Question: Show how the basic snooping protocol of Figure 5.6 can be changed for a write-through cache. What is the major hardware functionality that is not
Show how the basic snooping protocol of Figure 5.6 can be changed for a write-through cache. What is the major hardware functionality that is not needed with a write-through cache compared with a write-back cache?
Figure 5.6
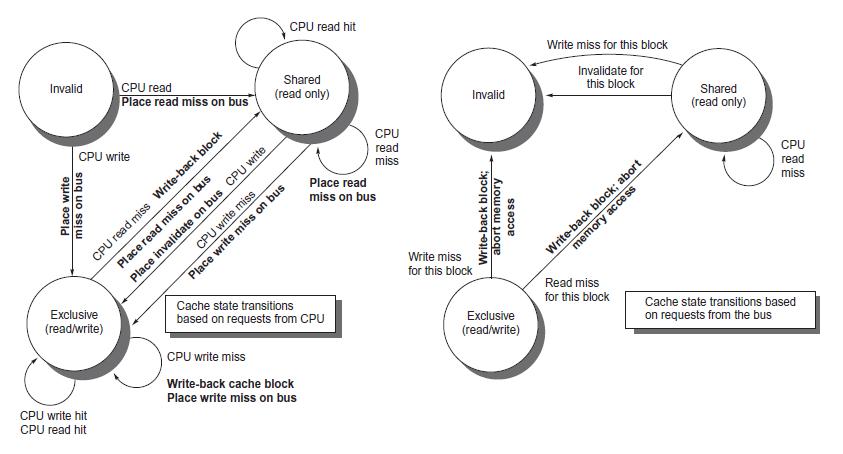
Invalid CPU write Place write miss on bus CPU read Place read miss on bus Exclusive (read/write) CPU read miss Write-back block Place read miss on bus CPU write hit CPU read hit Place invalidate on bus CPU write CPU read hit Shared (read only) CPU write miss Place write miss on bus Cache state transitions based on requests from CPU CPU write miss Write-back cache block Place write miss on bus CPU read miss Place read miss on bus Invalid Write miss for this block Write-back block; abort memory access Exclusive (read/write) Write miss for this block Invalidate for this block memory access Write-back block; abort Read miss for this block Shared (read only) CPU read miss Cache state transitions based on requests from the bus
Step by Step Solution
There are 3 Steps involved in it
The figure youve provided appears to show the state transitions for cache lines within a cache coherence protocol for a system with multiple processors or cache controllers Cache coherence protocols like MESI Modified Exclusive Shared Invalid help maintain consistency among multiple caches so that processors dont operate on stale data When discussing writethrough and writeback caches in the context of such a protocol 1 WriteThrough Cache A writethrough cache writes data to both the cache and the backing store usually main memory simultaneously Due to this behavior other caches will see the updated value as soon as it hits the memory bus because the write operations are immediately propagated to memory which can be snooped by other cache controllers The protocol for a writethrough cache primarily eliminates the Modified state since data is always consistent with main memory When a cache line is updated written to it is directly written to memory and hence there is no need to writeback the data upon eviction or when another cache requests the data 2 WriteBack Cache A writeback cache only writes data back to the memory when it is replaced evicted or during a writemiss where another processor ... View full answer

Get step-by-step solutions from verified subject matter experts


