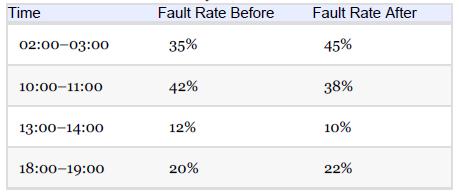
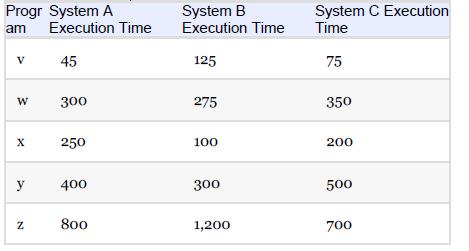
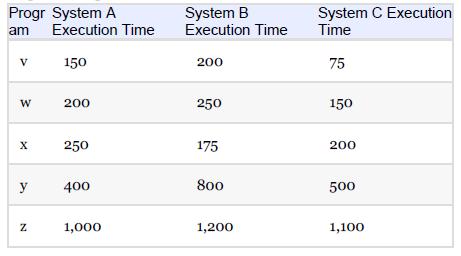
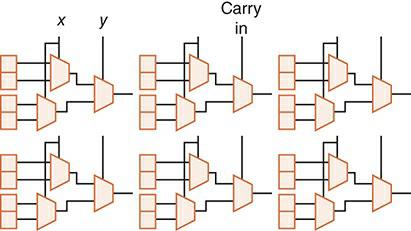
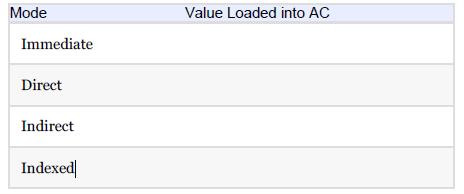
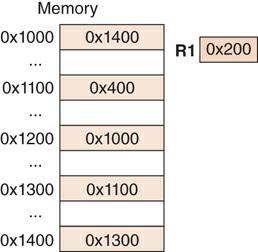
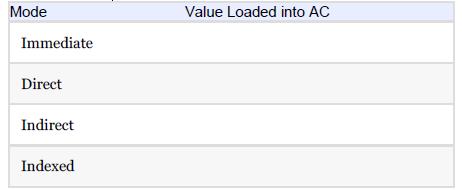
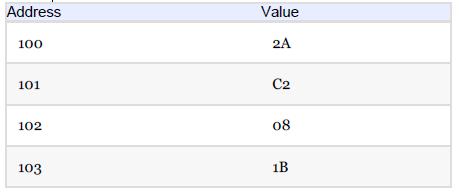
Essentials Of Computer Organization And Architecture 5th Edition Linda Null, Julia Lobur - Solutions
Unlock the full potential of your studies with our comprehensive resources for "Essentials of Computer Organization and Architecture 5th Edition" by Linda Null and Julia Lobur. Access the online answers key, solution manual, and solutions PDF to tackle solved problems with confidence. Explore detailed questions and answers, test bank insights, and chapter solutions for a seamless learning experience. Our step-by-step answers and instructor manual serve as an invaluable guide to mastering this textbook. Enjoy a hassle-free study session with these resources available for free download, ensuring success in your academic journey.
![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()