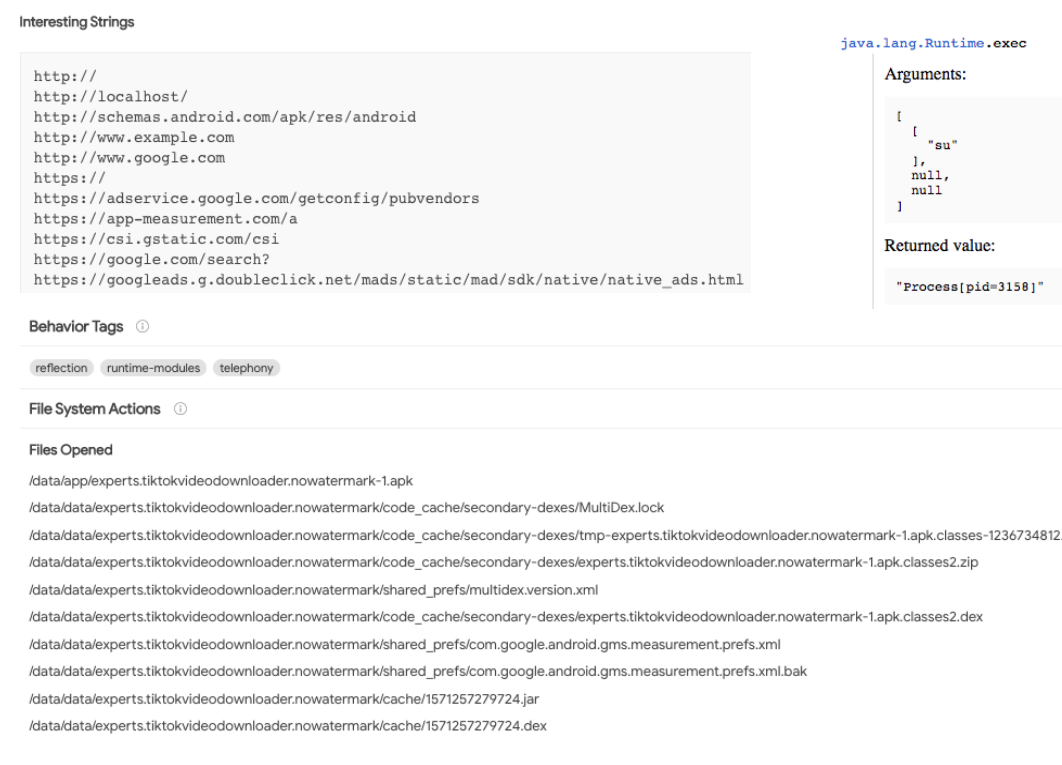
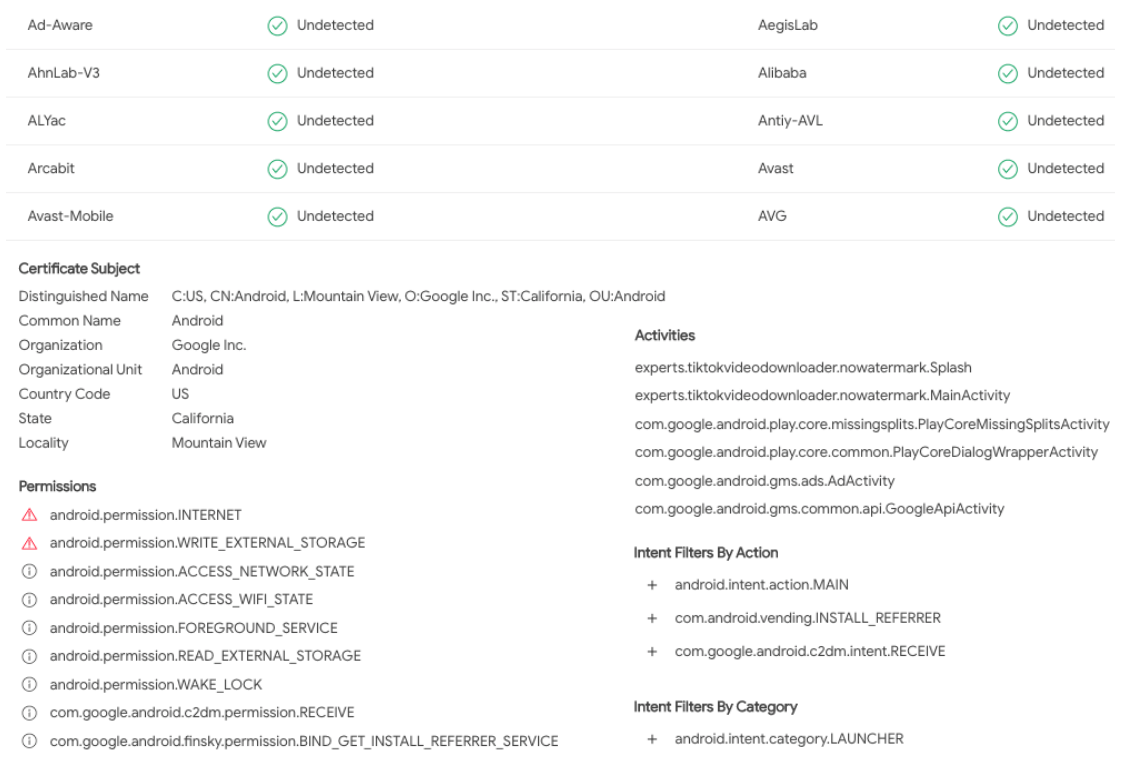
Process And Service Actions Highlighted Actions Permissions Checked + com.google.android.c2dm.permission.SEND + android.permission.ACCESS_NETWORK_STATE Calls Highlighted android telephony.Telephony Manager.getNetworkOperator android telephony.Telephony Manager.getPhone Type android.util.Base64.decode android.util.Base64.encode javax.crypto.Cipher.doFinal Shell Commands su Synchronization Mechanisms & Signals Cryptographical Algorithms Observed AES Signals Hooked Cryptographical Keys Observed Ox00000000 82 BO 1C CC 3E 25 25 E8 86 8D 09 C5 21 B7 4C F9.....>%%...I.L. android.intent.action.PROXY_CHANGE android.intent.action.USER PRESENT android.intent.action.SCREEN OFF com.google.android.ads.intent.DEBUG_LOGGING_ENABLEMENT_CHANGED android.intent.action SCREEN ON android.intent.action.BATTERY CHANGED android.hardware.usb.action.USB_STATE Encoding Algorithms Observed base64 Decoded Text (DEFAULT) 1:748747249691:android:a3ea66cd50f325114a40be 8838774c0eb1a5790c2eac3bbb80631a85cff4cd android.util.Base64.decode Arguments: [ "ZXQfmMBOWIH6YWGswsingWXzCL3/RF60jd69jzM1GPS=", "2 ] Returned value: " 0x00000000 65 74 IF 98 C6 F4 58 88 7A 61 61 AC C2 C9 4D 81 et....X.zaa...M. 0x00000010 65 73 08 BD FF 44 5E BE BD DE BD 8D 93 35 18 FB e....D......5.." Interesting Strings java.lang.Runtime.exec Arguments: [ http:// http://localhost/ http://schemas.android.com/apk/res/android http://www.example.com http://www.google.com https:// https://adservice.google.com/getconfig/pubvendors https://app-measurement.com/a https://csi.gstatic.com/csi https://google.com/search? https://googleads.g.doubleclick.net/mads/static/mad/sdkativeative_ads.html [ "su" 1. null, null Returned value: "Process[pid=3158]" Behavior Tags reflection runtime-modules telephony File System Actions Files Opened Idata/app/experts.tiktokvideodownloader.nowatermark-1.apk Idata/data/experts.tiktokvideodownloader.nowatermark/code_cache/secondary-dexes/MultiDex.lock /data/datalexperts.tiktokvideodownloader.nowatermark/code_cache/secondary-dexes/tmp-experts.tiktokvideodownloader.nowatermark-1.apk.classes-1236734812 /data/data/experts.tiktokvideodownloader.nowatermark/code_cache/secondary-dexes/experts.tiktokvideodownloader.nowatermark-1.apk.classes2.zip Idata/data/experts.tiktokvideodownloader.nowatermark/shared_prefs/multidex.version.xml Idata/data/experts.tiktokvideodownloader.nowatermark/code_cache/secondary-dexes/experts.tiktokvideodownloader.nowatermark-1.apk.classes2.dex /data/data/experts.tiktokvideo downloader.nowatermark/shared_prefs/com.google.android.gms.measurement.prefs.xml Idata/data/experts.tiktokvideodownloader.nowatermark/shared_prefs/com.google.android.gms.measurement.prefs.xml.bak /data/data/experts.tiktokvideodownloader.nowatermark/cache/1571257279724.jar Idata/data/experts.tiktokvideodownloader.nowatermark/cache/1571257279724.dex Ad-Aware Undetected AegisLab Undetected AhnLab-V3 Undetected Alibaba Undetected ALYac Undetected Antiy-AVL Undetected Arcabit Undetected Avast Undetected Avast-Mobile Undetected AVG Undetected Certificate Subject Distinguished Name C:US, CN:Android, L:Mountain View, O:Google Inc., ST:California, OU:Android Common Name Android Activities Organization Google Inc. Organizational Unit Android experts.tiktokvideodownloader.nowatermark. Splash Country Code US experts.tiktokvideodownloader.nowatermark. MainActivity State California com.google.android.play.core.missingsplits.PlayCoreMissingSplits Activity Locality Mountain View com.google.android.play.core.common.PlayCoreDialogWrapperActivity Permissions com.google.android.gms.ads.AdActivity Aandroid.permission.INTERNET com.google.android.gms.common.api.GoogleApiActivity Aandroid.permission.WRITE_EXTERNAL_STORAGE Intent Filters By Action android.permission.ACCESS_NETWORK_STATE android.intent.action.MAIN android.permission.ACCESS_WIFI_STATE com.android.vending.INSTALL_REFERRER android.permission.FOREGROUND_SERVICE android.permission.READ_EXTERNAL_STORAGE com.google.android.c2dm.intent.RECEIVE android.permission.WAKE_LOCK com.google.android.c2dm.permission.RECEIVE Intent Filters By Category com.google.android.finsky.permission.BIND_GET_INSTALL_REFERRER_SERVICE