Question: A program is running on a computer with a four-entry fully associative (micro) translation lookaside buffer (TLB): The following is a trace of virtual page
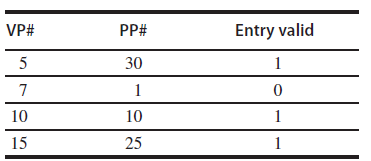
A program is running on a computer with a four-entry fully associative (micro) translation lookaside buffer (TLB):
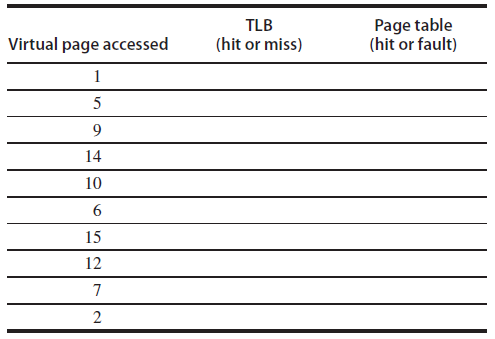
The following is a trace of virtual page numbers accessed by a program. For each access indicate whether it produces a TLB hit/miss and, if it accesses the page table, whether it produces a page hit or fault. Put an X under the page table column if it is not accessed.
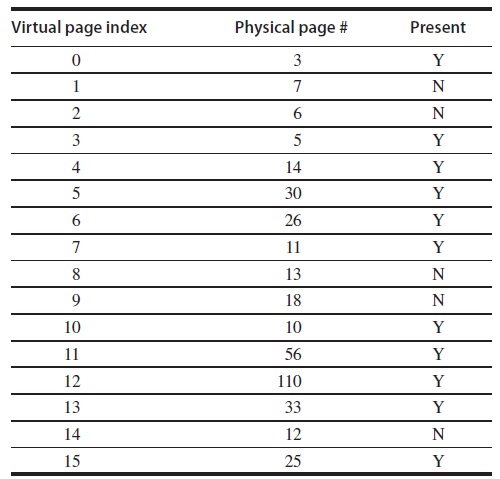
VP# PP# Entry valid 5 30 10 10 15 25 Virtual page index Physical page # Present 3 3 5 4 14 5 30 26 11 13 18 10 10 11 56 12 110 13 33 14 12 15 25 2. 1,
Step by Step Solution
3.43 Rating (182 Votes )
There are 3 Steps involved in it
VP 5 7 10 15 PP 30 1 10 25 Entry Valid 1 0 1 1 Virtual Page Index 0 1 2 3 4 5 ... View full answer

Get step-by-step solutions from verified subject matter experts


