Answered step by step
Verified Expert Solution
Question
1 Approved Answer
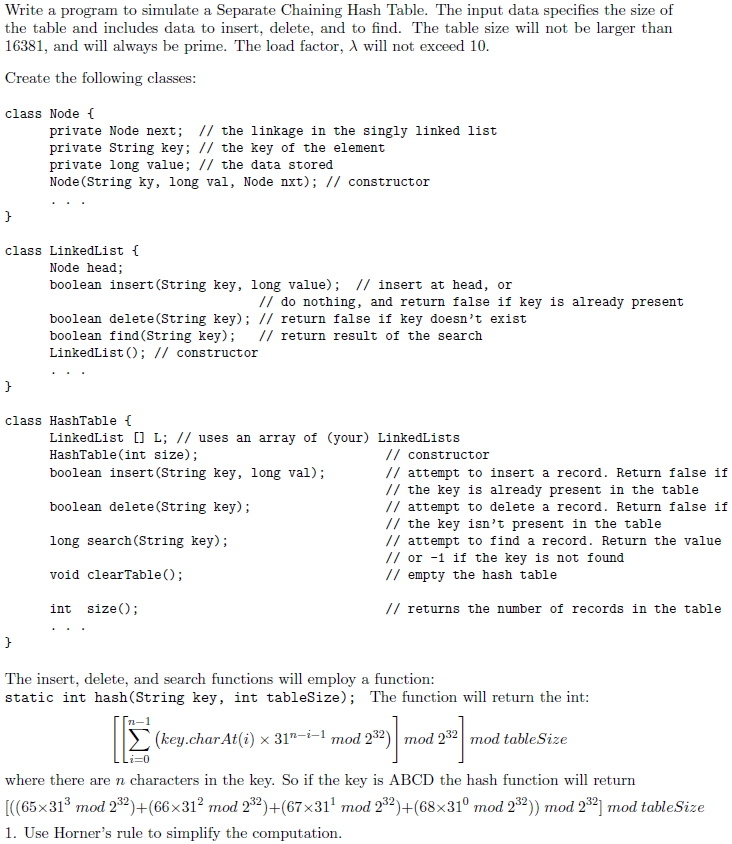
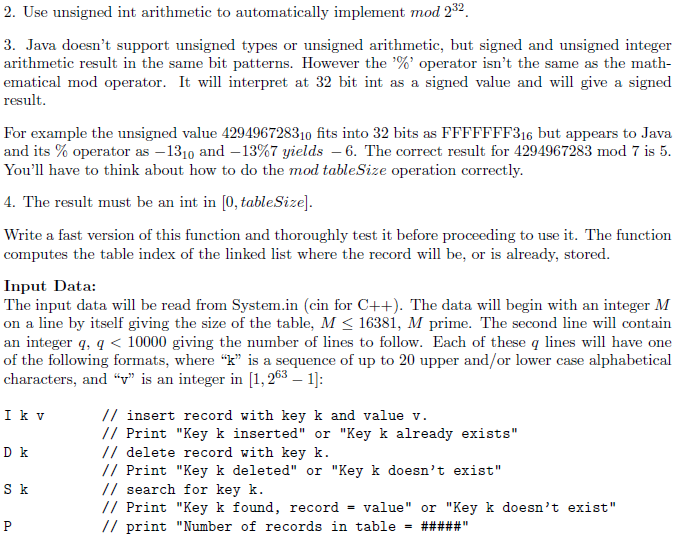
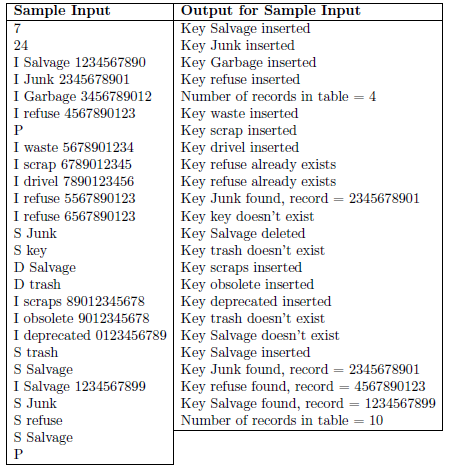
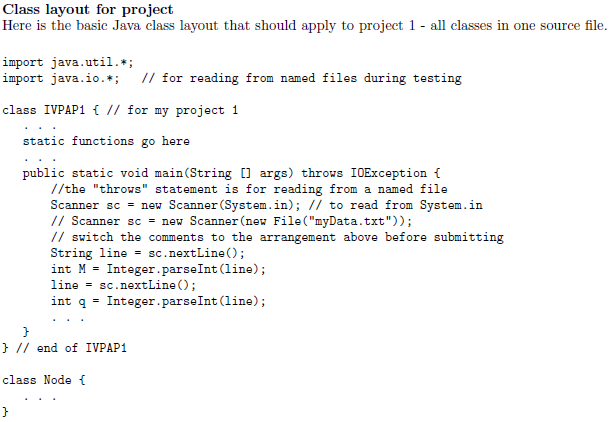
Write a program to simulate a Separate Chaining Hash Table. The input data specifies the size of the table and includes data to insert, delete,
Write a program to simulate a Separate Chaining Hash Table. The input data specifies the size of the table and includes data to insert, delete, and to findnd. The table size will not be larger than 16381, and will always be prime. The load factor, will not exceed 10.
**The examples are in Java but i want this in C++.
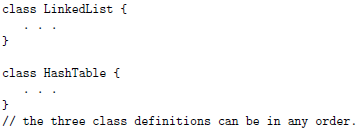
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


