Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Using the following table, calculate the ARO ( Pre ) , ALE ( Pre ) , ARO ( Post ) , ALE ( Post )
Using the following table, calculate the ARO Pre ALEPre AROPost ALEPost and CBA for each threat category listed with explanation how calculation was done.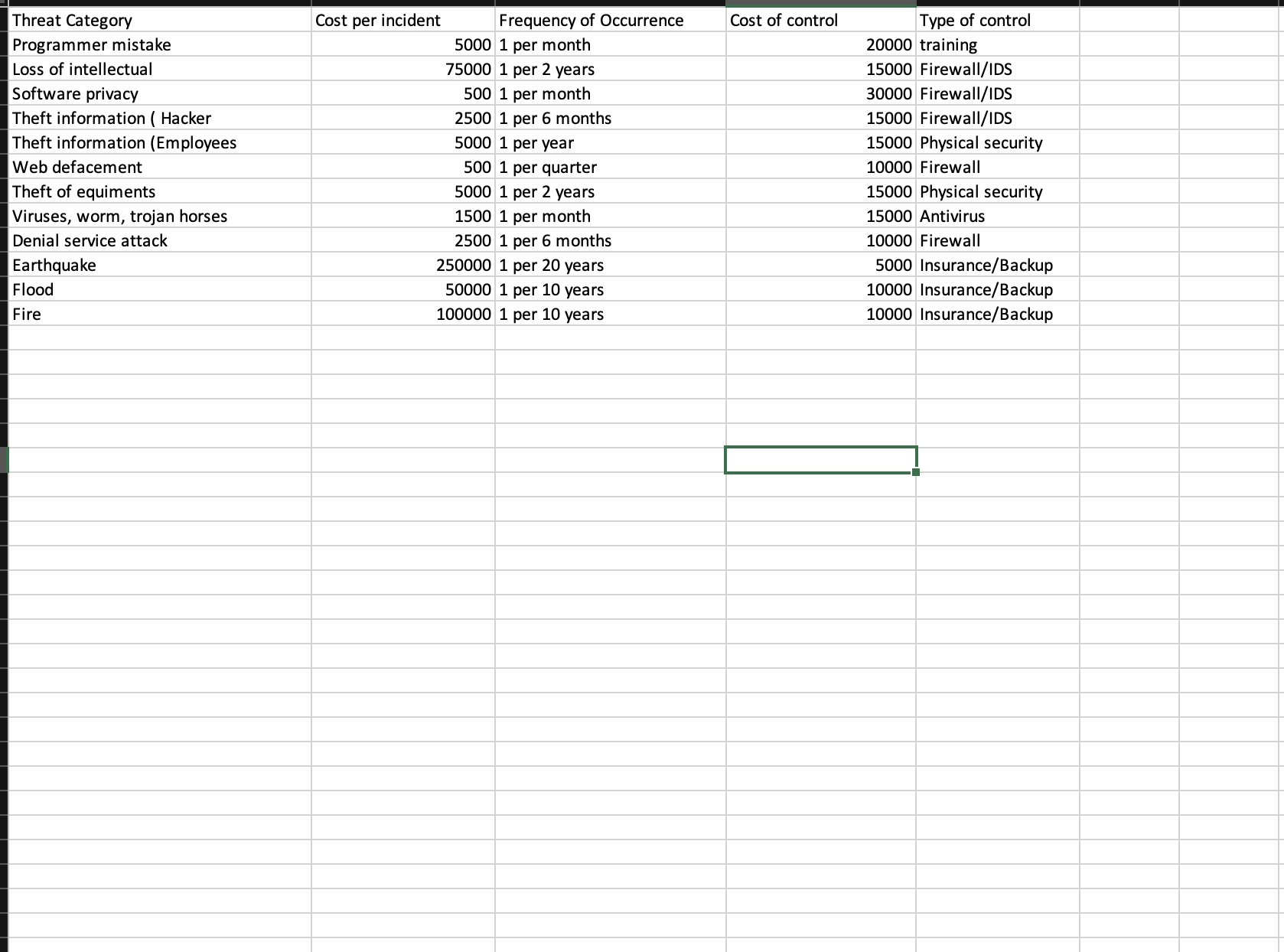
Threat Category Programmer mistake Loss of intellectual Software privacy Theft information (Hacker Cost per incident Frequency of Occurrence Cost of control 5000 1 per month Type of control 20000 training Theft information (Employees Web defacement Theft of equiments Viruses, worm, trojan horses Denial service attack Earthquake 250000 1 per 20 years 75000 1 per 2 years 500 1 per month 2500 1 per 6 months 5000 1 per year 500 1 per quarter 5000 1 per 2 years 1500 1 per month 2500 1 per 6 months 15000 Firewall/IDS 30000 Firewall/IDS 15000 Firewall/IDS 15000 Physical security 10000 Firewall 15000 Physical security 15000 Antivirus 10000 Firewall 5000 Insurance/Backup Flood Fire 50000 1 per 10 years 10000 Insurance/Backup 100000 1 per 10 years 10000 Insurance/Backup
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


