Answered step by step
Verified Expert Solution
Question
1 Approved Answer
please help me in securtity please 3 . 6 Task 6 : Manually Verifying an X . 5 0 9 Certificate In this task, we
please help me in securtity please Task : Manually Verifying an X Certificate
In this task, we will manually verify an X certificate using our program. An X contains data about a public key and an issuer's signature on the data. We will download a real X certificate from a web server, get its issuer's public key, and then use this public key to verify the signature on the certificate.
Step : Download a certificate from a real web server. We use the
wwwexample.org server in this document. Students should choose a different web server that has a different certificate than the one used in this document it should be noted that
wwwexample.com share the same certificate with www
example.org We can download certificates using browsers or use the following command:The result of the command contains two certificates. The subject field the entry starting with s: of the certificate is wwwexample.org, ie this is wwwexample.org's certificate. The issuer field the entry starting with i: provides the issuer's information. The subject field of the second certificate is the same as the issuer field of the first certificate. Basically, the second certificate belongs to an intermediate CA In this task, we will use CA's certificate to verify a server certificate.
If you only get one certificate back using the above command, that means the certificate you get is signed by a root CA Root CAs' certificates can be obtained from the Firefox browser installed in our prebuilt VM Go to the Edit Preferences Privacy and then Security View Certificates. Search for the name of the issuer and download its certificate.
Copy and paste each of the certificate the text between the line containing "Begin CERTIFICATE" and the line containing "END CERTIFICATE", including these two lines to a file. Let us call the first one pem and the second one pem.
Step : Extract the public key e n from the issuer's certificate. Openssl provides commands to extract certain attributes from the x certificates. We can extract the value of using modulus. There is no specific command to extract e but we can print out all the fields and can easily find the value of e
SEED Labs RSA PublicKey Encryption and Signature Lab
SEED Labs RSA PublicKey Encryption and Signature Lab
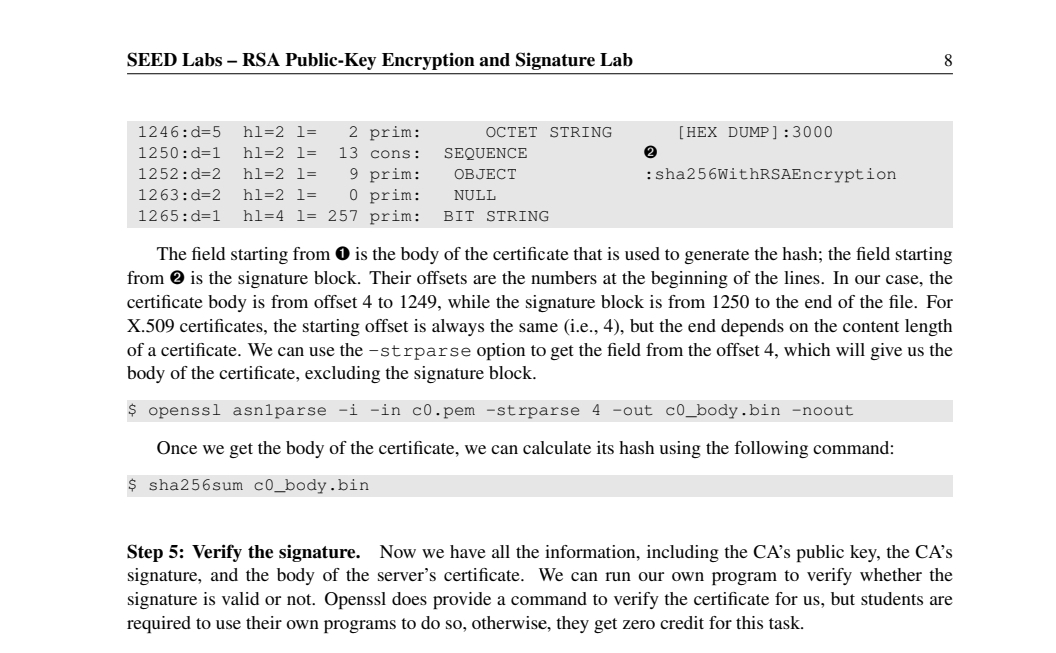
Step : Extract the signature from the server's certificate. There is no specific openss l command to extract the signature field. However, we can print out all the fields and then copy and paste the signature block into a file note: if the signature algorithm used in the certificate is not based on RSA, you can find another certificateWe need to remove the spaces and colons from the data, so we can get a hexstring that we can feed into our program. The following command commands can achieve this goal. The tr command is a Linux utility tool for string operations. In this case, the d option is used to delete : and "space" from the data.Step : Extract the body of the server's certificate. A Certificate Authority CA generates the signature for a server certificate by first computing the hash of the certificate, and then sign the hash. To verify the signature, we also need to generate the hash from a certificate. Since the hash is generated before the signature is computed, we need to exclude the signature block of a certificate when computing the hash. Finding out what part of the certificate is used to generate the hash is quite challenging without a good understanding of the format of the certificate.X certificates are encoded using the ASN. Abstract Syntax Notation.One standard, so if we can parse the ASN. structure, we can easily extract any field from a certificate. Openssl has a command called asnparse used to extract data from ASN. formatted data, and is able to parse our X certificate.
SEED Labs RSA PublicKey Encryption and Signature Lab
:shaWithRSAEncryption
The field starting from is the body of the certificate that is used to generate the hash; the field starting from is the signature block. Their offsets are the numbers at the beginning of the lines. In our case, the certificate body is from offset to while the signature block is from to the end of the file. For X certificates, the starting offset is always the same ie but the end depends on the content length of a certificate. We can use the strparse option to get the field from the offset which will give us the body of the certificate, excluding the signature block.
$ openssl asnparse i in cpem strparse out cbody.bin noout
Once we get the body of the certificate, we can calculate its hash using the following command:
$ shasum cbody.bin
Step : Verify the signature. Now we have all the
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


