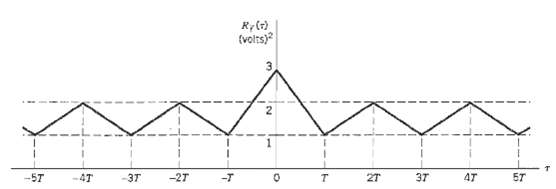
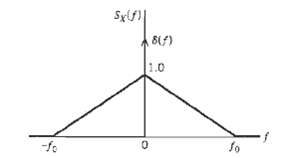
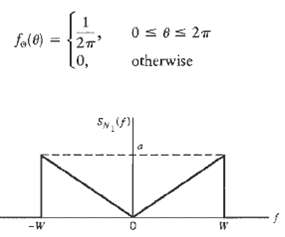
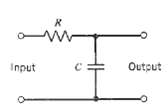
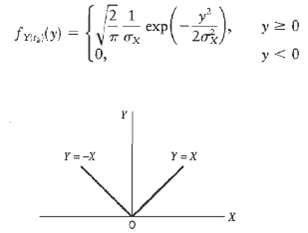
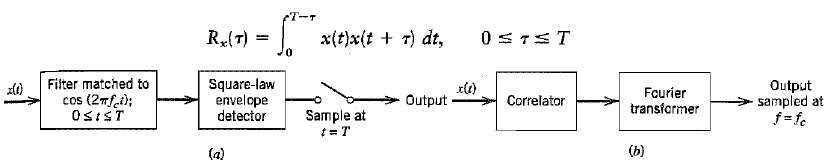
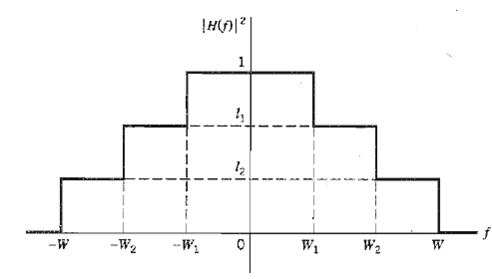
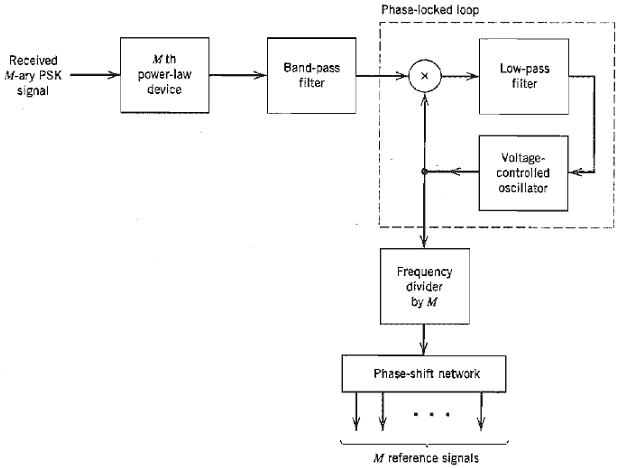
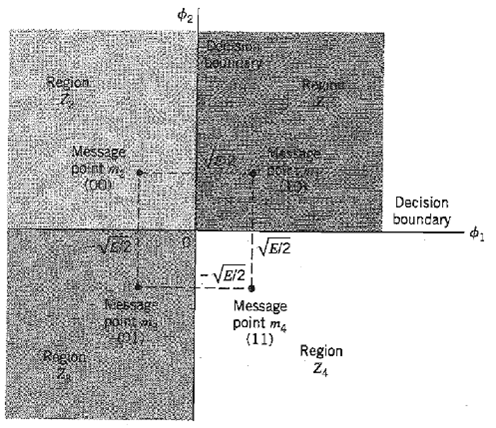
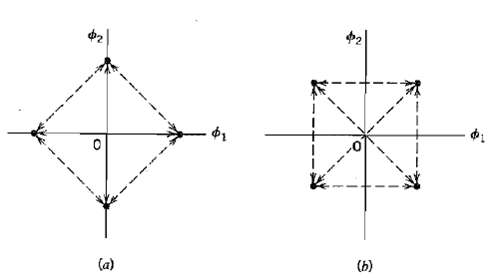
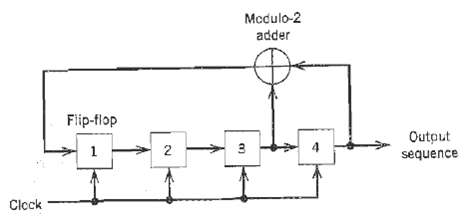
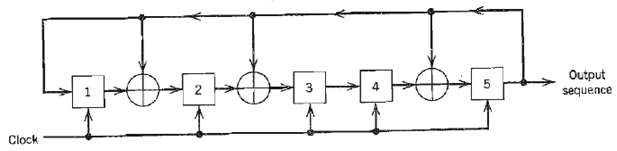
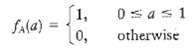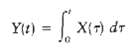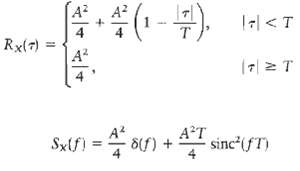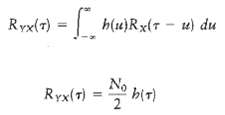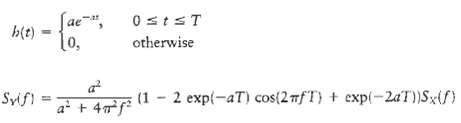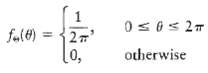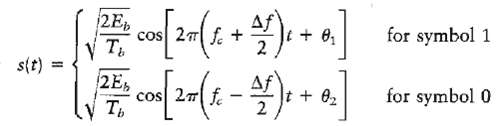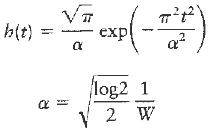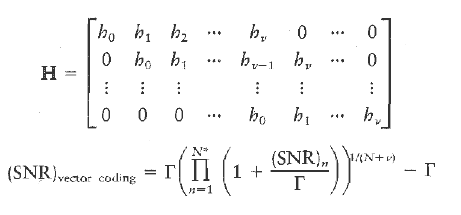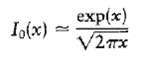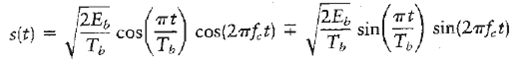Communication Systems 4th Edition Simon Haykin - Solutions
Discover the comprehensive solutions for "Communication Systems 4th Edition" by Simon Haykin. Access an extensive collection of questions and answers, designed to offer a deeper understanding of key concepts. Our solution manual and answers key provide step-by-step answers to complex problems, making learning more accessible. Delve into the instructor manual and chapter solutions for detailed insights. Utilize our test bank for exam preparation with solved problems. Download the solutions PDF for free and explore the textbook's intricacies. Enhance your knowledge with this valuable resource, available online for effortless access.
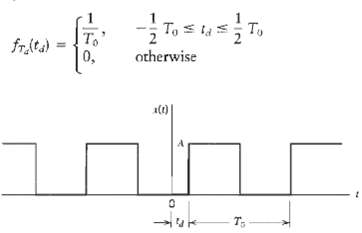
![]()
![]() New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
New Semester Started
Get 50% OFF
Study Help!
--h --m --s
Claim Now
![]()
![]()