Question
Please help me with these questions based on this paper since I'm short of time. 1. What is the ethical issue/problem in one sentence? State
Please help me with these questions based on this paper since I'm short of time.
1. What is the ethical issue/problem in one sentence? State this in the form of an ethical question an IT practitioner would need to consider.
2. What facts have the most bearing on the ethical decision you must render in this case? Note: facts do not include ethical judgments at this point.
3. Are there any other external or internal factors to be considered? (Economic, political, etc.)
4. Who are the claimants, and in what way are you obligated to each of them? (List all affected by your decision.)
Introduction
Identifying security threats in the digital world is a critical issue and requires thorough knowledge of security-based technologies [1]. There are various forms of security that can be discussed within organizations and companies, including computer security, information security, cyber security, etc. [2]. Generally, information security refers to the preservation of particulars and information, as well as the systems and hardware that are employed to use, preserve, and communicate those particulars and information [3]. It is important to understand that information security is both a process and a product [4].
Whatever the case may be, information security is not an undisputed idiom [5]. There are few distinctions between cyber security and information security in the documentation or a correlation between the two. The concept of "information security" can prove to be an imperative matter for Small and Medium Businesses (SMEs) and is commonly referred to as cyber security [6].
It is increasingly difficult for organizations to protect themselves from potential cyberattacks [7]. Cyber security is defined by the International Telecommunications Union (ITU) as follows:
The term "cyber security" refers to a collection of tools, strategies, security concepts, suggestions, measures, instructions, and technologies that may be helpful in safeguarding a company's digital environment, users, and data. Global attention and significance are being accorded to cyber security [8]. Cybercrime is committed at a rate of 72% by Small and Medium Enterprises (SMEs). As a result, SMEs require security services at some levels [9]. The primary objective of IT security is to protect networked computer resources and assets [10]. As a means of combating cyber-attacks, cyber security advocates encourage using security applications and acquiring security technology.
The idea of cybersecurity is based on computing and combines human and process resources to ensure "Assured Operation" in the presence of challenges and threats. As a matter of financial and national security, cybersecurity has become one of the most serious issues [12]. The internet is a safe and resourceful place for those wishing to pursue criminal hobbies due to its phantasm, and sometimes reality, of anonymity. The modern World Wide Web (sometimes referred to as "internet 2.0") allows a variety of activities, including cyberstalking (13).
A DoS transmission can also be used to spoof remote records from random sources. An attacker should assemble malicious message streams to shape any subscriber activity that could be forwarded to the DCS service event for disclosure. Subsequent subscribers could then unknowingly receive the malicious packets via trusted DCS event services. The 2007 cyberattacks on Estonia involved DDoS attacks that crippled the country's banks and parliament. The technology of DDoS attacks evolved to a level of sophistication unprecedented in the era of ping floods and botnets. Researchers and naval planners agree that the coaching underlying DDoS attacks are the second largest example of state-sponsored cyberwarfare [14].
During a hit attack, the loss to the victim (the city and its citizens) and the advantage to the hacker may be asymmetric, with the loss exceeding the advantage in many cases [15]. In a 12-month study conducted by the Russian data protection certification system, approximately one-third of the software components examined exhibited vulnerabilities at some point. This vulnerability might be caused by an intentional or unintentional code flaw and does not appear to be malicious in nature [17].
Instead of creating complete PC systems, most developers focus on verifying smaller, vulnerable, or significant portions of a system. The state of cybersecurity will remain weak as long as those individuals remain unaware of their role in enhancing cybersecurity [18].
Based on the survey conducted by Symantec, which interviewed 20,000 people in 24 countries, 69% mentioned being the victim of a cyberattack in their lifetime. Each of those 14 adults is the victim of a cyberattack every second. This is more than a million attacks every day, no matter where they live or how far they live [19].
The international availability of the Internet permits cybercriminals to launch attacks on each machine from anywhere, at any place, at any time. Nevertheless, one of the most challenging and complex elements of cybersecurity is its constantly evolving nature. Due to this, cyberattacks have become more capable of unfolding in a matter of seconds [20].
To address cybersecurity issues/challenges, a research question is formulated:
RQ1. What are the cyber security issues faced by vendor organizations in software development that have a negative impact on the software industry?
