Answered step by step
Verified Expert Solution
Question
1 Approved Answer
Consider the following network> Answer the questions about static, floating static, host, and default routes. a) b) c) PC1 * 172.16.1.0/24 172.16.2.0/24 172.16.3.0/24 SODO
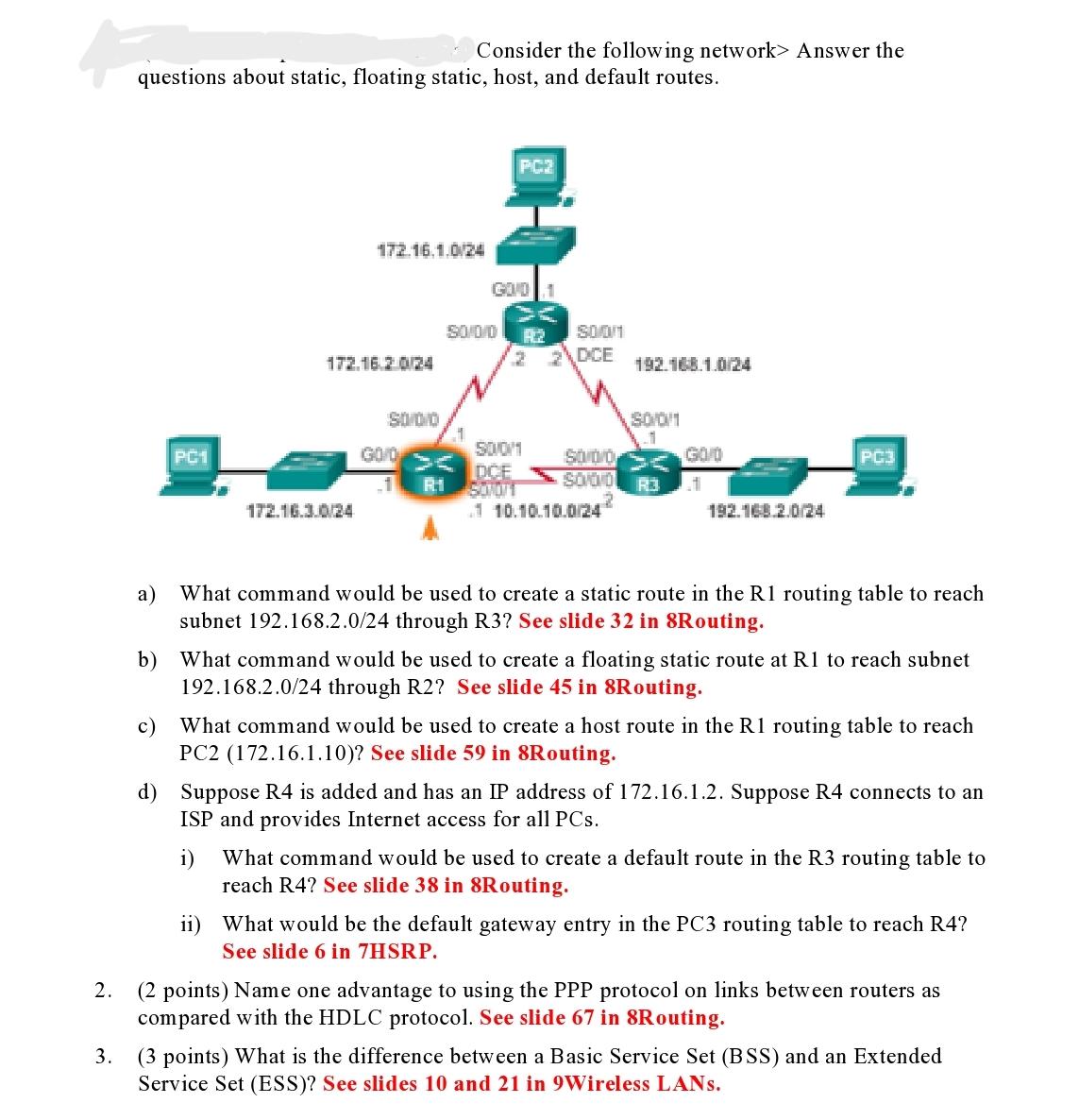
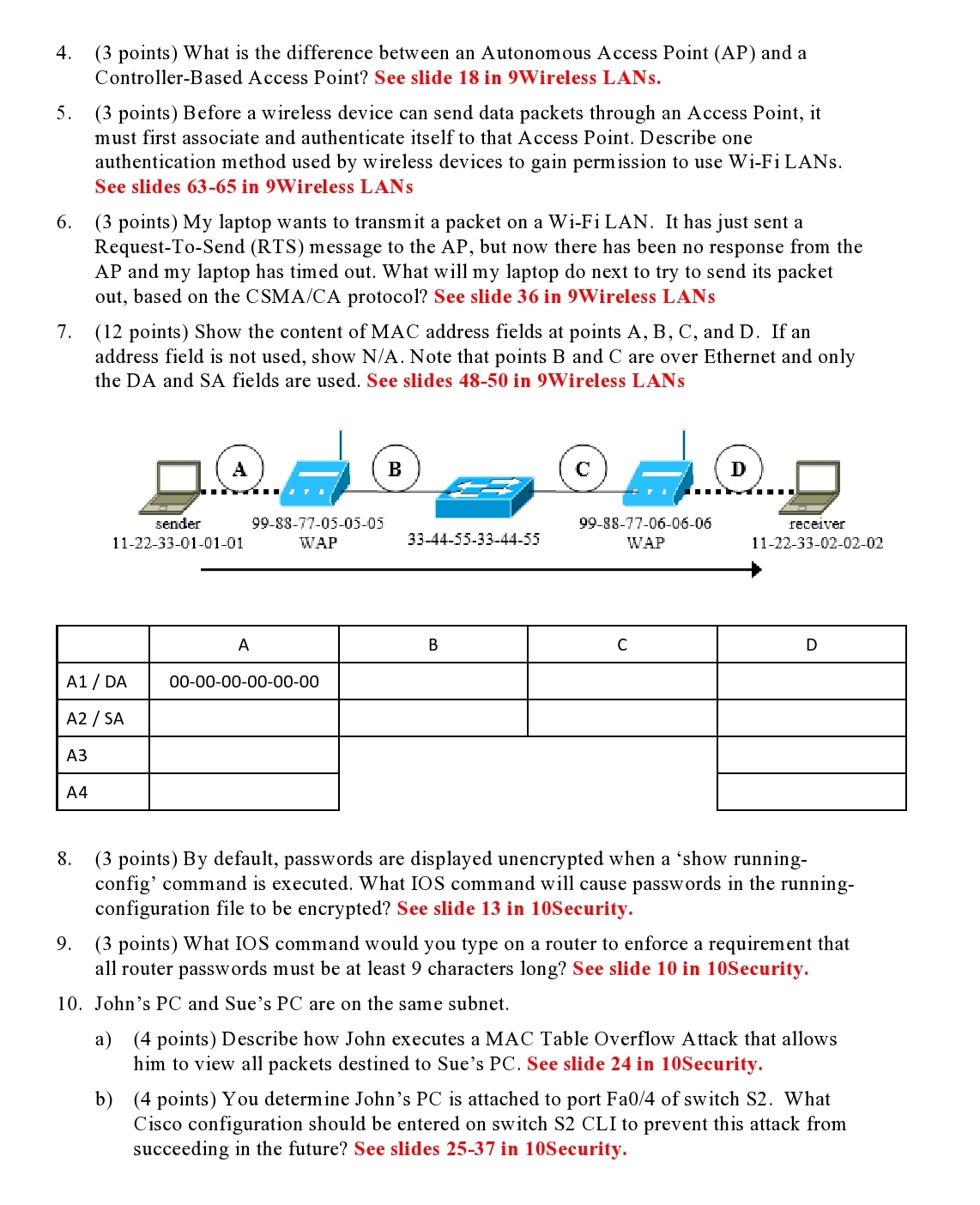
Consider the following network> Answer the questions about static, floating static, host, and default routes. a) b) c) PC1 * 172.16.1.0/24 172.16.2.0/24 172.16.3.0/24 SODO GO/O GOD 1 50/0/0 50/0/1 DCE R.1 SON01 Soon DCE 192.168.1.0/24 1 10.10.10.0/24 SOOM 1 SO/0/0 SOOD R3 G0/0 t 192.168.2.0/24 PC3 What command would be used to create a static route in the R1 routing table to reach subnet 192.168.2.0/24 through R3? See slide 32 in 8Routing. What command would be used to create a floating static route at R1 to reach subnet 192.168.2.0/24 through R2? See slide 45 in 8Routing. What command would be used to create a host route in the R1 routing table to reach PC2 (172.16.1.10)? See slide 59 in 8Routing. d) Suppose R4 is added and has an IP address of 172.16.1.2. Suppose R4 connects to an ISP and provides Internet access for all PCs. i) What command would be used to create a default route in the R3 routing table to reach R4? See slide 38 in 8Routing. ii) What would be the default gateway entry in the PC3 routing table to reach R4? See slide 6 in 7HSRP. 2. (2 points) Name one advantage to using the PPP protocol on links between routers as compared with the HDLC protocol. See slide 67 in 8Routing. 3. (3 points) What is the difference between a Basic Service Set (BSS) and an Extended Service Set (ESS)? See slides and 21 in 9Wireless LANs. 4. (3 points) What is the difference between an Autonomous Access Point (AP) and a Controller-Based Access Point? See slide 18 in 9Wireless LANs. 5. (3 points) Before a wireless device can