Answered step by step
Verified Expert Solution
Question
1 Approved Answer
write a C++ program 2. Data Security Encryption is an effective way to achieve data security. To read an encrypted file, you must have access
write a C++ program 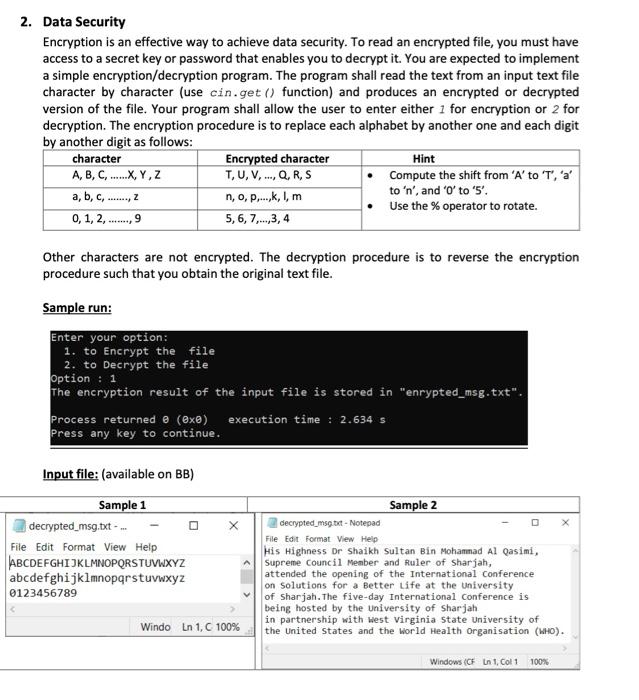
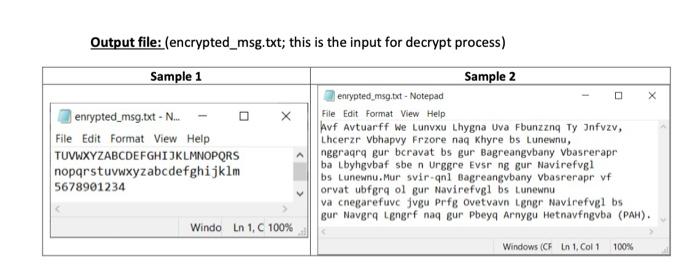
2. Data Security Encryption is an effective way to achieve data security. To read an encrypted file, you must have access to a secret key or password that enables you to decrypt it. You are expected to implement a simple encryption/decryption program. The program shall read the text from an input text file character by character (use cin.get() function) and produces an encrypted or decrypted version of the file. Your program shall allow the user to enter either 1 for encryption or 2 for decryption. The encryption procedure is to replace each alphabet by another one and each digit by another digit as follows: character Encrypted character Hint A, B, C, ......X,Y,Z T,U,V, ..., Q, R, S Compute the shift from 'A' to 'T', 'a' no, ....,k,1,m to 'n', and 'o' to 'S'. Use the % operator to rotate. 0, 1, 2, 5,6,7,...,3,4 a, b, c, Z 9 Other characters are not encrypted. The decryption procedure is to reverse the encryption procedure such that you obtain the original text file. Sample run: Enter your option: 1. to Encrypt the file 2. to Decrypt the file Option : 1 The encryption result of the input file is stored in "enrypted_msg.txt". Process returned @ (exe) execution time : 2.634 s Press any key to continue. Input file: (available on BB) Sample 1 decrypted_msg.txt- File Edit Format View Help ABCDEFGHIJKLMNOPQRSTUVWXYZ abcdefghijklmnopqrstuvwxyz 0123456789 Sample 2 decrypted_msgst - Notepad D X File Edit Format View Help His Highness Dr Shaikh Sultan Bin Mohammad Al Qasimi, Supreme Council Member and Ruler of Sharjah, attended the opening of the International Conference on Solutions for a Better life at the University of Sharjah. The five-day International Conference is being hosted by the University of Sharjah in partnership with west Virginia State University of the United States and the World Health Organisation (WHO). Windo in 1, C 100% Windows (CF in 1, Col1 100% Output file: (encrypted_msg.txt; this is the input for decrypt process) Sample 1 Sample 2 enrypted_msg.txt - Notepad enrypted_msg.txt - N. File Edit Format View Help Avf Avtuarff We Lunvxu Lhygna Uva Fbunzzng Ty Infuzv, File Edit Format View Help Lhcerzr Vbhapvy Frzore naq Khyre bs Lunewnu, TUVWXYZABCDEFGHIJKLMNOPQRS nggraqrq gur bcravat bs gur Bagreangybany Vbasrerar ba Lbyhgvbaf sbe n Urggre Evsr ng gur Navirefugi nopqrstuvwxyzabcdefghijklm bs Lunewnu. Mur svir.nl Bagreang bany Vbasrerar vf 5678901234 orvat ubfgrq ol gur Navirefugl bs Lunewnu va chegarefuvc jvgu Prfg ovet vavn tgner Navirefugl bs Arnygu (PAH). Windo Ln 1, C 100% Windows (CF in 1 Col 1 100% 

Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