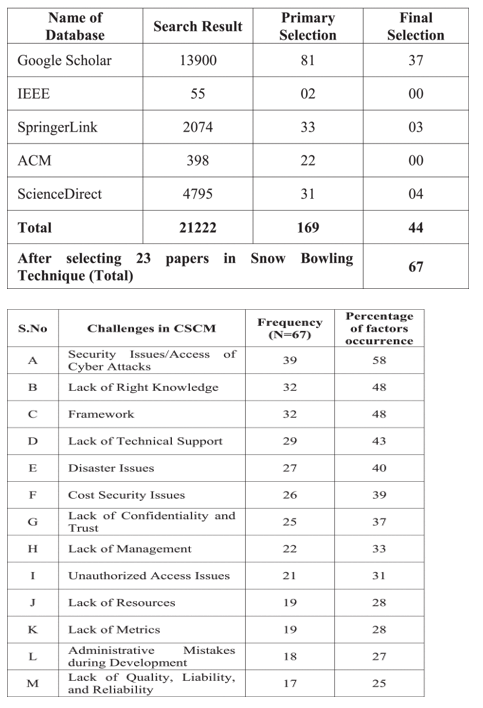
From the final selection of 67 research articles for the proposed SLR study, we identified 13 critical cybersecurity challenges. Despite the differences between the identified critical cybersecurity challenges in different periods, continents, organizations, databases, and methods, the results confirm their resemblances.
Methodology
A predefined search string is used in SLR to find relevant compositions based on the study questions. For the analysis of the collected data, a predefined criterion of SLR was used for insertion/removal. According to Kitchenham [21], a systematic literature review (SLR) consists of three phases, namely planning, conducting, and reporting. Since SLR mimics an organized evaluation process, its results are more trustworthy than those of a traditional literature search. To identify cybersecurity issues/challenges, SLR follows a step-by-step process. This process evaluates the relevance of a paper to the topic or search term. We applied an inclusion/exclusion criterion to our selected research papers to exclude irrelevant articles. Then, relevant data are extracted from the selected articles through the data extraction process and the evaluation of the publication process is performed. This article aims to highlight all cybersecurity issues/challenges using SLR that vendor organizations face during software development.
Through SLR, we found thirteen (13) critical issues/obstacles, as shown in Table 2, those vendor organizations face in software development in the form of cybersecurity, and these challenges are identified through SLR.
A. Search Process
We proceed as follows to create the search string for SLR. - Identify outcomes, population, and intervention for a search term. - Identification of synonym words for the search term. - Validating and checking keywords in the relevant literature. - Using Boolean operators for accurate output.
First, on a trial basis, a search string is developed that can be applied in various digital libraries/search engines to recognize the relevant research papers. The trial visits were conducted in five databases/search engines, namely Google Scholar, ACM, IEEE Explore, SpringerLink, and ScienceDirect. The trial visits collect different results from different databases, but their accuracy is lower. The search string is given below:
(("software development") AND ("cybersecurity") AND (vendors) AND (challenges) AND (practices))
The results of the trial visits were not satisfactory, so we developed a final search.
The final search string above was too short for ScienceDirect to find relevant articles because ScienceDirect does not support long strings. The final search string for ScienceDirect is as follows: (("software development" OR "software evolution" OR "software maturing") AND ("cybersecurity" OR "cyber risks" OR "IT security") AND (supplier OR trader) AND (issues OR problems)).
The results of the search for related articles are obtained by applying the search string shown in Table 1. An inclusion/exclusion criterion was used for the final selection of research papers, as shown in Table 1. In this process, we selected the relevant articles based on the quality of the work and reviewed them by reading.
\begin{tabular}{|l|c|c|c|} \hline \multicolumn{1}{|c|}{NameofDatabase} & Search Result & PrimarySelection & FinalSelection \\ \hline Google Scholar & 13900 & 81 & 37 \\ \hline IEEE & 55 & 02 & 00 \\ \hline SpringerLink & 2074 & 33 & 03 \\ \hline ACM & 398 & 22 & 00 \\ \hline ScienceDirect & 4795 & 31 & 04 \\ \hline Total & 21222 & 169 & 44 \\ \hline AfterselectingTechnique(Total) & papers in Snow & Bowling & 67 \\ \hline \end{tabular} \begin{tabular}{|c|l|c|c|} \hline S.No & \multicolumn{1}{|c|}{ Challenges in CSCM } & Frequency(N=67) & Percentageoffactorsoccurrence \\ \hline A & SecurityIssues/AccessofCyberAttacks & 39 & 58 \\ \hline B & Lack of Right Knowledge & 32 & 48 \\ \hline C & Framework & 32 & 48 \\ \hline D & Lack of Technical Support & 29 & 43 \\ \hline E & Disaster Issues & 27 & 40 \\ \hline F & Cost Security Issues & 26 & 39 \\ \hline G & LackofConfidentialityandTrust & 25 & 37 \\ \hline H & Lack of Management & 22 & 33 \\ \hline I & Unauthorized Access Issues & 21 & 31 \\ \hline J & Lack of Resources & 19 & 28 \\ \hline K & Lack of Metrics & 19 & 28 \\ \hline L & AdministrativeduringDevelopment & 18 & 27 \\ \hline M & LackofQuality,Liability,andReliability & 17 & 25 \\ \hline \end{tabular}Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


