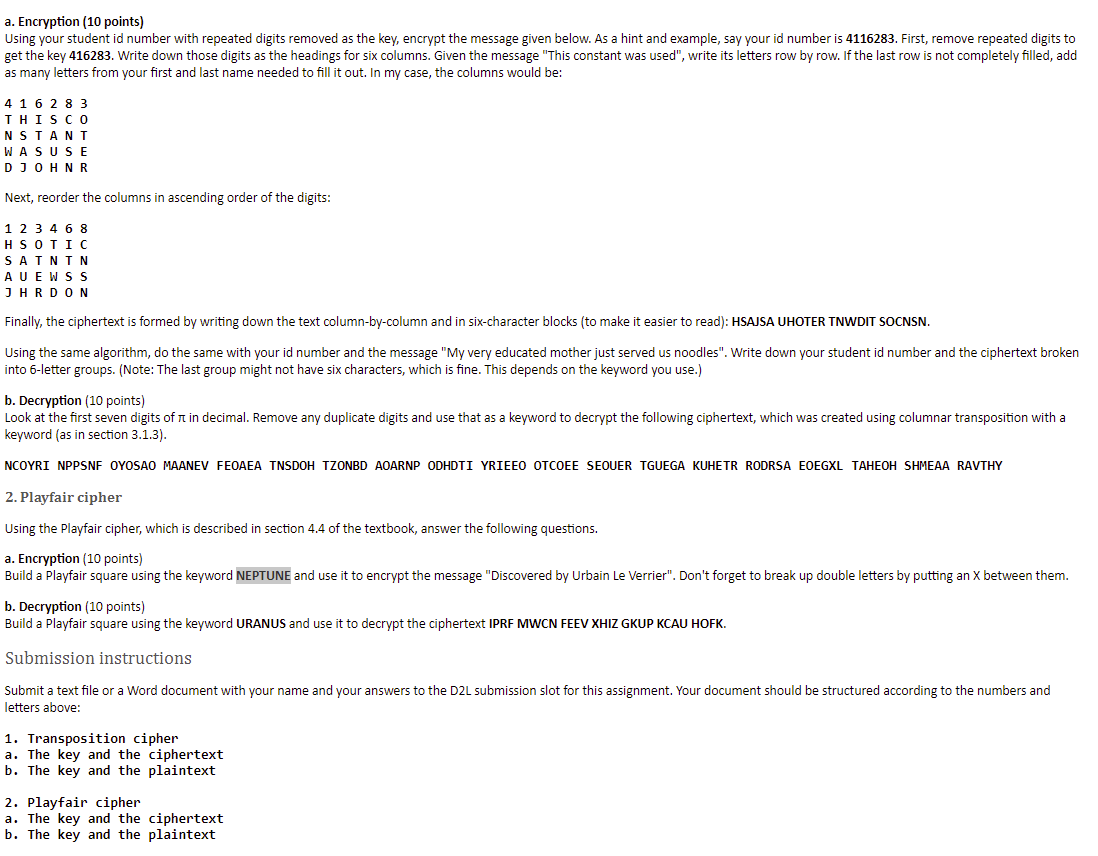
a. Encryption (10 points) Using your student id number with repeated digits removed as the key, encrypt the message given below. As a hint and example, say your id number is 4116283. First, remove repeated digits to get the key 416283. Write down those digits as the headings for six columns. Given the message "This constant was used", write its letters row by row. If the last row is not completely filled, add as many letters from your first and last name needed to fill it out. In my case, the columns would be: 4 1 6 2 83 THISCO NSTANT WASU SE DJOHNR Next, reorder the columns in ascending order of the digits: 1 2 3 4 6 8 HSOTIC SAININ AU EWSS JHRDON Finally, the ciphertext is formed by writing down the text column-by-column and in six-character blocks (to make it easier to read): HSAJSA UHOTER TNWDIT SOCNSN. Using the same algorithm, do the same with your id number and the message "My very educated mother just served us noodles". Write down your student id number and the ciphertext broken into 6-letter groups. (Note: The last group might not have six characters, which is fine. This depends on the keyword you use.) b. Decryption (10 points) Look at the first seven digits of it in decimal. Remove any duplicate digits and use that as a keyword to decrypt the following ciphertext, which was created using columnar transposition with a keyword (as in section 3.1.3). NCOYRI NPPSNF OYOSAO MAANEV FEOAEA TNSDOH TZONBD AOARNP ODHDTI YRIEEO OTCOEE SEOUER TGUEGA KUHETR RODRSA EOEGXL TAHEOH SHMEAA RAVTHY 2. Playfair cipher Using the Playfair cipher, which is described in section 4.4 of the textbook, answer the following questions. a. Encryption (10 points) Build a Playfair square using the keyword NEPTUNE and use it to encrypt the message "Discovered by Urbain Le Verrier". Don't forget to break up double letters by putting an X between them. b. Decryption (10 points) Build a Playfair square using the keyword URANUS and use it to decrypt the ciphertext IPRF MWCN FEEV XHIZ GKUP KCAU HOFK. Submission instructions Submit a text file or a Word document with your name and your answers to the D2L submission slot for this assignment. Your document should be structured according to the numbers and letters above: 1. Transposition cipher a. The key and the ciphertext b. The key and the plaintext 2. Playfair cipher a. The key and the ciphertext b. The key and the plaintext







