Question
Bootkit Short bio - A bootkit is a type of malicious infection which targets the Master Boot Record located on the physical motherboard of the
Bootkit
Short bio - A bootkit is a type of malicious infection which targets the Master Boot Record located on the physical motherboard of the computer. Attaching malicious software in this manner can allow for a malicious program to be executed prior to the loading of the operating system.
The primary benefit to a bootkit infection is that it cannot be detected by standard operating systems processes because all of the components reside outside of the Windows file system.
Bootkit infections are on the decline with the increased adoption of modern operating systems and hardware utilizing UFEI and Secure Boot technologies.
Symptoms
Well-crafted bootkit infections may provide little indication of compromise as pertinent files may be hidden from the operating system and security defenses present on the computer. More often, bootkit infections may cause system instability and result in Blue Screen warnings or an inability to launch the operating system. Some bootkit infections may display a warning and demand payment via digital currency to restore the computer to an operational capacity. Malwarebytes recommends to never pay these types of ransom.
Type and source of infection
Bootkits were historically spread via bootable floppy disks and other bootable media. Recent bootkits may be installed using various methods, including being disguised as harmless software program and distributed alongside free downloads, or targeted to individuals as an email attachment. Alternatively, bootkits could be installed via a malicious website utilizing vulnerabilities within the browser. Infections that happen in this manner are usually silent and happen without any user knowledge or consent.
Protection
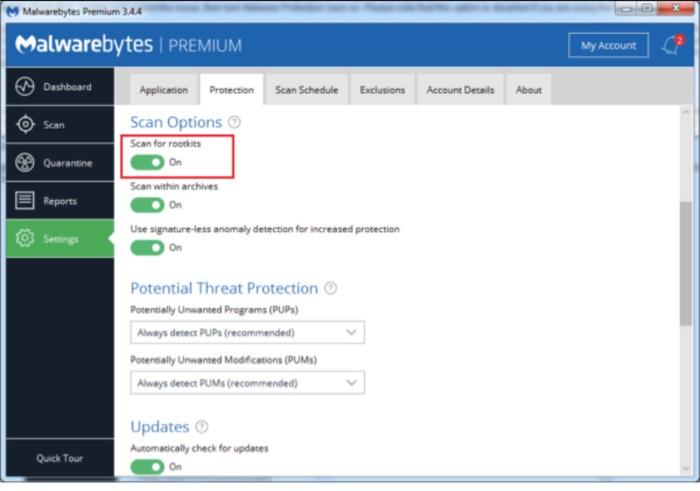
Malwarebytes can scan and detect for the presence of some bootkit infections. These detections utilize a specific set of rules and tests to determine if a bootkit infection is present on the computer. This testing method is more intensive and more effective, but including rootkit scans as part of your overall scan strategy increases the time required to perform a scan.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


