There are five types of fraud schemes in systems development cycles (refer to Figure 12.6)? Identify an
Question:
FIGURE 12.6:
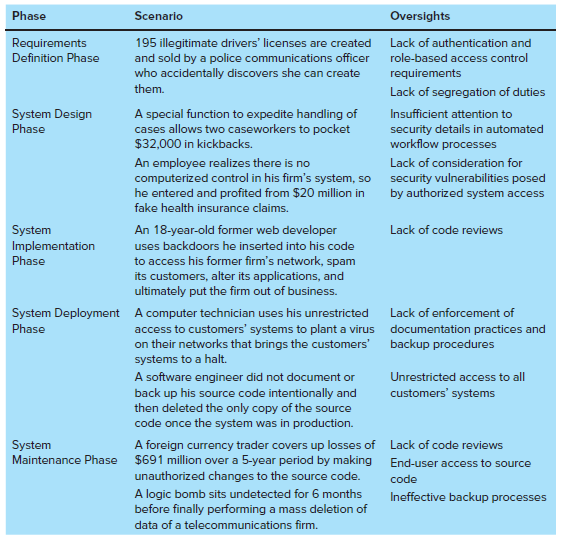
Transcribed Image Text:
Phase Scenario Oversights Requirements Definition Phase 195 illegitimate drivers' licenses are created and sold by a police communications officer who accidentally discovers she can create them. Lack of authentication and role-based access control requirements Lack of segregation of duties System Design A special function to expedite handling of cases allows two caseworkers to pocket $32,000 in kickbacks. Insufficient attention to security details in automated workflow processes Phase An employee realizes there is no computerized control in his firm's system, so he entered and profited from $20 million in Lack of consideration for security vulnerabilities posed by authorized system access fake health insurance claims. An 18-year-old former web developer System Implementation Lack of code reviews uses backdoors he inserted into his code to access his former firm's network, spam its customers, alter its applications, and ultimately put the firm out of business. Phase System Deployment A computer technician uses his unrestricted access to customers' systems to plant a virus on their networks that brings the customers' systems to a halt. Lack of enforcement of Phase documentation practices and backup procedures A software engineer did not document or back up his source code intentionally and then deleted the only copy of the source code once the system was in production. Unrestricted access to all customers' systems System Maintenance Phase A foreign currency trader covers up losses of $691 million over a 5-year period by making Lack of code reviews End-user access to source unauthorized changes to the source code. code A logic bomb sits undetected for 6 months before finally performing a mass deletion of Ineffective backup processes data of a telecommunications firm.
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 60% (15 reviews)
a Lack of authentication andor role based acc...View the full answer

Answered By

Aun Ali
I am an Associate Member of Cost and Management Accountants of Pakistan with vast experience in the field of accounting and finance, including more than 17 years of teaching experience at university level. I have been teaching at both undergraduate and post graduate levels. My area of specialization is cost and management accounting but I have taught various subjects related to accounting and finance.
5.00+
13+ Reviews
32+ Question Solved
Related Book For 

Accounting Information Systems
ISBN: 978-1260153156
2nd edition
Authors: Vernon Richardson, Chengyee Chang, Rod Smith
Question Posted:
Students also viewed these Business questions
-
There are five types of management earnings techniques presented in this chapter. Provide two or three specific examples of how corporate leaders could pull off these types of fraud, as well as the...
-
There are five types of boxes whose sizes and demands are given in the table below. The unit cost of a box is equal to its size, and there is an initial cost of $100 to produce each type of box....
-
What are the five types of analytical procedures? Briefly discuss each. There are five types of analytical procedures: (1) Those ratios that compare client and industry data; (2) Ratios that compare...
-
Data visualization can help Broadway theatre analysts to understand ticket pricesExample: Recall the Service Company Insight box How Much Did You Pay for That Seat? presented in the chapter. As...
-
Find g'(x) if g(x) = 1/ x3 - 4x.
-
A three-element series circuit contains R = 5, L = 4 H, and C = 3.91 mF. Obtain the series resonant frequency, in rad/s, and then frequency-scale the circuit with K f = 1000. Plot |Z(w)| for both...
-
Consider an experiment designed to estimate the linear relationship between the percentage of a certain drug in the bloodstream of a subject and the length of time it takes the subject to react to a...
-
1. Using your best cultural intelligence, how would you adjust your behavior on a business trip to China? 2. What cultural adjustments will Chinese managers need to make if they want to effectively...
-
Earnings Per Share Financial statement data for years ending December 31 for Jardine Company are shown below. 2016 2015 Net income $623,500 $499,250 Preferred dividends $95,000 $95,000 Average number...
-
Pam, Sergei, and Mercedes are all one-third partners in the capital and profits of Oak Grove General Partnership. Partnership debt is allocated among the partners in accordance with their capital and...
-
Internal auditors are often tasked with testing vulnerabilities. How would you suggest testing for system intrusion, logical access control, natural disasters, and intentional destruction of...
-
Identify the main components of vulnerability management and assessment? Component a. Prioritize vulnerabilities b. Design a risk response plan c. Monitor vulnerabilities d. Establish policy and...
-
RP owned residential real estate with a $680,000 adjusted basis that was condemned by City Q because it needed the land for a new convention center. RP received $975,000 condemnation proceeds for the...
-
1. Make a comparison between the leadership approaches "Trait Models" and "Behavioral Models". Discuss the main postulates and differences between the models and provide examples of a theory...
-
Applying the Central Limit Theorem: The amount of contaminants that are allowed in food products is determined by the FDA ( Food and Drug Administration ) . Common contaminants in cow milk include...
-
A collection of techniques used by social scientists to compile, summarize, and convey numerical data. Revised Research Question Hypothesis : Null Hypothesis : A null hypothesis, often known as H0,...
-
Adidas is an international sporting apparel/shoes brand. If Adidas was to enter a new foreign market, it would conduct a country market assessment. Identify the 4 components of the assessment....
-
Using the scenario linked in the Supporting Materials section, assume that you are the cost accountant for your company, and the CFO has asked for your analysis on purchasing materials from an online...
-
Use the Comparison Test or Limit Comparison Test to determine whether the following series converge. Data from in Comparison Test & Limit Comparison k + 1 k=1 k + 2 00
-
You are planning to purchase your first home five years from today. The required down payment will be $50,000. You currently have $20,000. but you plan to contribute $500 each quarter to a special...
-
Why are program change procedures important to auditors?
-
What is the importance of the SPL?
-
What functions does the SPLMS control?
-
Billy Bob bank has three assets. It has $83 million invested in consumer loans with a 3-year duration, $46 million invested in T-Bonds with a 12-year duration, and $69 million in 6-month (0.5 years)...
-
Ventaz Corp manufactures small windows for back yard sheds. Historically, its demand has ranged from 30 to 50 windows per day with an average of 4646. Alex is one of the production workers and he...
-
Which of the following statements is not true regarding the $500 credit for dependent other than a qualifying child credit. Cannot be claimed on the same tax return if the child tax credit is also...

Study smarter with the SolutionInn App


