Use Python programing for the following problem.

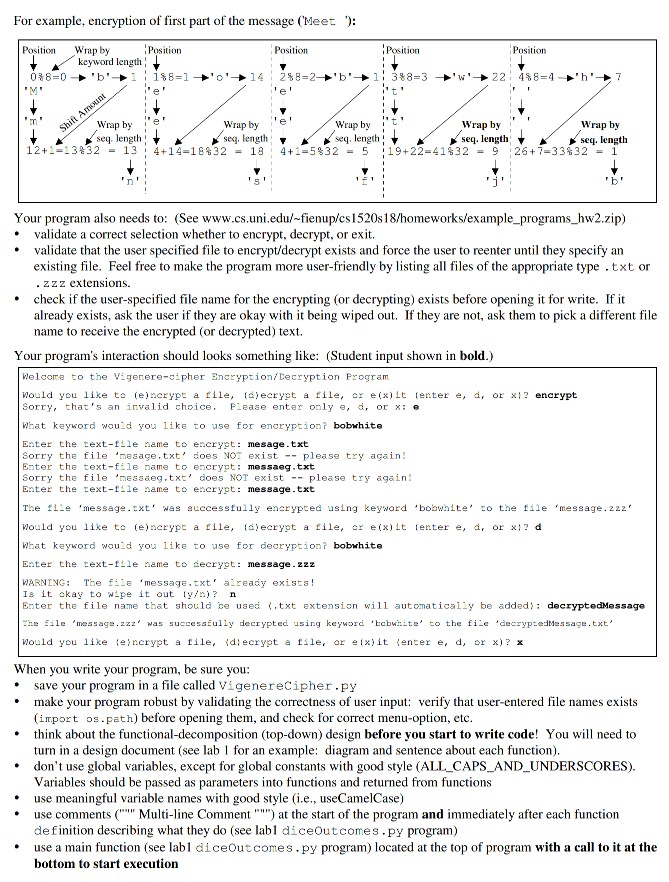
File Encryption/Decryption Program: You are to design and write a program that allows a user to interactively select between encrypting or decrypting files * encrypting a user-specified text-file (.txt extension) using a Vigenere-cipher encryption scheme to generate a new encoded file with the same name, except with a .zzz extension. The Vigenere-cipher is a form of substitution cipher based on a user-specified keyword. see below example) * decrypting a user-specified Vigenere-cipher file (.zzz extension) using a user-specified keyword to generate a new text-file with the same name, except with a .txt extension Vigenere-cipher encryption example: For the keyword "hobwhite" and the subset of 32 characters shown in the top row helow (i.e., letters,space, nnew-line, , /comma, /period,/question-mark, and !Hexclamation-point), the Vigenere-cipher table would be Additional Positions row#| 0 | 1 | 2 | 3 | 4 | 5 | 6 | 7 | 8 | 9 | 10|11112131415|16|17|18| 19202122232425 2627282930|31 ?!a 816 24 0 a 1018I 26 7. r s 1422 30 To encrypt a message with the keyword "bobwhite", the first character of message (at position 0) uses row 0 ('a' maps to a ;h', 'h' maps to ac", etc.). The second character of the message (at position l ) uses row I ("a' maps to a , b' maps to a 'p', etc). Tf the message is longer than the keyword, then every 8th character (i.e., the length of "bobwhite") uses the same row (e.g., characters of the message at positions 1,9, 17, 25, 33, etc. al use row 1). All upper-case letters can he converted to lower-case before encryption. Any characters not in the top row can be completely ignored (i.e., discarded) without incrementing the position in the message The text-file message.txt (with new-line characters shown as in') would he encrypted to message. zzz and then decrypted back to decryptedMessage.txt as shown below: message.txt message zz2 decryptedMessage.txt Meet by the Union at noon today!hn -Sam rn eet by the union at noon today!r samn lints: . You don't actually need to create the Vigenere-cipher table shown above. Instead just use the position of each character from the overall sequence, and the position of each keyword character in the overall sequence Letter minO Position 012 3456 7 Letter b o b wh ite Letter seq You might also want to create a dictionary to enable quick lookup of characters position in the sequence (e.g. "m" 12, '?' . 30, etc.)








