Answered step by step
Verified Expert Solution
Question
1 Approved Answer
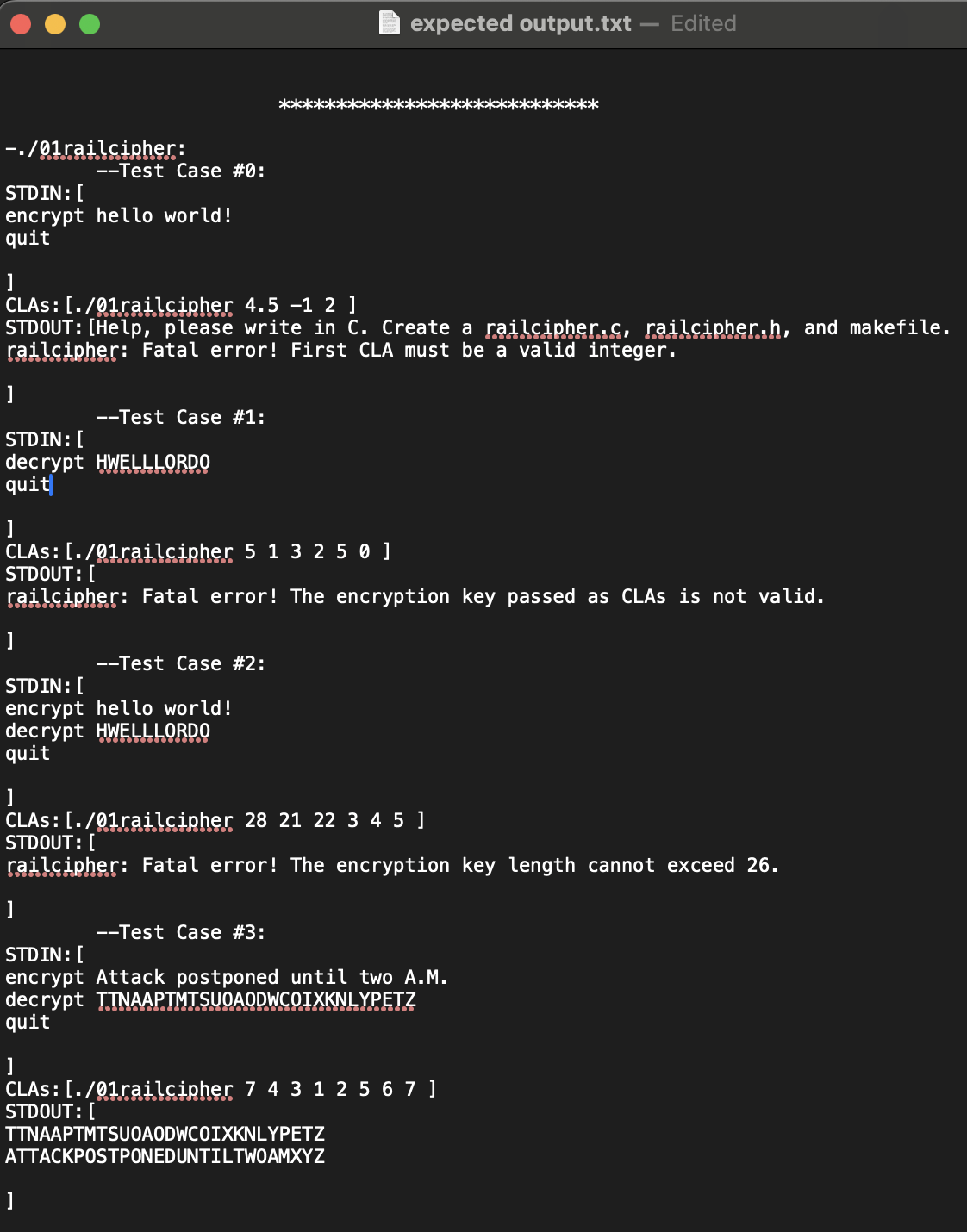
Help, please! What's wrong with my C code? It isn't working. Can you write the correct decryption and encryption logic? And include the railcipher.c ,
Help, please! What's wrong with my C code? It isn't working. Can you write the correct decryption and encryption logic? And include the railcipher.c railcipher.h and makefile. The screen shot at the end is what the 'Expected Outcome' should be once you compile and run the code the cipher text as shown in the screen shot is supposed to be converted to uppercase: #include "railcipher.h
#include
#include
#include
#include
#define MAXTEXTLENGTH
#define MAXKEYLENGTH
int mainint argc, char argv
Array to store encryption key
int keyMAXKEYLENGTH;
Validate the encryption key provided as commandline arguments
int keyLength validateKeyargc argv, key;
If key validation fails, exit the program
if keyLength
return ;
Buffers to store user input command and result
char commandMAXTEXTLENGTH resultMAXTEXTLENGTH;
Prompt user for command
printfEnter command encryptdecryptquit: ;
Loop to read commands until the user enters "quit"
while fgetscommand sizeofcommand stdin
Remove trailing newline
commandstrcspncommand
;
If user enters "quit", exit the loop
if strncmpcommand "quit",
break;
else
Process user command
processCommandcommand key, keyLength, result;
Print the result
printfs
result;
Prompt user for next command
printfEnter command encryptdecryptquit: ;
return ;
Function to validate the encryption key provided as commandline arguments
int validateKeyint argc, char argv int key
Check if sufficient commandline arguments are provided
if argc
printfUsage: s
argv;
return ;
Extract key length from commandline arguments
int keyLength atoiargv;
Check if key length is within acceptable bounds
if keyLength keyLength MAXKEYLENGTH
printfError: Invalid key length.
;
return ;
Parse and store key elements
for int i ; i keyLength; i
keyi atoiargvi ;
Additional validation for the key elements can be added here
Validation passed, return key length
return keyLength;
Function to process user command
void processCommandconst char command const int key int keyLength, char result
Buffer to store text extracted from command
char textMAXTEXTLENGTH;
Attempt to extract command and associated text from input
if sscanfcommand "encrypt s text
If command is "encrypt", call encryption function
encrypttext key, keyLength, result;
else if sscanfcommand "decrypt s text
If command is "decrypt", call decryption function
decrypttext key, keyLength, result;
else
If command is unrecognized, set result to error message
strcpyresult "Invalid command. Please enter 'encrypt', 'decrypt', or 'quit'.";
Function to perform rail fence cipher encryption
void encryptconst char matrix int rows, const int key, char ciphertext
int index ;
for int k ; k ; k
int col keyk;
for int i ; i rows; i
ciphertextindex touppermatrixicol;
ciphertextindex;
void decryptconst char ciphertext, int rows, const int key, char plaintext
char matrixrows;
int colLength strlenciphertext rows;
for int k ; k colLength; k
int col keyk;
for int i ; i rows; i
matrixicol tolowerciphertexti colLength k;
int index ;
for int i ; i rows; i
for int j ; j colLength; j
plaintextindex matrixij;
plaintextindex;
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


