Answered step by step
Verified Expert Solution
Question
1 Approved Answer
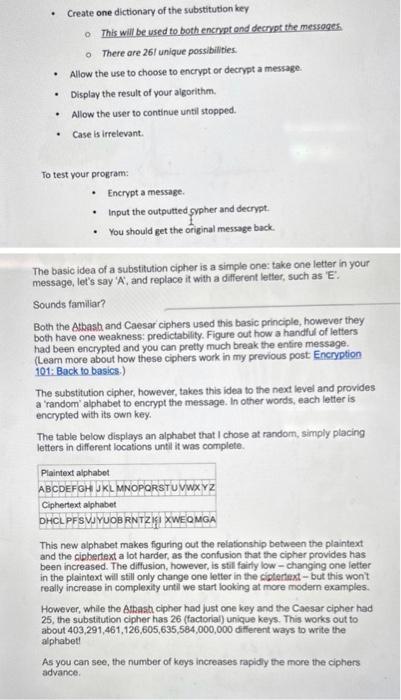
IN PYTHON PLEASE!!! CANNOT USE DEF FUNCTION!! LIST AND DICTS ETC ALLOWED From what I'm seeing you can use any cypher of your choosing as
IN PYTHON PLEASE!!!
CANNOT USE DEF FUNCTION!!
LIST AND DICTS ETC ALLOWED
From what I'm seeing you can use any cypher of your choosing as long as we can type it in. Make sure to include input validation for the encrypting part tho!!
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


