Question
Question 1. The actions of the hacktivist group 'Anonymous' illustrate..... Select the correct response(s): a) .....how modern hactivist groups have been deterred from targeting lager
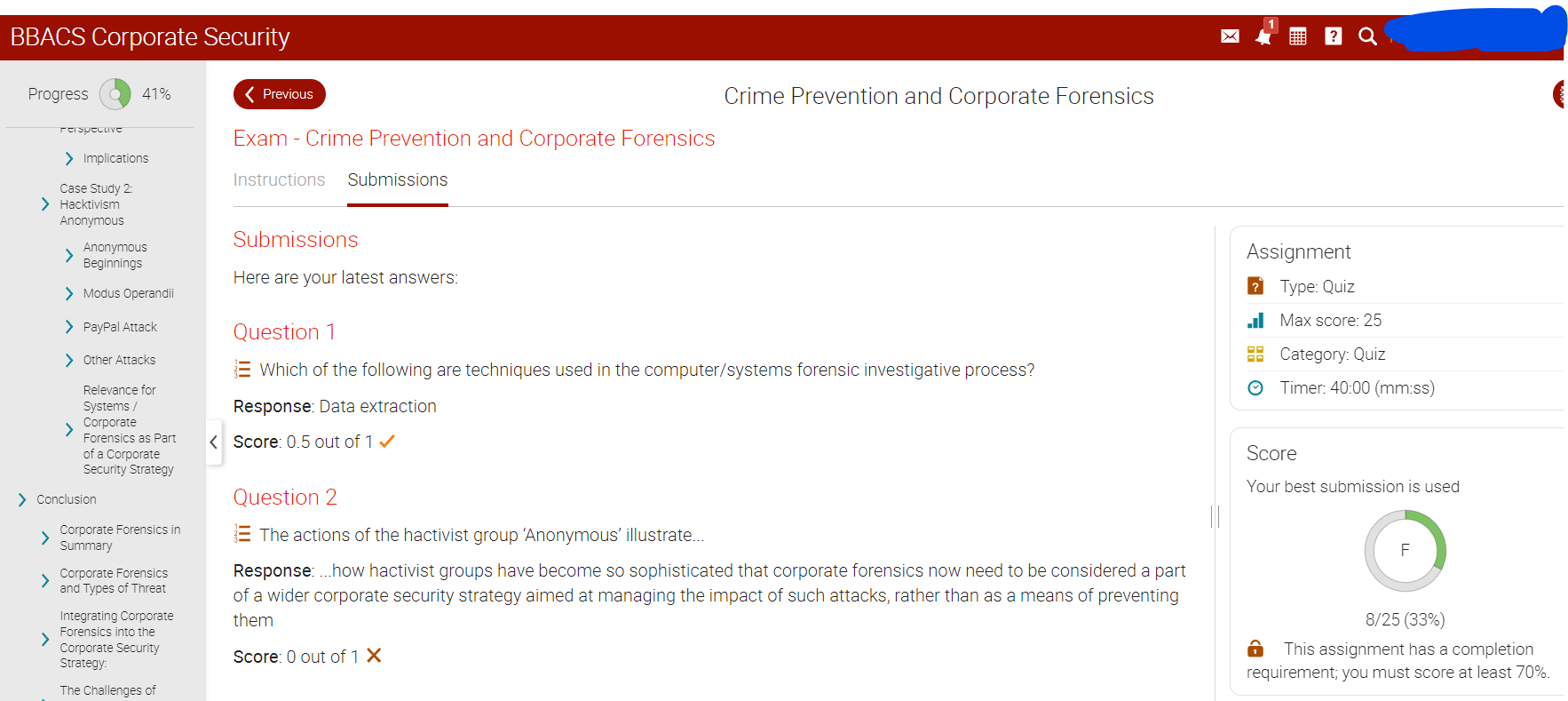
Question 1.
The actions of the hacktivist group 'Anonymous' illustrate.....
Select the correct response(s):
a) .....how modern hactivist groups have been deterred from targeting lager organisations in favour of smaller, less technologically sophisticated firms which might not be able to afford to integrate corporate forensics into their security strategies.
b) .....how the dynamic in the international security environment in general is shifting away from physical attacks on civilians to cyber attacks on commercial organisations by 'stateless' virtual networks.
c) ....how hactivist groups have become so sophisticated that corporate forensics now need to be considered a part of a wider corporate security strategy aimed at managing the impact of such attacks, rather than as a means of preventing them.
d) .... why corporate forensics, in and of itself, is insufficient to protect organisations from potential cyber-threats, and needs to be integrated into part of a wider and more comprehensive corporate security strategy.
e).....how members of modern, loosely networked online collectives are becoming ever more technologically sophisticated and talented, but also harder to identify and track down.
Step by Step Solution
There are 3 Steps involved in it
Step: 1

Get Instant Access to Expert-Tailored Solutions
See step-by-step solutions with expert insights and AI powered tools for academic success
Step: 2

Step: 3

Ace Your Homework with AI
Get the answers you need in no time with our AI-driven, step-by-step assistance
Get Started


