Question: The transmission schedule (Table 6.3) for a given flow lists for each second the number of packets sent between that time and the following second.
The transmission schedule (Table 6.3) for a given flow lists for each second the number of packets sent between that time and the following second. The flow must stay within the bounds of a token bucket filter. What bucket depth does the flow need for the following token rates? Assume the bucket is initially full.
(a) Two packets per second.
(b) Four packets per second.
Table 6.3)
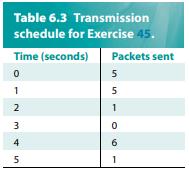
Table 6.3 Transmission schedule for Exercise 45. Time (seconds) Packets sent 0 1 U AWN 2 3 4 5 5 5 1 0 6 1
Step by Step Solution
3.52 Rating (155 Votes )
There are 3 Steps involved in it
To determine the required bucket depth for the flow to stay within the bounds of a token bucket filter we need to understand how the token bucket mech... View full answer

Get step-by-step solutions from verified subject matter experts


