Company A is a global company based in the United States that operates in the financial industry. Company A serves its customers with financial products,
Company A is a global company based in the United States that operates in the financial industry. Company A serves its customers with financial products, such as checking accounts, bank cards, and investment products. Company A has recently acquired Company B and needs to integrate with or remove similar capabilities and tools from Company B. Company B is smaller in size, has no dedicated cybersecurity professional role, and utilizes third-party support for infrastructure needs. Company B offers specialized software to medical providers and accepts credit cards as a payment option.
The executives of the newly merged company have expressed interest in integrating the use of the cloud to allow for scalability and redundancy. As the security professional of the merged networks, you are tasked with creating a secure network design that includes the use of zero trust principles and that utilizes both on-premises and cloud infrastructure. You also have been tasked with ensuring compliance with all regulatory requirements of the merged company, along with utilizing cloud-based technologies to provide security capabilities. Company executives have provided a budget of $50,000 in the first year to create a secure network design to utilize cloud-based services.
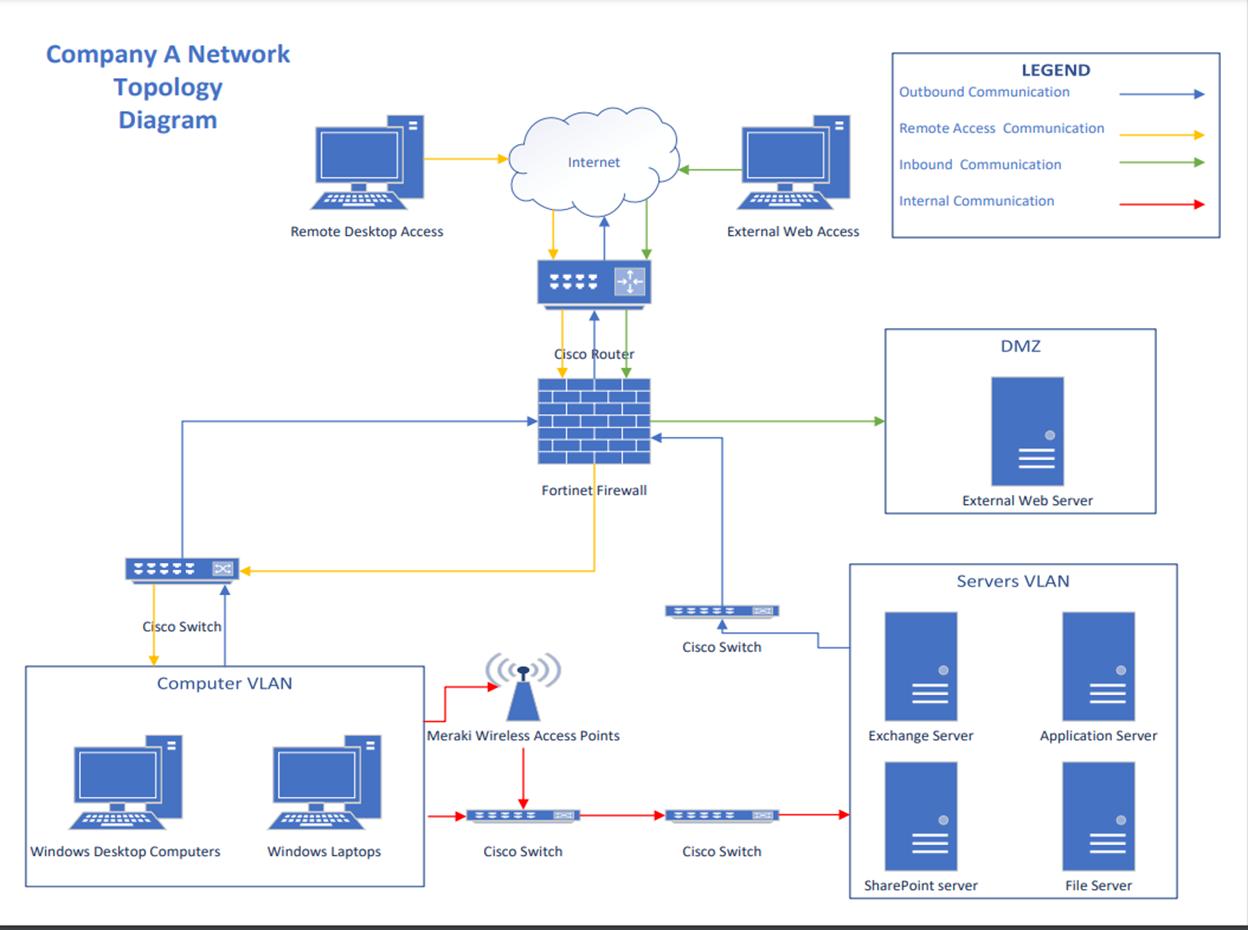
C. Create a network topology diagram with details of the proposed merged network requirements.
E. Explain the rationale for adding, deleting, or repurposing network components in the newly merged network topology diagram, including details of how each component addresses budgetary constraints.
G. Explain how the proposed merged network topology diagram addresses two regulatory compliance requirements that are relevant to the newly merged company, including the following in your explanation:
• the name of the regulatory compliance requirement
• why the regulatory requirement is relevant to the newly merged company
• how the proposed merged network topology diagram meets the regulatory requirement
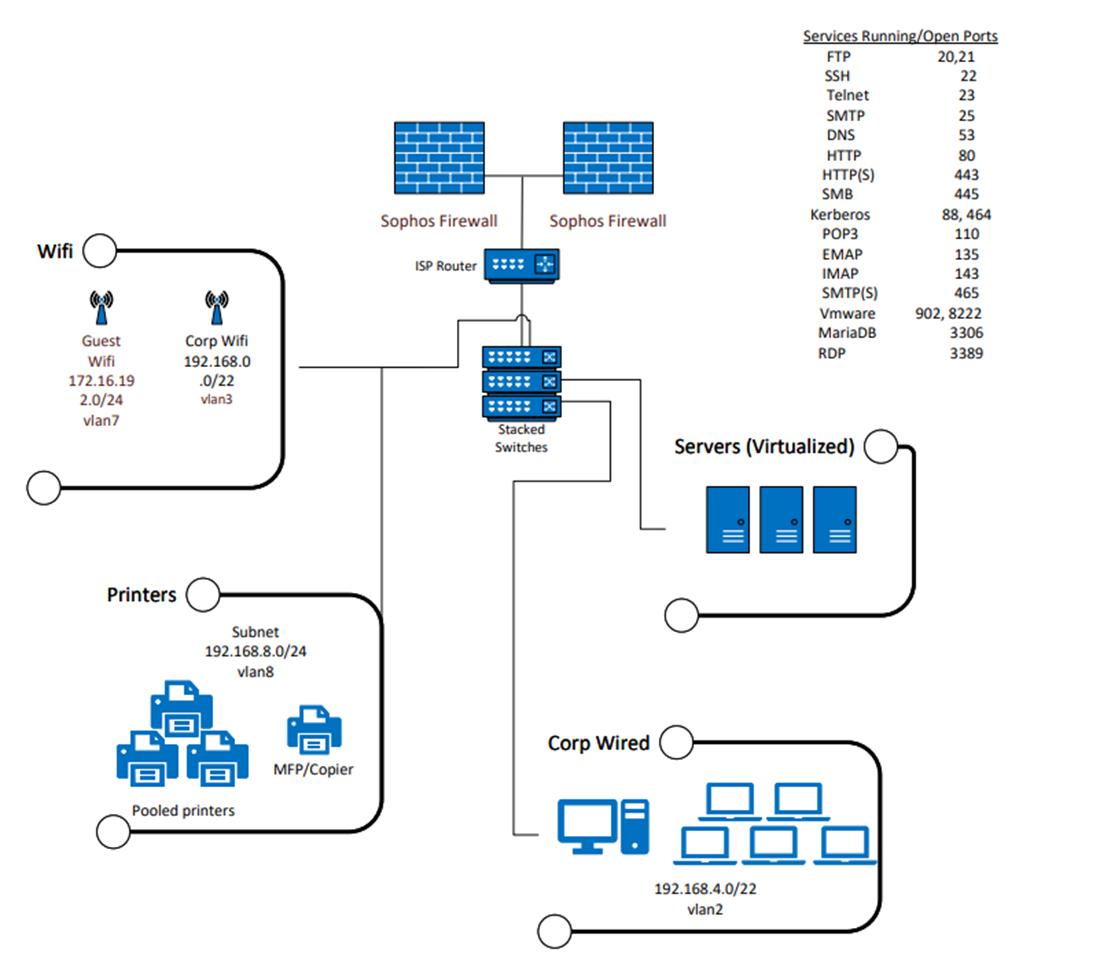
Wifi Guest Wifi 172.16.19 2.0/24 vlan7 Printers Corp Wifi 192.168.0 .0/22 vian3 Subnet 192.168.8.0/24 vlan8 Pooled printers MFP/Copier Sophos Firewall ISP Router Sophos Firewall X Stacked Switches Corp Wired Services Running/Open Ports 20,21 FTP SSH 22 23 192.168.4.0/22 vlan2 Telnet SMTP DNS HTTP HTTP(S) SMB Kerberos POP3 EMAP IMAP SMTP(S) Vmware MariaDB RDP Servers (Virtualized) 25 53 80 443 445 88, 464 110 135 143 465 902, 8222 3306 3389
Step by Step Solution
3.53 Rating (156 Votes )
There are 3 Steps involved in it
Step: 1
To address this scenario we need to create a secure merged network topology diagram and provide explanations for revisions and regulatory compliance N... View full answer

Get step-by-step solutions from verified subject matter experts
100% Satisfaction Guaranteed-or Get a Refund!
Step: 2Unlock detailed examples and clear explanations to master concepts

Step: 3Unlock to practice, ask and learn with real-world examples

See step-by-step solutions with expert insights and AI powered tools for academic success
-
 Access 30 Million+ textbook solutions.
Access 30 Million+ textbook solutions.
-
 Ask unlimited questions from AI Tutors.
Ask unlimited questions from AI Tutors.
-
 Order free textbooks.
Order free textbooks.
-
 100% Satisfaction Guaranteed-or Get a Refund!
100% Satisfaction Guaranteed-or Get a Refund!
Claim Your Hoodie Now!

Study Smart with AI Flashcards
Access a vast library of flashcards, create your own, and experience a game-changing transformation in how you learn and retain knowledge
Explore Flashcards