android.intent.category.LAUNCHER + + + + Process And Service Actions Highlighted Actions Permissions Checked + com.google.android.c2dm.permission.SEND + android.permission.ACCESS_NETWORK_STATE Calls Highlighted android telephony.Telephony Manager.getNetworkOperator android telephony.Telephony Manager.getPhone Type android.util.Base64.decode android.util.Base64.encode javax.crypto.Cipher.doFinal Shell Commands su Synchronization Mechanisms & Signals Cryptographical Algorithms Observed AES Signals Hooked Cryptographical Keys Observed Ox00000000 82 BO 1C CC 3E 25 25 E8 86 8D 09 C5 21 B7 4C F9.....>%%...I.L. android.intent.action.PROXY_CHANGE android.intent.action.USER PRESENT android.intent.action.SCREEN OFF com.google.android.ads.intent.DEBUG_LOGGING_ENABLEMENT_CHANGED android.intent.action SCREEN ON android.intent.action.BATTERY CHANGED android.hardware.usb.action.USB_STATE Encoding Algorithms Observed base64 Decoded Text (DEFAULT) 1:748747249691:android:a3ea66cd50f325114a40be 8838774c0eb1a5790c2eac3bbb80631a85cff4cd android.util.Base64.decode Arguments: [ "ZXQfmMBOWIH6YWGswsingWXzCL3/RF60jd69jzM1GPS=", "2 ] Returned value: " 0x00000000 65 74 IF 98 C6 F4 58 88 7A 61 61 AC C2 C9 4D 81 et....X.zaa...M. 0x00000010 65 73 08 BD FF 44 5E BE BD DE BD 8D 93 35 18 FB e....D......5.." Interesting Strings java.lang.Runtime.exec Arguments: [ http:// http://localhost/ http://schemas.android.com/apk/res/android http://www.example.com http://www.google.com https:// https://adservice.google.com/getconfig/pubvendors https://app-measurement.com/a https://csi.gstatic.com/csi https://google.com/search? https://googleads.g.doubleclick.net/mads/static/mad/sdkativeative_ads.html [ "su" 1. null, null Returned value: "Process[pid=3158]" Behavior Tags reflection runtime-modules telephony File System Actions Files Opened Idata/app/experts.tiktokvideodownloader.nowatermark-1.apk Idata/data/experts.tiktokvideodownloader.nowatermark/code_cache/secondary-dexes/MultiDex.lock /data/datalexperts.tiktokvideodownloader.nowatermark/code_cache/secondary-dexes/tmp-experts.tiktokvideodownloader.nowatermark-1.apk.classes-1236734812 /data/data/experts.tiktokvideodownloader.nowatermark/code_cache/secondary-dexes/experts.tiktokvideodownloader.nowatermark-1.apk.classes2.zip Idata/data/experts.tiktokvideodownloader.nowatermark/shared_prefs/multidex.version.xml Idata/data/experts.tiktokvideodownloader.nowatermark/code_cache/secondary-dexes/experts.tiktokvideodownloader.nowatermark-1.apk.classes2.dex /data/data/experts.tiktokvideo downloader.nowatermark/shared_prefs/com.google.android.gms.measurement.prefs.xml Idata/data/experts.tiktokvideodownloader.nowatermark/shared_prefs/com.google.android.gms.measurement.prefs.xml.bak /data/data/experts.tiktokvideodownloader.nowatermark/cache/1571257279724.jar Idata/data/experts.tiktokvideodownloader.nowatermark/cache/1571257279724.dex Ad-Aware Undetected AegisLab Undetected AhnLab-V3 Undetected Alibaba Undetected ALYac Undetected Antiy-AVL Undetected Arcabit Undetected Avast Undetected Avast-Mobile Undetected AVG Undetected Certificate Subject Distinguished Name C:US, CN:Android, L:Mountain View, O:Google Inc., ST:California, OU:Android Common Name Android Activities Organization Google Inc. Organizational Unit Android experts.tiktokvideodownloader.nowatermark. Splash Country Code US experts.tiktokvideodownloader.nowatermark. MainActivity State California com.google.android.play.core.missingsplits.PlayCoreMissingSplits Activity Locality Mountain View com.google.android.play.core.common.PlayCoreDialogWrapperActivity Permissions com.google.android.gms.ads.AdActivity Aandroid.permission.INTERNET com.google.android.gms.common.api.GoogleApiActivity Aandroid.permission.WRITE_EXTERNAL_STORAGE Intent Filters By Action android.permission.ACCESS_NETWORK_STATE android.intent.action.MAIN android.permission.ACCESS_WIFI_STATE com.android.vending.INSTALL_REFERRER android.permission.FOREGROUND_SERVICE android.permission.READ_EXTERNAL_STORAGE com.google.android.c2dm.intent.RECEIVE android.permission.WAKE_LOCK com.google.android.c2dm.permission.RECEIVE Intent Filters By Category com.google.android.finsky.permission.BIND_GET_INSTALL_REFERRER_SERVICE android.intent.category.LAUNCHER + + + +









