Consider the following fragment: What type of malicious software is this? legitimate code if data is Friday
Question:
Consider the following fragment: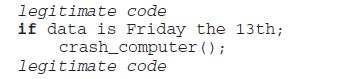
What type of malicious software is this?
Transcribed Image Text:
legitimate code if data is Friday the 13th; (); crash_computer legitimate code
Fantastic news! We've Found the answer you've been seeking!
Step by Step Answer:
Answer rating: 100% (2 reviews)

Answered By

Bhartendu Goyal
Professional, Experienced, and Expert tutor who will provide speedy and to-the-point solutions. I have been teaching students for 5 years now in different subjects and it's truly been one of the most rewarding experiences of my life. I have also done one-to-one tutoring with 100+ students and help them achieve great subject knowledge. I have expertise in computer subjects like C++, C, Java, and Python programming and other computer Science related fields. Many of my student's parents message me that your lessons improved their children's grades and this is the best only thing you want as a tea...
3.00+
2+ Reviews
10+ Question Solved
Related Book For 

Question Posted:
Students also viewed these Computer science questions
-
8. Which term describes an action that can damage or compromisean asset? A. Risk B. Vulnerability C. Countermeasure D. Threat 10. Which type of attack involves the creation of some deceptionin order...
-
Consider the following fragment in an authentication program What type of malicious software is this? username password = read_username (); read_password(); if username is "133t h4ckor" return...
-
Ordinary Simple Annuities & Ordinary General Annuities 16. A loan of $40000.00 is to be repaid by equal quarterly payments for 5 years. What is the size of each quarterly payment if the interest is...
-
Q3: Prove: For any sets A and B, Ax B = B A ?
-
The refrigerant fluid R-21 (see Table A.2) is to be used as the working fluid in a solar energy powered Rankine-cycle type power plant. Saturated liquid R-21 enters the pump, state 1, at 25oC, and...
-
What is perception? Explain the three parts of the perception process: exposure, attention, and interpretation. For marketers, what are the implications of each of these components?
-
. Why does the classic waterfall project planning model fail in this situation? What is it about the IT departments processes that leads to their finished systems being rejected constantly? This isnt...
-
1. What were Price Waterhouses fatal flaws? 2. Does Hopkinss treatment here make good business sense? Explain. 3. How would you avoid the problems in this case? In a jointly prepared statement...
-
Assignment 2 During 2020, ABC company had total Sales $10,675,500 including $3,000,000 cash sales. The AFDA had an unadjusted beginning debit balance on Dec31, 2020 of $31,500. Accounts Receivable...
-
The following code fragments show a sequence of virus instructions and a metamorphic version of the virus. Describe the effect produced by the metamorphic code. Original Code mov eax, 5 add eax, ebx...
-
There is a flaw in the virus program of Figure 21.1.What is it? program V := {goto main; 1234567; subroutine infect-executable := {loop: file := get-random-executable-file; } if (first-line-of-file =...
-
A sample of 20 insurance claims for automobile accidents (in \($1000\)) gives the following values: Construct a 0.95 confidence interval on the mean value of claims. Comment on the usefulness of this...
-
The issue of Royal Rose Manufacturing Co., Ltd. with many new employees is the low level of production. Although the company implements training programs for employees, the skill improvement of...
-
For safety reasons an elevator stops with an acceleration of g/3 in the case of an emergency. Let's assume an unusually high ceiling of the elevator to hang three sections lamp one below the other...
-
Can Google be characterized as a monopoly? Justify your answer by specifying and comparing the characteristics of a monopoly with those of Google. What is competition law? How would you justify the...
-
In the case below design and draw a Rich Picture that identifies the key stakeholders, actors, power and decision-making authorities. The novel coronavirus has turned the world upside down as a...
-
1. Two spherical stars A and B have densities PA and PB, respectively. A and B have the same radius, and their masses MA and M are related by MB = 2M. Due to an interaction process, star A loses some...
-
There are 25 cells with no molecules, 21 with one molecule, 19 with two molecules, and 15 with three molecules. Suppose that the number N of molecules of toxin left in a cell after 10.0 min is...
-
As of January 1, 2018, Room Designs, Inc. had a balance of $9,900 in Cash, $3,500 in Common Stock, and $6,400 in Retained Earnings. These were the only accounts with balances in the ledger on January...
-
On a typical Intel 8086-based system, connected via system bus to DRAM memory, for a read operation, is activated by the trailing edge of the Address Enable signal (Figure 3.19). However, due to...
-
The memory of a particular microcomputer is built from 64K 1 DRAMs. According to the data sheet, the cell array of the DRAM is organized into 256 rows. Each row must be refreshed at least once every...
-
Figure 5.17 shows one of the early SRAMs, the 16 Ã 4 Signetics 7489 chip, which stores 16 4-bit words. a. List the mode of operation of the chip for each input pulse shown in Figure 5.17c. b....
-
Slow Roll Drum Co. is evaluating the extension of credit to a new group of customers. Although these customers will provide $198,000 in additional credit sales, 13 percent are likely to be...
-
Wendell's Donut Shoppe is investigating the purchase of a new $39,600 conut-making machine. The new machine would permit the company to reduce the amount of part-time help needed, at a cost savings...
-
1.Discuss the challenges faced with Valuing Stocks and Bonds. As part of this discussion, how will the selected item be implemented in an organization and its significance? 2. Discuss how Valuing...
Michele Scism On The Rules Of Effective Content Marketing 1st Edition - ISBN: 1616992778 - Free Book

Study smarter with the SolutionInn App


