Question: Justify Table 8.2, summarizing the running time of the methods of a tree represented with a linked structure, by providing, for each method, a description
Justify Table 8.2, summarizing the running time of the methods of a tree represented with a linked structure, by providing, for each method, a description of its implementation, and an analysis of its running time.
Table 8.2
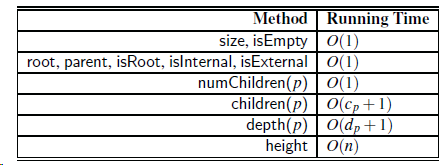
Method Running Time size, isEmpty| 0(1) root, parent, isRoot, islnternal, isExternal 0(1) numChildren(p) 0(1) children(p) | 0(cp+1) height | 0(n)
Step by Step Solution
3.36 Rating (159 Votes )
There are 3 Steps involved in it
The size and isEmpty methods run in O1 assuming we ma... View full answer

Get step-by-step solutions from verified subject matter experts