send data packets through an Access Point, it must first associate and authenticate itself to that Access Point. Describe one authentication method used by wireless devices to gain permission to use Wi-Fi LANS. See slides 63-65 in 9Wireless LANS 6. (3 points) My laptop wants to transmit a packet on a Wi-Fi LAN. It has just sent a Request-To-Send (RTS) message to the AP, but now there has been no response from the AP and my laptop has timed out. What will my laptop do next to try to send its packet out, based on the CSMA/CA protocol? See slide 36 in 9Wireless LANs 7. (12 points) Show the content of MAC address fields at points A, B, C, and D. If an address field is not used, show N/A. Note that points B and C are over Ethernet and only the DA and SA fields are used. See slides 48-50 in 9Wireless LANS A4 A1 / DA A2 / SA A3 A TI sender 11-22-33-01-01-01 A 99-88-77-05-05-05 WAP 00-00-00-00-00-00 B 33-44-55-33-44-55 B C 99-88-77-06-06-06 WAP C D receiver 11-22-33-02-02-02 D 8. (3 points) By default, passwords are displayed unencrypted when a 'show running- config' command is executed. What IOS command will cause passwords in the running- configuration file to be encrypted? See slide 13 in 10Security. 9. (3 points) What IOS command would you type on a router to enforce a requirement that all router passwords must be at least 9 characters long? See slide 10 in 10Security. 10. John's PC and Sue's PC are on the same subnet. a) (4 points) Describe how John executes a MAC Table Overflow Attack that allows him to view all packets destined to Sue's PC. See slide 24 in 10Security. b) (4 points) You determine John's PC is attached to port Fa0/4 of switch S2. What Cisco configuration should be entered on switch S2 CLI to prevent this attack from succeeding in the future? See slides 25-37 in 10Security.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


